What Is SOCKS5 Proxy and Should You Use It?

If you need to enhance your Internet privacy and mask your online identity, SOCKS5 will definitely come in handy. It will allow you to fake your IP address and access the desired content without being tracked by third parties. Compared to other proxy servers, SOCKS5 is a more reliable solution thanks to its flexibility, reliability, and good connection speed.
However, SOCKS5 is not 100% secure. Unlike a VPN (virtual private network), it won’t keep you away from major cyber threats, such as hacker attacks, viruses, and infected links. So is SOCKS5 proxy worth it? Keep reading to learn how SOCKS5 works, understand its pros and cons and learn how to set it up on your device.
What is SOCKS5 proxy?
For starters, let’s come up with a definition first.
SOCKS5 is the latest version of the Socket Security (SOCKS) protocol that spoofs users’ IPs by capturing data packets and rerouting them to an additional server. This way, it provides you with an alternative virtual location, while the real one is hidden. In other words, this means that your data travels to an intermediary proxy server, which gives it a random IP address and sends it to the destination server (the website you want to access).
But most proxies can do the same trick. What’s the difference, then?
SOCKS5 vs. HTTP proxies
One of the main specifics that makes SOCKS5 stand out from other proxies is that it’s more stable and flexible. For example, HTTP proxies (also known as high-level proxies) can handle only HTTP and HTTPS web pages, while SOCKS5 (low-level proxies) can cope with any kind of Internet traffic.
Let’s take a closer look at how SOCKS5 proxies reroute your traffic and hide your identity (but note, the process is not completely secure – more on that in a bit).
What does SOCKS5 proxy do?
SOCKS5 does change your IP address, but how? Let’s look at this simple example to understand this process better.
Let’s say you want to visit a particular website without being tracked. Then, before reaching its final destination, the request from your IP goes through a SOCKS5 proxy server with another IP. When your data travels to the requested server, it will see the IP of the proxy server instead of your real address.
Besides, SOCKS5 ensures that only authorized clients can connect to the server thanks to three different authentication methods:
- Null authentication is applied when you’re connecting to a proxy server.
