Protection from Malware: Best Practices and Tools for Every Device
A lone traveler venturing into the dark and treacherous woods of the Internet, beware! Unseen monsters such as viruses, ransomware, and spyware lie in wait to ambush unsuspecting explorers like you. This guide would serve you as your map, illuminating the paths to safety, while VeePN can be your trusted weapon, shielding you from harm and ensuring a reliable malware protection. Ready to journey with confidence? Let’s dive into the essentials of protection from malware right now!

What is malware?
Malware, short for malicious software, refers to any software intentionally designed to cause damage to a computer, server, client, or network. These monsters can be of different breeds! The most common types of malware include:
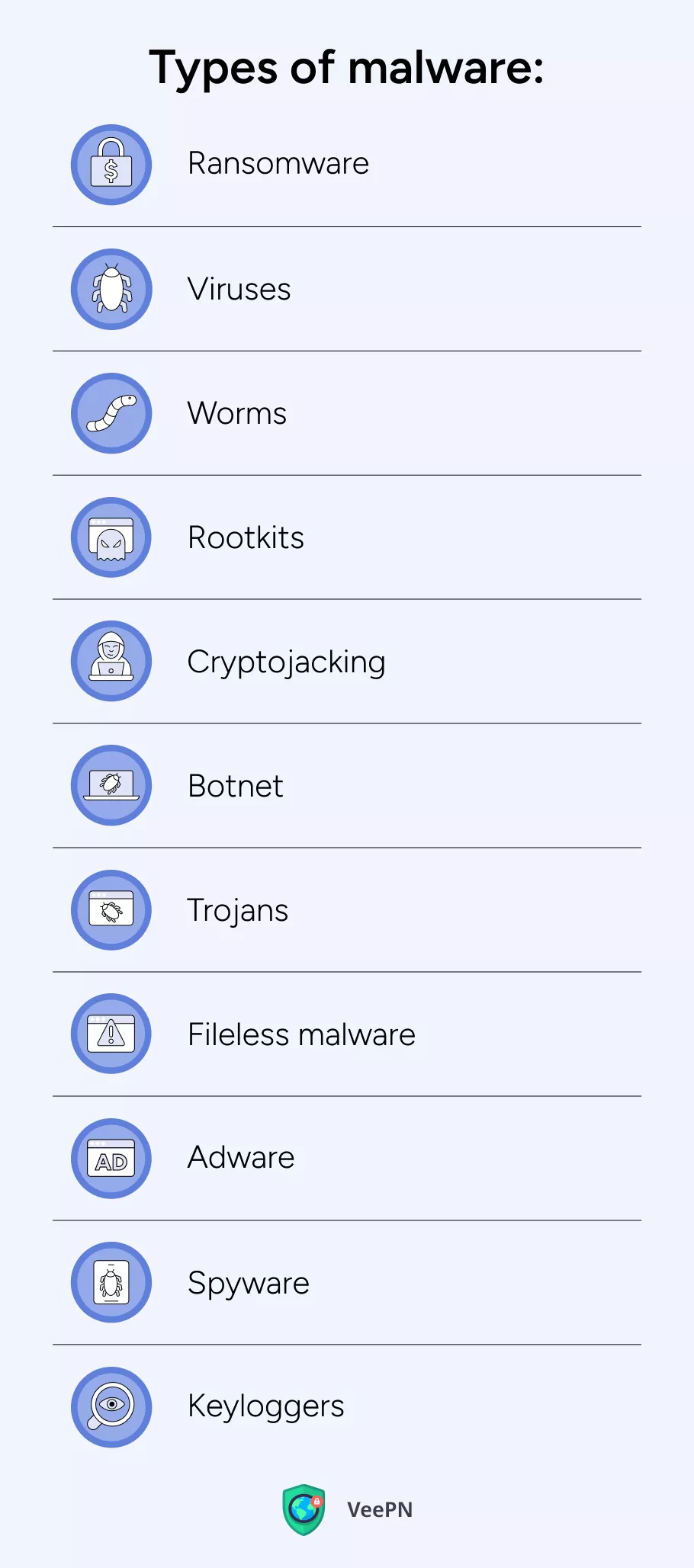
👹Ransomware: A type of malware that encrypts your files and demands a ransom for decryption.
👹Viruses: Disguised as harmless programs, these parasites aim to corrupt your files and cause damage to your device once they sneak in.
👹Worms: Similar to viruses, but they can self-replicate and spread malware independently without human intervention.
👹Rootkits: Tools designed to remotely access or control your device without being detected by you.
👹Cryptojacking: The unauthorized use of your device to mine cryptocurrency with the help of a malicious code.
