11 Internet Safety Tips for Protecting Your Privacy and Data
We all love using the Internet for things like social media, online learning, remote work, and just good old entertainment. But the thing is, not all of us know how to use it safely. Luckily, we’ve got some great Internet safety tips to keep you protected online. The number one rule is to use a VPN whenever you browse. It’ll encrypt your data and give you peace of mind. As for other tips, read along to find out more.

Danger ahead: common online threats and how to stay safe
To help you navigate the digital landscape safely, we’ve outlined some of the most common online threats you may come across. From identity theft to phishing scams and cyberbullying, these dangers can take many forms and strike at any time.
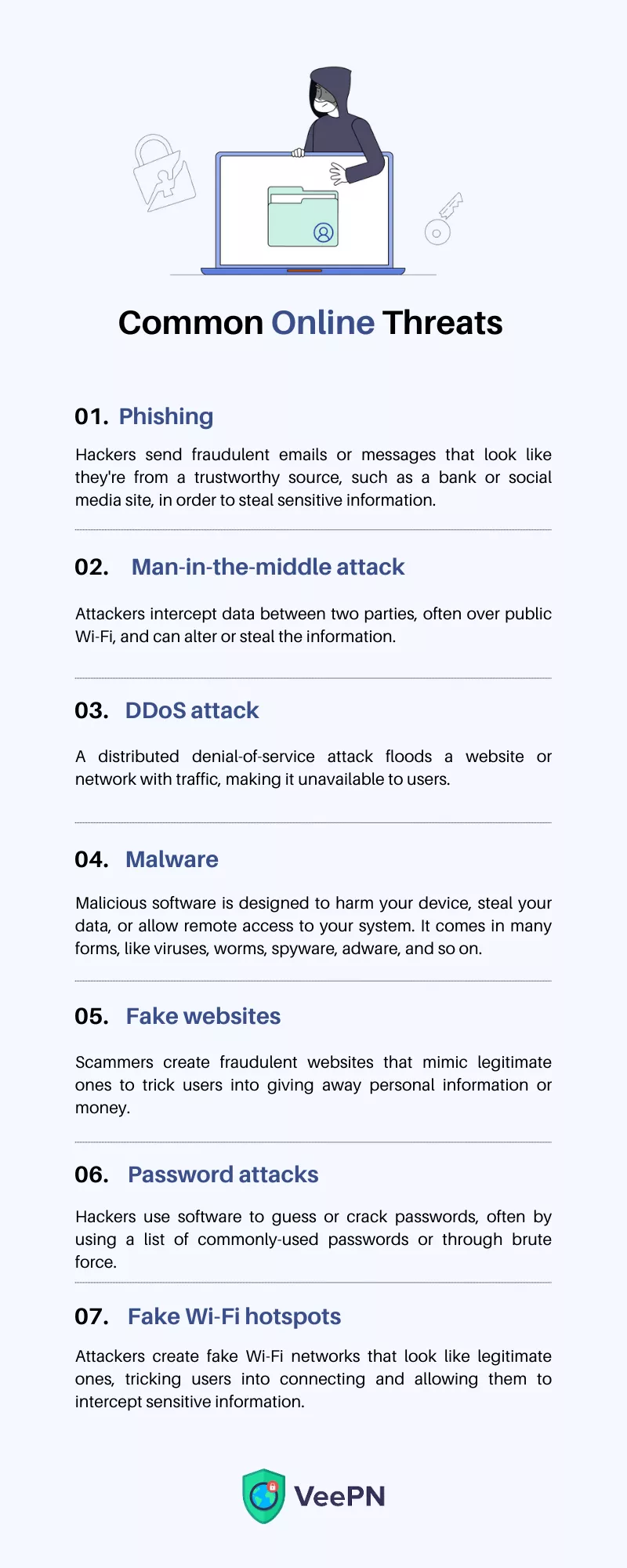
- Phishing. Hackers send fraudulent emails or messages that look like they’re from a trustworthy source, such as a bank or social media site. And those are not just Internet trolls trying to trick you. Such emails contain malicious links, clicking on which endangers your data. Fake emails from PayPal are the most common examples of phishing.