- Username/password authentication requires your credentials to connect to a proxy.
- GSS-API authentication verifies your digital identity at the operating system level.
Moreover, SOCKS5 uses both UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) to provide reliable and fast connections.
So, should you use a SOCKS5 proxy after all? Let’s discuss its benefits and downsides to find out.
Pros and cons of using SOCKS5 proxy
There are a number of compelling reasons to use a SOCKS5 proxy. However, this solution comes with certain drawbacks one shouldn’t neglect. Here are the most significant pros and cons of a SOCKS5 proxy to consider.
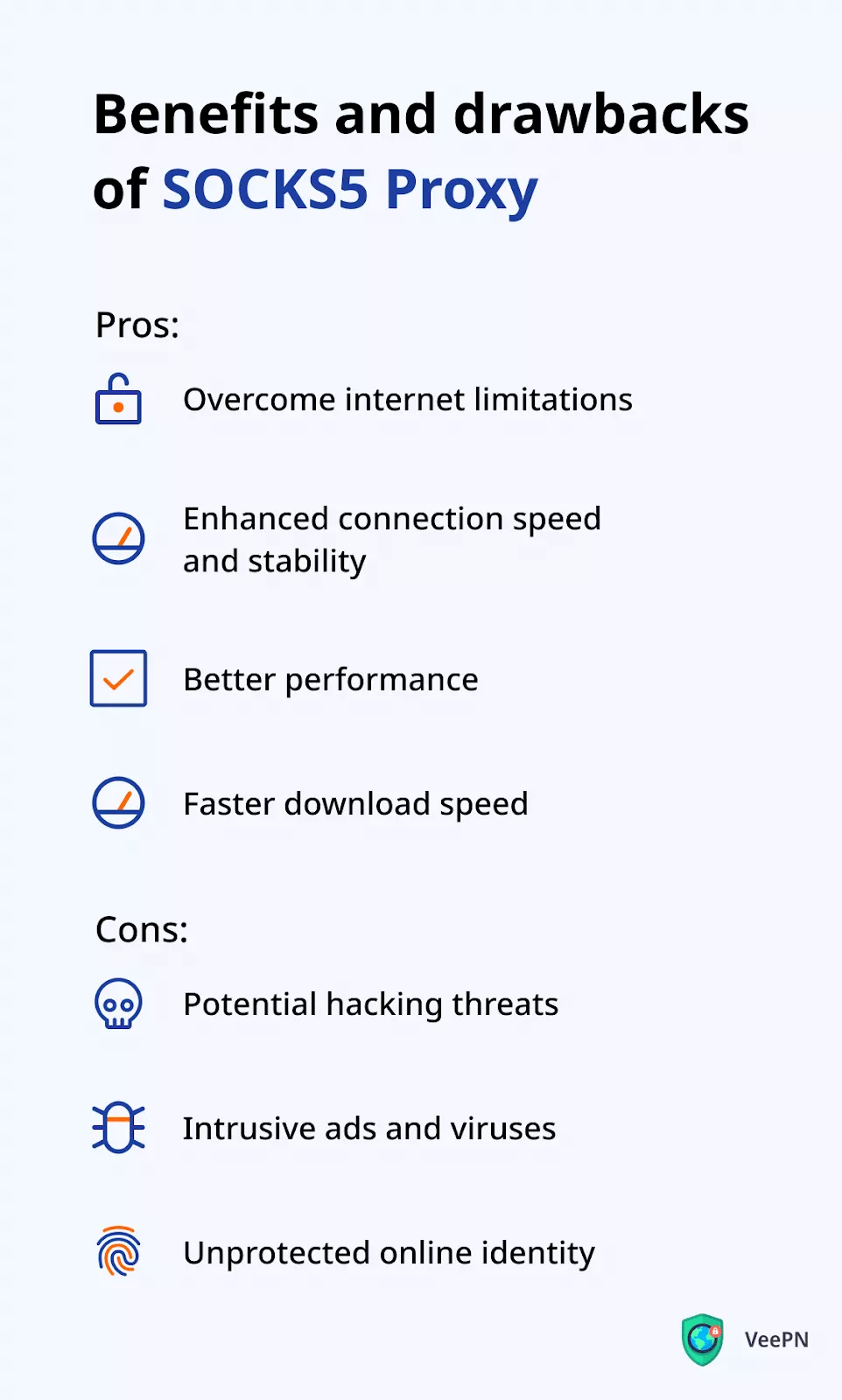
Benefits of SOCKS5
- Overcome internet limitations. If certain websites are blocked for you, using SOCKS5 is one of the best ways to get around Internet limitations. It’s particularly helpful if your IP was blacklisted or even if a VPN server you’re using was detected and blocked. However, a SOCKS5 proxy will likely fail to slip through national firewalls that use more advanced technologies, such as DPI (deep packet inspection). In this case, a VPN is a much more effective solution.
VeePN is the VPN service not intended to be used for bypassing copyright regulations or other illegal behavior. For more details, please read the VeePN Terms of Service.
- Enhanced connection speed and stability. The previous versions of SOCKS used only TCP protocol to ensure smooth and reliable data transfer. SOCKS5, in turn, is also enhanced with the UDP protocol that significantly improves the connection speed. Instead of controlling the order and stability of transferred data, which is covered by TCP, it reduces the time required for communication between SOCKS5 proxy servers.
- Better performance. Unlike other types of proxy servers, SOCKS5 doesn’t rewrite data packets. It means that there are fewer errors in the communication process, which takes the service’s performance to the next level.
- Faster download speed. Another reason why the communication with SOCKS5 is faster than with any other type of proxy is that the data packets are much smaller. It results in a greater download speed, especially when using P2P platforms.
Drawbacks of SOCKS5
The main problem of SOCKS5 proxies is the lack of data encryption during transmission. This issue causes the following security challenges.
