How to Be Anonymous Online: 19 Tips to Protect Your Identity
The Internet is rife with viruses, spies and other instruments lurking about. After getting online, you make your personal details visible to a large number of individuals who include your Internet company, online advertisers, and government officials. Whenever you logout on cookies on a site, create a post on your social media, or simply accept privacy terms without reading them, data collection takes place and your information may be stored or exchanged. So, can one surf the web anonymously and protect their online identity? Continue reading to discuss the important practices and useful hints on how to be anonymous online.

Can you be completely anonymous online?
First, let’s answer the most burning question — does anonymity online even exist?
In theory, it’s possible to become truly anonymous online. But staying anonymous constantly is a way more challenging task. That would require significant effort. You will have to totally redefine your habits of browsing, your behavior and attitude towards what you post (or do not post) over the internet.
They can be some illustrations of individuals who remain non-identified, such as the street artist Banksy or the creator of Bitcoin Satoshi Nakamoto (those instances are rather exceptional, however).
At the same time, many still confuse going completely incognito and simply protecting their personal information online. In fact, while anonymity and privacy are closely related, there’s a drastic difference between these two concepts. Here are some details.
Anonymity vs. privacy: The difference explained
The ability to control what information you post on the Internet, to keep off the uninvited surveillance, and to ensure that your personal information will not be stolen is what online privacy implies. In the vast majority of cases, it implies that you do not want to be noticed by people.
On the other hand, there is the anonymity of the internet where you would wish to be known without revealing your name. In the vast majority of cases, such a choice is made by activists, journalists, super-whistles, and artists who want to remain anonymous (the latter is often due to safety reasons).
In case you are interested in staying out of the reach of unwanted surveillance and storing your data securely, it is likely that you will be able to stay on the right side of the simplest principles of online privacy. In this case, then read our informative blog post that unveils the meaning of digital privacy and how to keep it in your daily life. However, should you really wish to conceal the identity to the best, we will shortly discuss the key steps to follow.
However is it not possible to remove your online footprint by just typing the incognito (private browsing) feature of your web browser? You can, but that will not make you an Internet ninja. Here is why.
How anonymous is incognito mode?
In private browsing mode (in Safari and Firefox) or incognito mode (in Google Chrome) or In private mode (in Microsoft Edge), is an option to make sure that your browsing history (including search history) will not be stored on your computer once you close the window. Nonetheless, nothing is left to do with real Internet anonymity.
To be more specific, let’s see what the incognito does and what it doesn’t do in terms of your privacy.
| ✅ What incognito mode does | ❌ What incognito mode doesn’t do |
| – Prevents collecting a local record of your browsing and search history – Hides your browsing data on your device from other users – Stops the creation or storage of cookies when you close the browsing window | – Doesn’t protect you from hacking attempts and malware – Doesn’t hide your browsing data from third parties, such as your employer, Internet service provider (ISP), and websites you visit – Doesn’t erase your digital footprint – Doesn’t hide your IP address and other connection details – Doesn’t secure your data on public Wi-Fi |
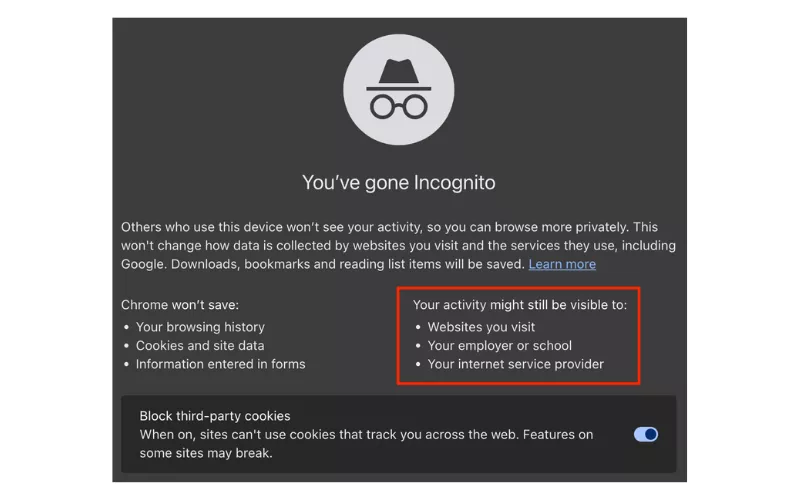
In a nutshell, the incognito mode is not sufficient to conceal you on the internet. So, what do you need to do? In the following paragraphs, we will discuss the most important measures that will enable you to hide your digital identity and ensure that no one can trace you on the internet.