- Man-in-the-middle (MITM) attacks. Attackers intercept data between two parties, often over public Wi-Fi, and can change or steal the information.
- DDoS attacks. A distributed denial-of-service attack floods a website or network with traffic, making it unavailable to users.
- Malware. Malicious software is designed to harm your device, steal your data, or allow remote access to your system. It can come in many forms, like viruses, worms, spyware, and adware.
- Fake websites. These are websites that look like real ones, but are actually created by hackers to trick you into giving them your personal data or money.
- Password attacks. Hackers use software to guess or crack passwords, often by using a list of commonly-used passwords or through brute force.
- Fake Wi-Fi hotspots. Attackers create fake Wi-Fi networks that look like legitimate ones, tricking users into connecting and allowing them to intercept sensitive information.
Surely, these are not all. And while you can’t eliminate all cyber risks altogether, you can take measures to boost your security and safety online. To help you out, we’ve compiled must-follow Internet safety tips for you.
Think before you click: Top Internet safety rules
Ready to learn how to stay safe while browsing the web? Here we’ll cover the main digital safety rules for using Internet. Let’s dive in!
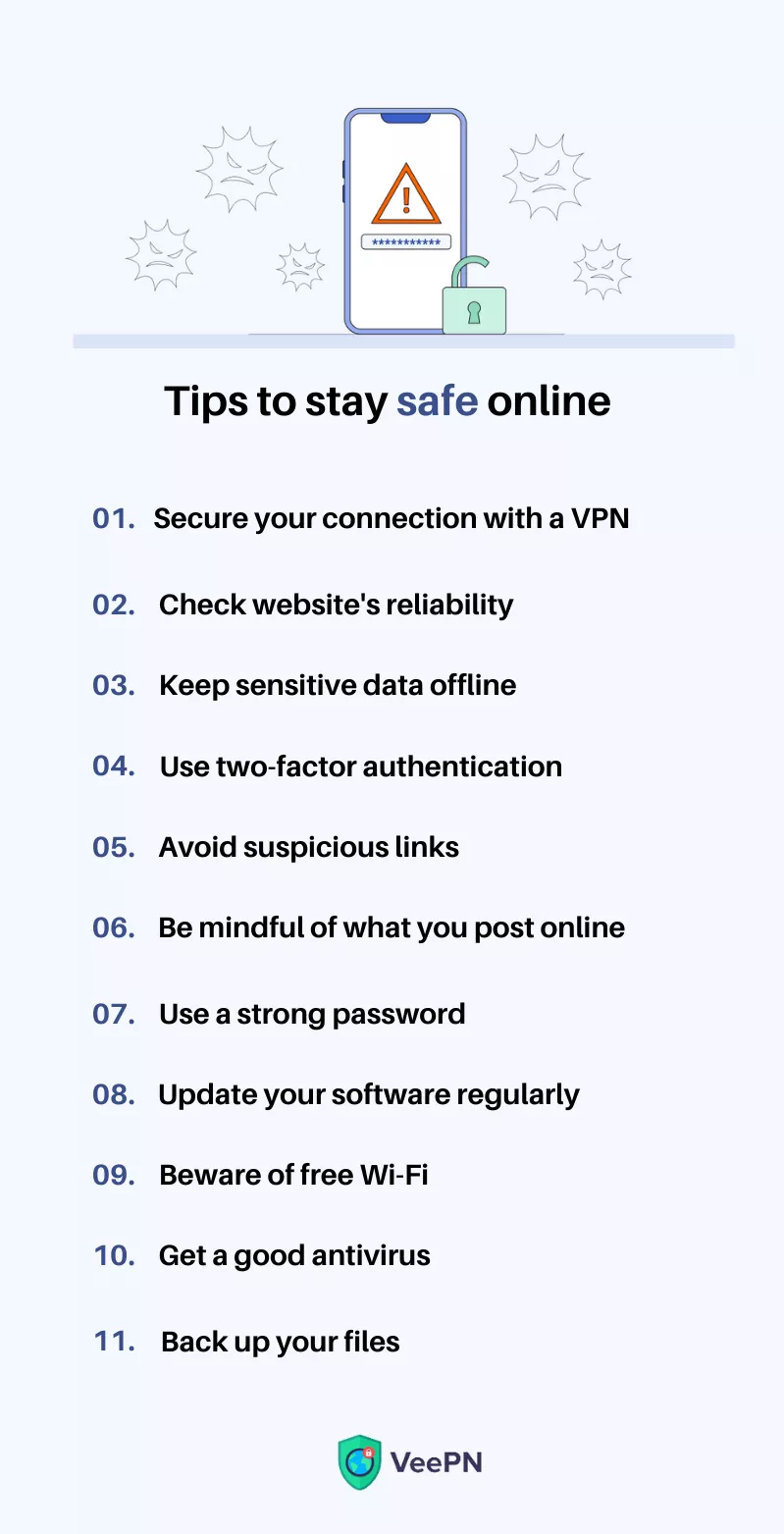
1. Secure your connection with a VPN
✅ Trust a reliable VPN provider with protecting your data. Download VeePN to boost your online security.
We send and receive data back and forth when using the Internet, and hackers and malicious actors can easily intercept it. But by using a virtual private network (VPN), you can protect even your most sensitive information, like financial data, personal emails, or browsing history. Think of a VPN as a secret tunnel that hides your online activities from prying eyes. It encrypts your Internet traffic and hides your IP address, so no one can see what you’re doing online.
2. Check website’s reliability
✅ Look for the padlock icon in the URL bar and check if the website’s address starts with “https.”
Have you ever entered your credit card information on a website, only to find out later that it was a scam? You’re not alone — in 2021, Google’s Safe Browsing detected over 2 billion phishing sites designed to steal personal information, such as usernames and passwords. To avoid falling for online scams, make sure to check the reliability of the website before entering any sensitive info. Here are some online safety tips:
- Look for a privacy policy. Reliable websites usually have a clear and concise privacy policy that outlines how they collect, use, and protect your personal data.
- Check for contact information. A trustworthy website will typically provide contact information, such as an email address or phone number, so you can reach out to them if you have any questions or concerns.
- Read reviews and ratings. Check out reviews and ratings from other users to see what their experiences have been like with the website.
- Use a website reputation tool. Use various tools available online, such as Norton Safe Web or Google Safe Browsing. They can check a website’s reputation and flag any potential security issues.
- Look at the website’s content. See if the pages are grammar mistakes-free. Check if ads are relevant and aren’t swarming on the page.
3. Keep sensitive data offline
✅ If you do have to share sensitive information, be sure to encrypt it for online security.
Even with the best security measures in place, there’s always a risk of your online data being compromised. To be extra cautious, avoid storing sensitive information like Social Security Number online. Instead, keep them offline in a safe place, like a locked cabinet or a USB drive.
4. Use two-factor authentication (2FA)
✅ 2FA makes it harder for hackers to access your accounts even if they have your password.
Adding an extra layer of protection to your accounts is always a good idea. A study by the National Institute of Standards and Technology (NIST) found that 2FA reduced successful phishing attacks by 76%. Two-factor authentication requires you to enter a code sent to your phone or email. You can also enable biometric 2FA (face ID, fingerprint) on your devices for maximum security.
5. Avoid clicking on suspicious links
✅ VeePN NetGuard blocks malicious sites, pop-up ads, and trackers on the spot. Enable the feature in the settings.
Got an email or a message with a link that seems too good to be true or is sent from an unknown source? Be careful then. Phishing can be the culprit here. Phishing messages contain suspicious or weird-looking links that can lead you to fake websites or install malware on your computer, compromising your online security.
6. Be mindful of your online posts and activity
✅ Sharing personal data online can make you more vulnerable to cyber threats like identity theft and hacking.
