Beware of Fake Virus Warning Pop-Ups: How to Recognize and Avoid Them
Fake virus warnings are the common tactic used by scammers to trick you, and if you’re not cautious, they might get real malware to your device. We’ve put together a list of the usual worries people have about those fake virus alerts that appear on their screen. We’ve got the answers you’re looking for, so keep reading to clear up all questions!
1. What is a fake virus warning pop-up?
Fake virus alerts are pop-up windows or tabs that appear on your screen, urgently warning you about supposed malware threats. They’re not coming from your OS or security software but rather a website that’s been abusing the pop-up feature in your web browser to present you with virus scam messages.
Why you might be getting fake virus pop-ups? Fake virus alerts often stem from malicious websites or potentially unwanted programs (PUAs). These programs redirect you to these pop-ups, aiming to trick you into taking actions that compromise your security.
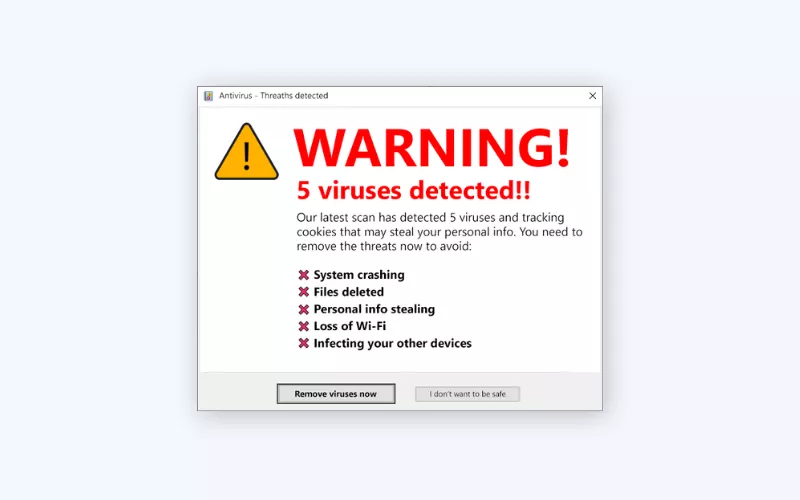
2. What does a fake virus warning pop-up look like?
Identifying a fake pop-up can save you from falling victim to scams or malware. Here are some telltale signs to look out for:
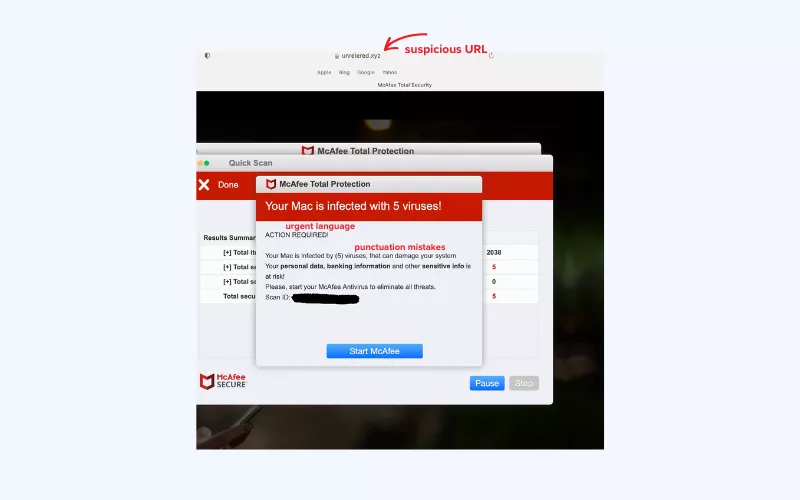
- Urgent language: Fake pop-ups often use urgent and alarming language to create a sense of panic. Phrases like “Your computer is infected!” or “Immediate action required!” are common in such cases.
- Mismatched URLs: Check the web address (URL) displayed in the pop-up. Scammers may use URLs that look similar to legitimate sites but have slight variations. Look for misspellings or domains that don’t match the official website.
- Unsolicited pop-ups: If a pop-up appears without you clicking on anything, it’s likely fake. Legitimate alerts are usually triggered by user actions like clicking a link or button.
- Request for personal information: Legitimate companies won’t ask for sensitive information like passwords, Social Security numbers, or credit card details through pop-ups to gain remote access to your accounts.
- Grammatical errors: Many fake pop-ups are hastily created and contain spelling or grammatical mistakes. Professional companies would rarely make such errors.
- Overuse of exclamation points and capital letters: Fake pop-ups often rely on excessive punctuation and capitalization to convey urgency. Legitimate alerts maintain a more professional tone.
- Unsolicited downloads: If a pop-up prompts you to download software or files you didn’t initiate, be cautious. These downloads might contain malware or unwanted software.
- Unusual behavior: Legitimate pop-ups usually appear as separate windows within a browser. If a pop-up behaves unusually, like blocking your entire screen or preventing you from closing it, it’s likely fake.