19 tips on how to stay anonymous online
As stated, being an anonymous online user is a difficult task that takes a lot of efforts, not to mention a certain variety of tools, programs, and even operating systems that are needed to guarantee this notion. Following one or several of the tips described below won’t make you anonymous. Only combining them all gives you a chance of erasing your trace online. In this connection, we can consider the most important hints on how to be anonymous on the Internet.
1. Use a VPN
A virtual private network (VPN) is an online privacy and security device with a number of advantages to the users who are struggling to keep their information confidential or remain unknown on the internet. The most important benefits of VPN are the following:
- It hides your IP address. VPN mimics your IP and substitutes it with an address of an anonymous remote server.
- It encrypts your traffic. A VPN provides secure encryption and end-to-end encryption of all your Internet traffic with a few tunneling protocols to maintain a stable and secure connection.
- It prevents unwanted tracking and security risks. A VPN is a must-have tool if you don’t want anyone, including your ISP, websites, advertisers, and the government, to snoop on you online.
Note however that not every VPN is provided at such advantages. Others can even do just the reverse and this can be more harmful than good. Specifically, VPNs that are free usually log the data of customers and sell it to earn money. The solution is to choose a well-known paid VPN such as VeePN, which guarantees the following:
- A transparent No Logs policy
- AES-256 encryption
- RAM-only VPN servers
- DNS and IP leak protection
- Double VPN (runs your traffic through two remote locations for greater privacy)
2. Use the Tor browser
The Tor browser is another great item in your online anonymity toolkit. Just like VPN, The Onion Router (Tor) secures the encryption of data and conceals your IP address. It redirects your traffic via multiple autonomous nodes operated by volunteers worldwide (it is also referred to onion routing). Tor is originally intended to be used by anonymous communication between American intelligence agents, but it is a decent solution to privacy enthusiasts, human rights activists, and journalists in those countries where the Internet is heavily censored.
However, remember that tor is very slow compared to Chrome, Firefox, Safari and other regular web browsers. Besides, it should be noted that it encrypts your traffic at the browser level, whereas a VPN secures the entire traffic.
3. Use Onion over VPN
One can also use the major functions of a VPN and Tor together to have even more protection and anonymity. Onion over VPN can be used like the following:
- Download and install VeePN.
- Pick a pricing plan and subscribe.
- Activate VeePN by connecting to the preferred server location.
- Open the Tor browser and choose the Safest mode in its settings.
- Done! You’re ready to start your anonymous browsing session.
But remember that combining Tor and VPN will significantly slow down your Internet speed due to multiple data encryption layers. Use this solution only when dealing with something particularly sensitive.
4. Don’t log in to your Google account
It’s not a secret that Google collects and stores tons of customer data, mostly for advertising purposes. Once you enter your Google account, you expose many private details, including the following:
- Your precise geolocation
- Your browsing behavior and habits
- Your search history on platforms partnering with Google
- Your interactions, such as likes, comments, and more
The least you can do to cover up your data is logging out of your Google account (and remaining logged out when possible).
5. Use a private web browser
We mentioned Tor as the best encrypted browser out there. But again, it’s much slower than Chrome or Edge. So, is there a safe alternative that works slightly faster?
Although no other browser will run your traffic through multiple encrypted nodes, there are a couple of decent options to consider. In particular, Mozilla Firefox, Brave, LibreWolf, Iridium, and Ungoogled Chromium are known for their enhanced privacy and security settings. For more information, feel free to check out our detailed overview of the best Internet browsers for privacy.
6. Use a private search engine
And we have mentioned that Google is not very privacy-friendly? Although you are not required to be logged in to your Google account, the search engine itself will continue gathering some bits of information on what you are browsing. Fortunately, some of the privately owned search engines ensure that they do not subject their users to undesirable surveillance efforts. Some decent examples include DuckDuckGo, Brave Search, MetaGer, and Mojeek.
Of course, these search engines won’t provide a personalized experience as Google does, as your search results won’t be based on your online habits. But that’s the price you should pay for your anonymity.