What you post online stays online forever, so be careful with what you share. Avoid posting sensitive information, like your home address or phone number, and think twice before posting anything that could harm your reputation or safety.
7. Create strong and unique passwords
✅The strongest password should be at least 12 characters long, with a mix of uppercase and lowercase letters, numbers, and symbols.
A strong password is your first line of defense against online attacks. Avoid using the same password for multiple accounts, and consider using a password manager to keep track of all your passwords. A 2022 study from cybersecurity company Hive Systems states that passwords of 4-6 characters can be cracked instantly with brute force. Meanwhile, it can take more than 24 years to crack passwords containing more than 12 mixed characters (uppercase, lowercase, numbers, and symbols).
8. Update your devices regularly
✅ Updates fix any vulnerabilities and make your software secure.
In 2020, outdated software was the second most common cause of data breaches. Outdated software was responsible for 15% of breaches, second only to phishing attacks. Software updates often include important security patches and bug fixes that can help protect your computer from online threats. Make sure to keep your software and apps up to date with the latest updates to ensure your online safety. Enable automatic updates in your device’s settings if needed.
9. Be cautious on public Wi-Fi networks
✅ Use a VPN, like VeePN, to make sure your public Wi-Fi connections are made private.
When 86-year-old Alec Daniels settled in for his coffee at a local shop, he didn’t look like someone who could hack into their Wi-Fi. But in just under 17 minutes, the man took control of the café’s public Wi-Fi and sent phishing emails to everyone connected to it. While Alec is an ethical hacker, who tries to raise awareness about cybersecurity flaws, not all hackers are good-natured. Some can easily take advantage of unsecured Wi-Fi networks.
That said, public Wi-Fi is not safe, especially if you use it to check your bank statements or work remotely from a coffee shop, hotel, or airport. Avoid using it altogether or consider using a VPN when connecting to public hotspots to protect your data.
Additional Internet safety tips are:
- Don’t allow your Wi-Fi to auto-connect to networks.
- Log out of accounts when done using them.
- Don’t log onto a network that isn’t password protected.
10. Get a good antivirus
✅ Along with a VPN, boost your cybersecurity arsenal with a reliable antivirus.
Antivirus software can help protect your computer from malware and viruses that can compromise your online security. Make sure to install a reliable antivirus program and keep it up to date with the latest updates.
11. Back up your files
✅ Use a cloud storage service or an external hard drive to keep your files safe and accessible.
Losing your important files can be a nightmare. To avoid losing your data in case of a computer crash or other unforeseen events, make sure to back up your files regularly.
Bottom line: How to use the Internet safely?
The Internet is filled with dangers, but by following the tips from above, you can minimize the chances of being affected by them. Remember, securing your connection is key to protecting your data and sensitive information from prying eyes. So, stay vigilant, get VeePN service to protect your privacy, and take control of your online safety.
FAQ: Top Internet Safety Tips
Some Internet safety tips include securing your connection wih a VPN, using strong passwords, avoiding suspicious links, keeping your software updated, and being mindful of what you post online. Find out more in our article.
To avoid internet dangers, be cautious of the websites you visit, use strong passwords and two-factor authentication, avoid suspicious links and downloads, keep your software updated, and use a VPN, especially on public Wi-Fi. Learn other Internet safety tips in this blog post.
We all love browsing the web, but let’s face it: online safety is crucial. To keep yourself protected from Internet dangers, we’ve put together a list of tips to keep your Internet connection secure. Take a look; maybe you’re already following some of them!
- Using a VPN to secure your connection in web browsers
- Checking website reliability before sharing personal information
- Keeping sensitive data offline
- Using two-factor authentication
- Avoiding suspicious links and downloads from unreliable online stores
- Using a strong password for your online accounts
- Keeping your software updated
- Being cautious when using public Wi-Fi to gain access to the Internet
- Using a good antivirus
- Backing up your files on mobile operating systems and other devices you use.
VeePN is freedom