Remember that scammers keep improving their tactics, so it’s crucial to stay cautious and trust your gut. If you encounter a pop-up that raises suspicions, close it and avoid interacting with it.
3. What should I do if I’ve already clicked a link?
Clicked the link or button in the alert by accident or the panic took over? There’s a chance you might have downloaded a virus to your computer. Stay calm, but take steps to check your device for malware
If you have a good antivirus tool like VeePN, use it to scan your Windows PC or Android device. VeePN scans your device for viruses and removes them if any are found. You can run quick scans or full scans depending on how thorough you want to be. You can also set up scheduled scans to automatically check your device regularly.
Besides, with VeePN, you’re not just getting antivirus protection. You also get a virtual private network (VPN), which is another powerful cybersecurity tool for keeping your information safe. A VPN changes your online location and makes your data unreadable to prying eyes due to powerful encryption. Try VeePN risk-free to keep your devices protected at all times!
4. How does a fake virus warning pop-up work?
These fake pop-ups are a type of scareware, using social engineering (that is, playing on people’s feelings of trust, fear, or curiosity) to make you feel anxious. They have a sneaky purpose – to fool you into taking immediate actions like downloading fake software or giving away sensitive information. If you think your device is infected, you might react impulsively and unintentionally download harmful files.
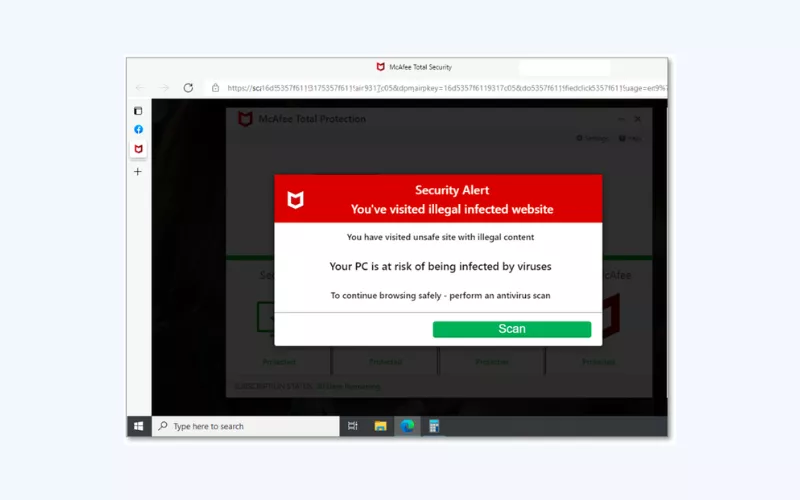
Proceeding with the alert can put you at a serious risk, such as getting malware on your device, having your browser taken over, or your data and even identity stolen. That’s why learning how to spot a fake virus alert is key.
5. How do I know if a virus alert is fake?
Easy. If you don’t have antivirus software on your computer, any virus alert you come across is fake. When you do have antivirus software, only trust alerts that appear in a window from your software. Pop-ups on web pages or in your browser are always fake.
📌 Note: Don’t mix up virus alerts with browser security warnings. Browsers often warn you about unsafe websites, but those aren’t virus alerts.
I keep getting phishy virus alerts from a real antivirus software. Are those alerts legit then?
Scammers can go as far as send you fake antivirus pop-ups posing as a legitimate company. If something looks off with a pop-up, don’t make any rash decisions just yet and do not click any links. Check the message for any signs of a fake virus alert and report the message as phishing to that antivirus company.
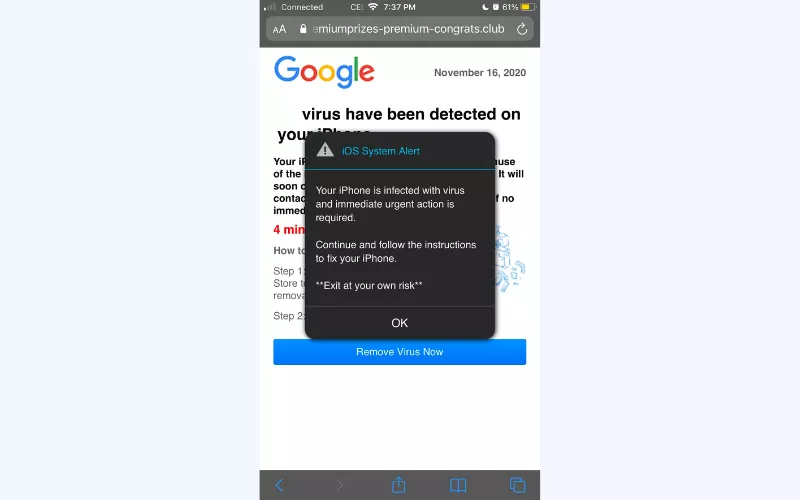
6. Are the virus warnings that pop-up on an iPhone/Mac real?
No, these are fake iPhone/Mac virus warnings. iOS/macOS doesn’t show virus warnings. So if you receive one, it’s likely fake or a scam from a website. Apps in the App Store are carefully checked, so you’re usually safe. Just make sure to update your device regularly and avoid installing suspicious apps apps from unknown sources.