7. Adjust your privacy settings
Digital privacy and anonymity are not limited to securing your online experience with an alternative search engine and an encrypted Internet browser. You will also have to reconfigure privacy and security settings on your devices for every application you use. Here are some basics in this regard:
- Remove all questionable apps and programs from all devices.
- Don’t install unverified software.
- Limit app permissions and location services on your mobile devices.
- Avoid allowing apps to access your location, microphone, camera, contacts, and other sensitive data that may expose your identity.
Eager to learn more? Jump into our detailed guidelines on the essential iPhone and Android privacy settings.
8. Update your software regularly
Also remember to upgrade your system and software on a regular basis. The old programs are also more susceptible to hacking attempts, since they do not have any relevant security patches among others. When a hacker succeeds in stealing your data with the help of an outdated program, he/she can disclose your actual identity or even sell it in the dark web.
9. Don’t overshare your data on social media
If you’re striving for complete anonymity, it’s not a good idea to use any social media at all. None of those platforms, including Instagram, Facebook, Twitter (X), Reddit, and TikTok, are privacy-friendly. Strangers can learn a lot from your social media page—in fact, even governments use advanced AI algorithms to analyze this information and create detailed profiles about citizens.
If you can’t quit your social media, follow these essential measures to preserve your anonymity:
❌ Don’t use your real name in your accounts.
❌ Don’t post any pictures or videos that could potentially link to your real identity and location.
❌ Don’t add your friends, family, and other people you know in real life to any groups or lists.
10. Use encrypted messaging apps
Data encryption is a crucial aspect of your journey to online anonymity. But many popular messaging applications, including Facebook Messenger, lack this protection level and thus threaten your privacy. In turn, some encrypted applications may look trustworthy yet have some significant security flaws (for instance, WhatsApp has suffered from major data breaches, while Telegram relies on its own encryption protocols instead of using proven ones).
Look for open-source messaging applications with default end-to-end encryption and additional privacy features, like no metadata collection, compliance with data protection laws, and self-destructing messages. Some decent examples of such apps are Signal, Wickr Me, and Wire. Dive into a more detailed overview of the most secure messaging apps in our blog if curious.
11. Use encrypted email services
Not only your messages, but also emails should be end-to-end encrypted. Unfortunately, just like with messaging apps, many popular email services lack this essential protection measure. So, if you send or receive something confidential, you need a safer alternative to Gmail, Yahoo! Mail, or Outlook. Encrypted email services, such as Mailbox.org, Tutanota, and ProtonMail are among the most notable options.
Also, consider using burner email accounts during registration on websites or platforms. This way, you will avoid sharing your real personal email, replacing it with a temporary address that isn’t linked to you.
12. Use an encrypted data storage
Storing your files, photos, and any other private data online can also be risky, as popular services like Google Drive, OneDrive, and iCloud aren’t 100% secure. To avoid potential leakage of your private information, look for encrypted cloud storage services, such as Sync.com or pCloud. That’s the only way to make sure that even if somebody manages to break in, they will only see gibberish text instead of real data.
13. Block cookies
Cookies are small pieces of data that track your activity when you land on a website. It may include the time you spend on the page and your interactions with it. Later on, online services use this info to build profiles and deliver targeted ads, which is the opposite of staying anonymous.
It’s possible to block cookies altogether in your browser settings. Alternatively, you can avoid them with the help of a privacy-focused browser extension like Ublock Origin or Ninja Cookie. Also, you can clear the cookies remaining after each browsing session with one of such add-ons. But it’s also important to note that removing cookies completely may significantly affect your browsing experience.
14. Use a password manager tool
Creating strong and unique passwords for each account can be challenging. After all, the same combination of characters is way easier to memorize. Sadly, it also makes it easier for a hacker to compromise you online. Once they learn your password, they will be able to access anything, from your emails to digital wallets and social media accounts.
To avoid this outcome, make sure you use different passwords everywhere and update them regularly. Besides, it’s a good idea to use a password manager tool, such as LastPass or Keeper, which will allow you to store your security keys in a safe place.
💡 Pro tip: Do not save your passwords in your browser. Linking this confidential information to your Google account may sabotage all your efforts to become anonymous.