👹Botnet: A collection of infected devices that can be controlled remotely to perform malicious tasks, often used for Distributed Denial of Service (DDoS) attacks.
👹Trojans: Malware that disguises itself as legitimate software to trick you into installing it.
👹Fileless malware: Exploits vulnerabilities in the system without leaving any trace on the disk, making detection difficult.
👹Adware: Software that automatically displays or downloads advertising material when you are online.
👹Spyware: Secretly monitors your online activity and collects your personal information without your consent.
👹Keyloggers: Record keystrokes to capture your sensitive information like passwords and credit card numbers.
Since malware is such a dangerous threat, knowing about potential consequences of encountering one of these mutants during your travels along the Internet would be helpful.
Why is malware protection important?
Malware protection is crucial for safeguarding your devices and personal data. On average, 11.5 malware attacks happen every minute, so falling a victim to such an ambush can result in:

🆘Data and financial loss: Malware can corrupt or delete valuable files, leading to potential losses of important information and money.
🆘System damage: Infections can cause irreparable harm to hardware or software, often resulting in costly repairs.
🆘Network disruption: Malware can disrupt normal network operations, resulting in widespread downtime and loss of productivity.
🆘Personal information leaks: Sensitive information, including financial details, can be stolen, putting you and your money at significant risk.
🆘Identity theft: Cybercriminals may use stolen information to impersonate you, thereby causing you severe financial and reputational damage.
How does malware infiltrate your devices?
Since malware attacks can be of different breeds, the ways it infiltrates devices also vary:
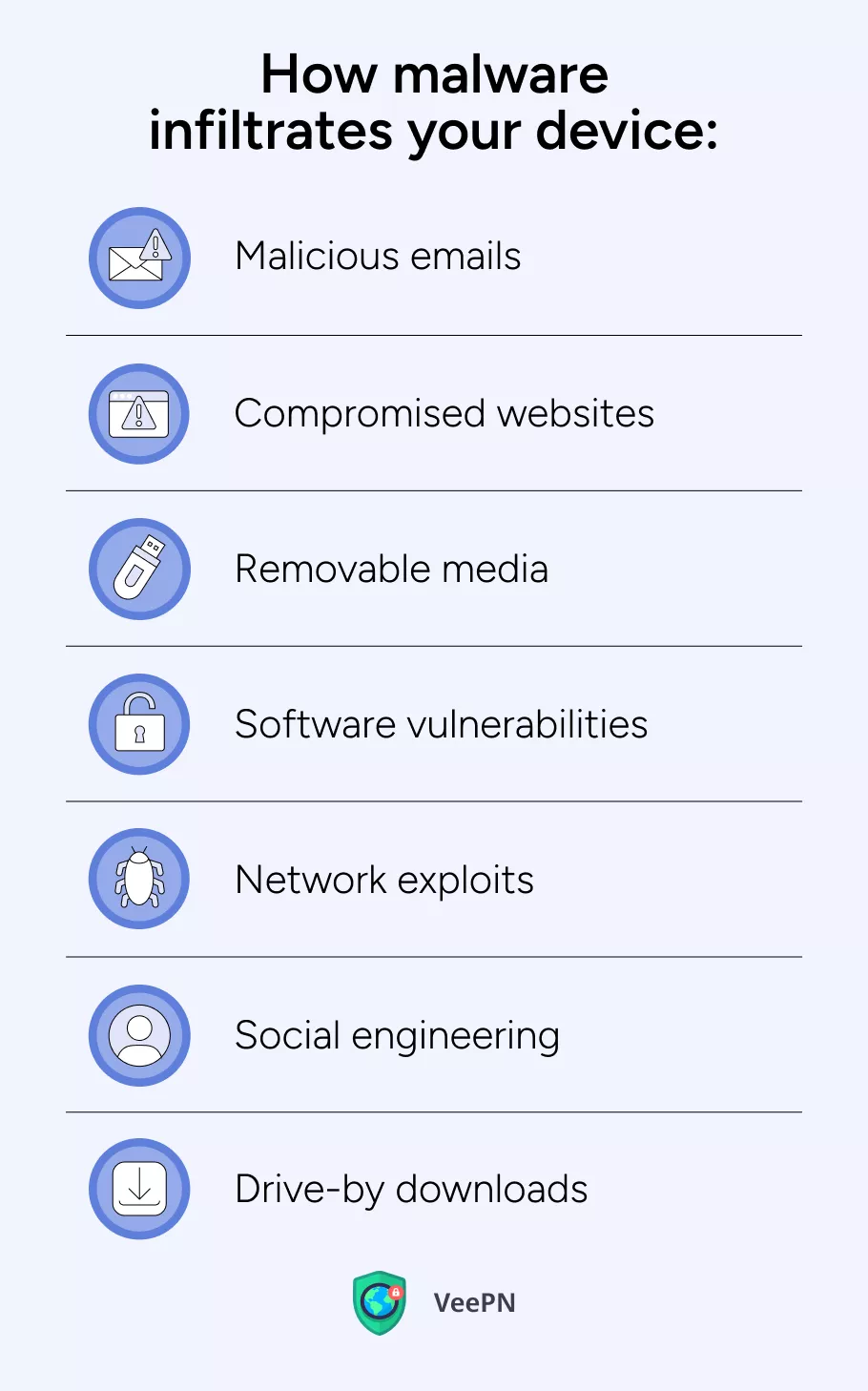
- Malicious emails:
- Phishing: Emails that appear legitimate but are designed to trick users into providing sensitive information.