- Potential hacking threats. It’s not recommended to perform any activities related to sensitive data, such as typing your bank account credentials, using a proxy solution like SOCKS5. When moving through a third-party server, it can be compromised by hackers in a blink of an eye. Moreover, if you happen to connect to a malicious proxy, it may hijack your private information from your device.
- Intrusive ads and viruses. Proxy servers often generate revenue by sending advertisements to connected users. And apart from being annoying, these intrusive ads and pop-ups may pose an actual risk to your cybersecurity. Many links are infected with viruses. Once you click on such a link, you will install malware on your device. Such malicious programs aim at collecting users’ data and sending it directly to hackers.
- Unprotected online identity. When connecting to a proxy server, you share your personal data, like your hostname, with strangers. And there is no guarantee that you can trust them. Identity theft is very common these days, as your ID can be used with malicious intentions or sold on the dark web.
Now you know what SOCKS5 is, how it works, as well as its pros and cons. But can it actually replace a VPN in your online privacy toolkit? Many confuse these solutions since both reroute users’ data through remote servers and alter their IPs. However, they are not the same. Here is why.
SOCKS5 proxy vs. VPN: the difference explained
A virtual private network (VPN) is software that enhances users’ Internet privacy and, at the same time, shields them from potential cyberattacks. That is because a VPN doesn’t just spoof your IP. It moves your traffic through a specific tunnel empowered with reliable encryption. As a result, no third party, be it a hacker, snooper, or even your Internet service provider (ISP), can access your data.
SOCKS5 proxy doesn’t encrypt your traffic while it’s moving your data through a remote server. So if online snoopers want to interfere with your online activities, they will be able to do it, whether you’re using a proxy server or not. SOCKS5 is efficient for certain activities, and it’s quite stable if compared to other proxies. But it is not as reliable as a VPN, especially when it comes to protecting your sensitive data.
Now that you’re aware of the positive sides of a SOCKS5 proxy, as well as the potential dangers you may face when using it, let’s learn how to set it up on your device.
How to set up SOCKS5 proxy
Setting up a SOCKS5 proxy on your device, whether you’re a macOS or Windows user, is relatively simple. Take the following steps to get the job done.
How to use SOCKS5 proxy on Mac
- Go to System Preferences > Network
- Head to the Advanced section and find Proxies
- From the list of available options, pick the SOCKS proxy
- Enter the address of your proxy server
- Click OK to enable the changes
How to use SOCKS5 proxy on Windows 10 and 11
- Go to Settings > Network & Internet
- Find the Proxy section
- Turn on the Manual proxy setup
- Enter your proxy server’s address
- Click Save to enable the changes
Want to improve your online security? – Try VeePN!
A proxy server like SOCKS5 can be useful if you need to access limited content or hide your IP address while browsing the web. But if your goal is to boost your online security, we recommend turning to a powerful VPN solution like VeePN. It will not only enhance your privacy but also protect your data thanks to the most powerful AES-256 encryption standard. Besides, if you install the VeePN app on your device, you can also take advantage of a SOCKS5 proxy, along with other reliable VPN protocols. Download VeePN today and feel safe on the web at all times.
FAQs
Can you get SOCKS5 for free?
Yes, there are some free SOCKS5 proxies you could opt for. But we do not recommend using such solutions. Similar to free VPNs, free proxies are often unreliable or even dangerous. In particular, a free proxy server may monitor your traffic, compromise your data, and send you malware-infected ads.
Is SOCKS5 the same as a VPN?
There is a drastic difference between a SOCKS5 proxy and a VPN. A virtual private network moves your traffic through a remote server and encrypts it along the way. The encryption and decryption processes might slightly slow down your connection speed, but they also ensure that nobody can compromise your cybersecurity. Meanwhile, SOCKS5 doesn’t encrypt your traffic. It simply routes it through a proxy server to spoof your IP address. As a result, SOCKS5 is a bit faster but less secure than a VPN. For more detailed information, read this article.
VeePN is freedom