15. Avoid JavaScript
JavaScript is a popular programming language many websites use in their visuals, animations, and other appealing design components. But there’s the other side of the coin: JavaScript collects lots of data about users.
There are ways to block JavaScript completely, but you may not want to do that since it will result in a much more limited online experience. Another option is to use a browser extension like ScriptBlock to keep JavaScript elements active only on trustworthy websites.
16. Use a live OS on your PC
Standard operating systems, like macOS and Windows, may collect your data even if you don’t download any questionable applications. The thing is that certain pre-loaded programs are designed to log your info (mostly, to share it with developers and improve user experience).
If you want to avoid sharing even the smallest pieces of your information, switching to live OS might be your go-to. Such systems usually run through a USB drive, so you should connect it every time you turn on your device. Some famous examples are Linux-based operating systems, such as Porteus, Puppy Linux, Tails, and Linux Lite.
17. Don’t use a smartphone (if possible)
Have you ever had a feeling that your smartphone is spying on you? It might not be as literal, but mobile devices actually come with lots of security and privacy pitfalls. Many apps simply wouldn‘t work properly without access to your location, microphone, contacts, and other data. From Google Maps and Uber Eats to simple weather and fitness apps are true privacy nightmares.
Ideally, you should avoid using such devices at all, as it’s very difficult to stop them from monitoring you at all levels. But if you can’t do without a smartphone, consider getting as private and secure mobile device as possible. iOS is generally considered more protected than Android. But if you’re striving for anonymity, you need a device with more advanced functionality, such as Purism Librem 5, Blackphone PRIVY 2.0, or Bittium Tough Mobile 2C. Feel free to explore the full list of the best phones for privacy in our blog.
18. Make payments in crypto
Crypto payments are more private, as they are much harder to trace than transactions via credit or debit cards. But while switching to crypto will allow you to avoid unwanted monitoring, it’s not completely anonymous. In fact, a snooper can track you if you use popular cryptocurrencies like Bitcoin and Ethereum. In turn, encrypted crypto coins, such as Monero, Dash, and Zcash, are encrypted, making it nearly impossible to trace them back to your digital wallet.
Also, mind the risks associated with cryptocurrencies. Learn about the most widespread crypto scams and fraudulent techniques and stay away from questionable investment schemes.
19. Read privacy policies carefully
Many users accept privacy policies without reading them, which may be extremely harmful to privacy. The presented information warns you about all the potential pitfalls—for example, a website may collect and share your private data with their partner services and other third parties. And there’s nothing you can do with that after accepting the privacy policy. So, don’t skip this step, as it may come at the cost of your anonymity.
Final thoughts
Online anonymity is not unreachable — but is that really what you want? Hiding every single aspect of your digital life requires significant effort, and your online experience won’t be as seamless and comfortable as you’re probably used to.
While in some cases anonymity is vital, most people are actually looking to make their online presence more private. And for that purpose, you won’t have to give up all your browsing habits. Following some basic cyber-hygiene rules, such as using a VPN and creating unique passwords, will provide the essential protection level without overhauling your online behavior completely.
But no matter whether your goal is to be anonymous or just maintain your digital privacy, a reputable VPN like VeePN is a must. With your IP address hidden and the entire traffic encrypted, you will be able to browse with peace of mind.
Try it out today and check out VeePN’s premium features risk-free with a money-back guarantee!
FAQ: How to be anonymous online
Here are several crucial steps if you want to host an anonymity website:
- Use a premium VPN tool like VeePN.
- Get an anonymous email address.
- Create an anonymous domain name.
- Opt for a privacy-friendly hosting provider.
- Pay for your domain with cryptocurrency.
Yes! Online privacy is a fundamental right of every Internet user. The essential practices you should follow to browse privately include the following:
- Use a VPN.
- Use a private browser and search engine.
- Don’t overshare your data online.
- Manage privacy settings and app permissions on your devices.
- Use an end-to-end encrypted messaging app.
- Create strong and unique passwords.
Theoretically, it’s possible to become an online anonymous. But that requires taking a lot of measures and using multiple tools to hide your digital identity. You will have to reconsider your Internet habits completely, safeguard your data at all levels, and stop using apps and services that may collect or expose your personal information. Find detailed guidelines regarding the best way to stay anonymous online in this blog post.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