- Spam emails: Unsolicited emails that often contain harmful links or attachments.
- Compromised websites:
- Malicious websites: Sites specifically designed to host malware.
- Hacked websites: Legitimate sites that have been breached and used to distribute malware.
- Removable media:
- Infected USB drives: USBs that carry malware can infect devices once connected.
- Shared storage devices: Devices shared among multiple users can transmit malware across systems.
- Software vulnerabilities:
- Outdated software: Failing to update can leave systems exposed to known exploits.
- Unpatched software: Lack of security patches enables malware to take advantage of vulnerabilities.
- Network exploits:
- Network vulnerabilities: Weaknesses in network security can be exploited by attackers.
- Remote code execution: Attackers gain the ability to execute code on a remote system.
- Social engineering: The technique hackers manipulate people into sharing confidential information.
- Drive-by downloads: Codes embedded in websites that automatically download malware onto your devices.
Common signs of malware infection
Just like it’s vital to hear the roar of the hungry beasts in the deep forest, it’s essential to recognize the signs of malware attacks early. Look out for:

🚩Slow device performance: A noticeable lag in your devices may indicate an infection.
🚩Frequent crashes: If your device is crashing more often than usual, malware could be the cause.
🚩Unusual network activity: Unexpected spikes in Internet usage might suggest malicious activity.
🚩Unwanted pop-ups: Excessive pop-ups or ads, especially from known websites, can be a sign of adware.
🚩Strange browser redirects: Frequent redirection to unfamiliar sites may indicate a browser hijack.
Malware attacks protection: Best practices
To ensure best malware protection, consider implementing these best practices and tools:

🛡️Update software and operating systems: To prevent malware from infecting your devices, regularly check for updates to patch vulnerabilities. In 99% of cases, the most recent version of software is the most secure one.
🛡️Download from reputable sources: Only download software from trusted websites to minimize risk.
🛡️Avoid suspicious links: Be wary of links in emails or on social media that seem suspicious or try to spoof a link to a legitimate site. For example, amaz0n.com instead of amazon.com is a red flag.
🛡️Use strong passwords: Create complex passwords and change them regularly to enhance security. Consider password management and generation software such as LastPass, Keeper, or 1Password
🛡️Adopt email security tools: Use spam filters and email scanners to block malicious emails. Also, we would like to recommend using VeePN’s Anonymous Email that creates a fake email address you can use to hide your real ones. All messages coming to your fake email will be forwarded to your real one, but nobody can know about it.
🛡️Use a VPN: A virtual private network encrypts your Internet connection, providing an additional layer of security. However, free VPNs may not offer adequate malware protection, so consider a premium solution like VeePN to fully safeguard your online activities.