7. Are there any real virus warnings pop-ups on an Android?
Same here. Android OS doesn’t have an antivirus system built-in, so it can’t show your virus alerts. However, if Google Play Protect thinks your device has a malicious app, it can block it or tell you to uninstall it.
8. What should I do if I see a fake virus alert?
If you encounter a fake virus alert, follow these steps and tips to handle the situation:
- Stay calm: Keep a cool head and don’t panic. Fake virus alerts are designed to create fear and urgency.
- Don’t click: Avoid clicking on any buttons, links, or pop-ups within the alert. These could lead to malware.
- Close the pop-up: If the fake alert is a pop-up window, close it using the X button in the top corner of the window or by pressing the Alt+F4 keys simultaneously (Windows) or Command+W (Mac).
- Don’t provide personal information: Legitimate software wouldn’t ask for this in a pop-up.
- Don’t call any numbers: Sometimes fake alerts include phone numbers to call for assistance. Do not call these numbers, as scammers may try to trick you into giving them access to your computer or personal information.
- Use Task Manager (optional): If you can’t close the alert or suspect your browser is frozen, you can open the Task Manager (Ctrl+Shift+Esc on Windows or Option+Command+Esc on Mac) to forcefully close the browser or the alert window.
- Update software: Make sure that your operating system, browser, and antivirus software are up to date. This helps prevent security vulnerabilities.
- Run a scan: If you have legitimate antivirus software, perform a full system scan to ensure that your device isn’t infected with any actual malware.
- Clear browser cache: Clear your browser’s cache and cookies to remove any traces of the fake alert and prevent it from reappearing.
9. I ignored and closed the fake pop-up but it keeps appearing. How do I remove it?
Remember, the fake pop-up alert isn’t coming from your OS or security software but a website that abuses the pop-up feature in your web browser and shows you these scam messages.
So, how do you get rid of fake pop-up viruses? In this case, you need to disable pop-up messages in browser settings. Here’s how to stop pop-ups in Chrome and other browsers.
For Google Chrome (Version 96+):
- Type chrome://settings/content/notifications in the address bar and hit Enter.
- Remove any non-google.com domains from the Allow section.
- Turn on the option Don’t allow sites to send notifications.
That’s how you can get rid of a Google virus warning.
For Chrome Version 88 and older:
- Click on Settings.
- Go to Advanced, then Site Settings, and select Notifications.
- Change Ask before sending (recommended) to Blocked.
This is the way to get rid of the fake Google virus warning on phone and other devices.
For Mozilla Firefox:
- Click on Tools, then select Settings.
- Go to Privacy & Security, then Permissions, and choose Notifications.
- Click on Settings, Remove all websites, then select Block new requests asking to allow notifications.
- Save changes.
For Microsoft Edge (Chrome-based, Version 91+):
- Type edge://settings/content/notifications in the address bar.
- Turn off Ask before sending (recommended).
- If there are entries in the Allow section, click the ⋯ menu for each and select Remove.
📌 Note: For Microsoft Internet Explorer, notifications are not supported.
10. How to prevent fake virus warning pop-ups
To avoid those virus detected pop ups in future, staying smart and safe is the way to go. Follow these easy Internet safety tips to protect yourself:
- Avoid shady links and attachments: If it looks suspicious, steer clear.
- Say no to spam: Revoke permissions from any spam site you see.
- Permissions matter: When a site asks for notification permission (unless it’s trustworthy), select Deny.
- Ad blocker help: Get an ad blocker to cut down on annoying pop-ups. Install VeePN’s dedicated apps or browser extensions to stop malicious pop-up ads and websites.
- Stay updated: Keep your software up-to-date for top-notch security.
- Scan for safety: Run antivirus scans regularly to stay clean.
- Boost security with a VPN: Consider a VPN for extra protection against troublemakers.
And there you have it! With VeePN as your trusty cybersecurity companion, your devices and data are shielded around the clock, letting you enjoy extra peace of mind. Take care and stay secure!
FAQ
Since pop-up alerts aren’t coming from your OS or security software but a website that abuses the pop-up feature in your web browser, you need to disable pop-up messages in browser settings with your browser’s pop-up blocker. Learn how to prevent fake virus alerts, stop pop-ups in Chrome and other browsers in this blog post.
It’s a false error message appearing in your browser stating that the system has spotted suspicious actions. Typically, users end up on the site unknowingly – they are redirected by different potentially unwanted programs (PUAs) that sneak into systems without consent. To remove it, stop pop-ups in your browser, clear your browser cache, install antivirus softwareand run an antivirus scan, and follow Internet safety practices. Find out more in this article.
VeePN is freedom