How VeePN can shield you from malicious software
VeePN acts as a robust weapon against almost any evil creature you may face on your journey across the Internet. Just check the security features VeePN offers:
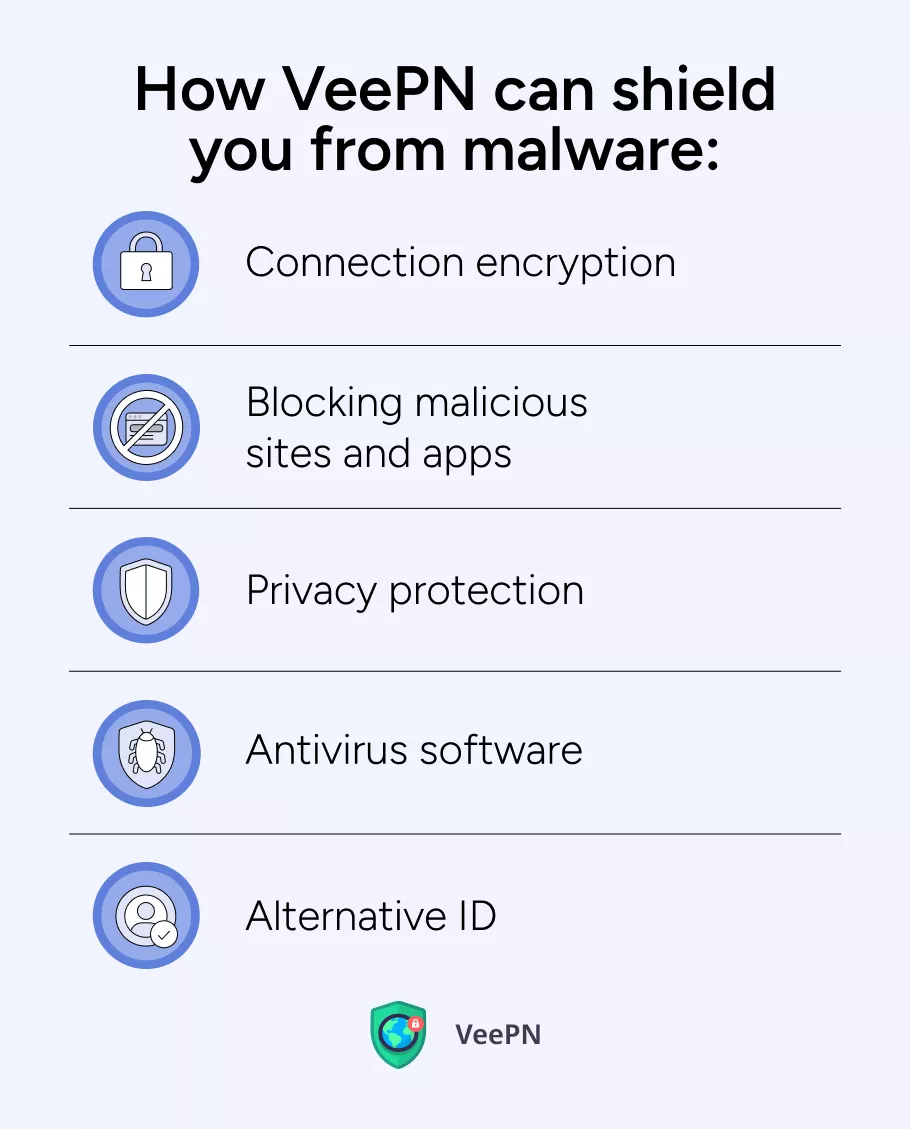
⚔️Connection encryption: VeePN uses AES 256-bit encryption standard which means hackers won’t be able to read a bit of your Internet traffic even if they manage to intercept it.
⚔️Blocking malicious sites and apps: Due to NetGuard anti-malware software, VeePN can detect malware and prevent access to known malicious websites, acting as a first line of defense.
⚔️Privacy protection: By passing your traffic through an encrypted tunnel to a remote server, the app will hide your IP address, so you can walk across the whole Internet without a fear that monstrous malware will sniff after your steps.
⚔️Antivirus software. Along a range of features, VeePN offers an antivirus software for Android and WIndows which comes as a part of our security bundle. By using our antivirus, you can establish a solid basis for your cyber defense against malware.
⚔️Alternative ID: This feature enables you to create an alternative persona for signing up and visiting various sites and online services without revealing your real identity.
Equipped with VeePN, all-in-one digital security software, you can confidently navigate the vast landscape of the Internet while keeping the lurking monsters of malware at bay. Download VeePN right now and use one subscription for up to 10 devices simultaneously!
FAQ
A reliable VPN such as VeePN can help protect your data by encrypting your Internet connection, but it is not designed to detect or block malware. To safeguard against malware, you need dedicated tools like antivirus software that can scan and remove malicious files. Combining a VeePN with other cybersecurity solutions offers comprehensive protection.
The best protection from malware is a multi-layered approach that includes:
- Reliable antivirus software to detect and remove threats.
- Keeping your devices and software updated to patch vulnerabilities.
- Practicing safe browsing habits, like avoiding suspicious links and downloads.
- Using strong passwords and enabling two-factor authentication to secure accounts.
Read this article to learn other ways of protection against malware.
Yes, spreading malware is illegal in most countries and is considered a cybercrime. It violates laws that protect computer systems and data, such as the Computer Fraud and Abuse Act (CFAA) in the U.S. or equivalent legislation worldwide. Offenders can face severe penalties, including fines and imprisonment, depending on the severity of the damage caused.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan







