10 Cybersecurity Memes to Think About
Cybersecurity has become a thing that makes many people feel concerned if not frightened. Leaking your credit card CVV or just getting a virus on your device is definitely unpleasant, especially if it has happened to you in the past. But sometimes, you need to laugh at a problem to be able to solve it. Just like Riddikulus! spell against the Boggart in Harry Potter, remember? With that said, let’s have a good old laugh looking at 10 funny cybersecurity memes we’ve picked and see how you can avoid getting into these kinds of trouble.
Introduction to Cyber Security
In today’s digital world, cyber security isn’t just a buzzword—it’s the backbone of protecting systems, networks, and all that precious data we can’t live without. From your favorite streaming service to your company’s sensitive files, everything is a potential target for cyber threats. That’s why security awareness and regular security awareness training are more important than ever.
Cyber security is all about putting the right security measures in place to keep the bad guys out and your information safe. This means using strong, unique passwords (no, “password123” still doesn’t count), keeping your software up to date, and staying alert to the latest scams. Security teams are the unsung heroes working behind the scenes, constantly improving the organization’s security posture and preparing for incident response planning. And let’s be honest—sometimes, a good security meme is just what you need to remind everyone that protecting systems is serious business, but it doesn’t have to be boring. So, as you scroll through these memes, remember: a little laughter can go a long way in building security awareness!
Best cybersecurity memes to laugh at and keep in mind
We’re going to make fun out of different topics from phishing, to DDoS attacks, and doxxing. Get yourself comfortable, and onto security awareness memes!
Password management is lifeblood of cybersecurity

Creating strong passwords is the foundation of cybersecurity. When you need to come up with a reliable password, it obviously shouldn’t be 123, while 456 instead won’t help much either. The plainer and more predictable your passwords are, the less time a hacker will need to crack them.
For that reason, we highly recommend installing password management software that can help you generate and securely store all your passwords. However, your password manager has to be trustworthy enough. Otherwise, you’ll just entrust all your passwords to a third party that God knows how will use this information. We suggest using 1Password, Keeper Dashlane or BitWarden. These are good password managers that won’t collect your personal information.
Personal information sharing is bad (even if tempting)

The Internet is full of various scams. Ads, discount coupons, prizes, rewards, and other free stuff entice you to click on a suggested link or leave your personal information. No matter how good the offer sounds, just ignore it and never share your private information.
The one thing you need to keep in mind is that there is no such thing as a free cheese. Free offers are always a scammy trap, and exceptions rarely happen. That’s a cruel and unjust world of the Internet as it is. Take this as an axiom, and you won’t fall victim to fraudsters.
Phishing is a thing to be careful about

This phishing email meme is simple: if you don’t check your email, there are zero chances you’ll click on a phishing link inside letters you received. No email — no phishing.
But if you still need to check your inbox, be careful with clicking on links from unknown and suspicious senders. Just like scams, phishing emails work in the same way: they attempt to entice or frighten you to click on a link without thinking. As a result, you’ll install malware on your device or leak your personal information directly into scammers’ hands.
Both scenarios are definitely bad, so don’t open emails promising you a prize, a lot of money inherited from a relative you’ve never heard of, or just being sent by a stranger you didn’t expect to email you. But if you’ve already clicked on a phishing link, here’s a guide on what you should do.
Employee awareness is crucial in preventing phishing attacks and reducing the risk of falling victim to cyber threats.
Many organizations conduct phishing test exercises to improve security and help employees recognize and respond to phishing attempts.
A celebrity can be a scammer
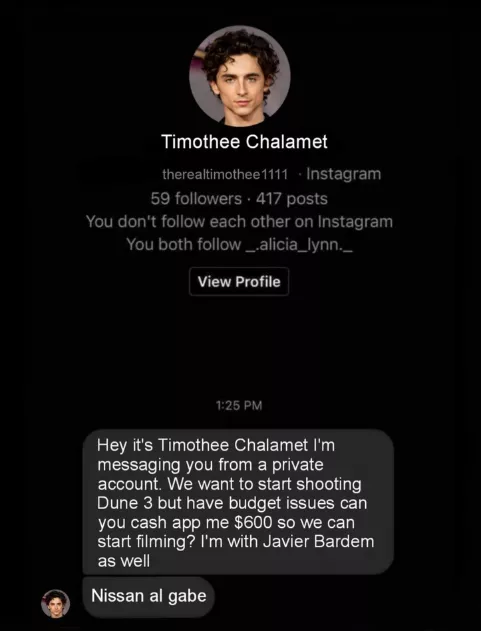
We’ve talked about sophisticated scams that attempt to manipulate you to get your personal information. However, people get scammed with simple yet very impudent strategies like the one you can see in the meme above.
Using a fake account of a celebrity, government official, relative, or friend to look legit in your eyes is the main tactic of such scams. Pay attention to the language a person uses. Scam messages usually sound awkward and generic, avoiding the details.
Using public WiFi is a huge risk

Using a public WiFi hotspot is convenient as you have free Internet access and all that. But guess what? Hackers and scammers think in the same way! Public networks are often unprotected meaning that hackers can use them to steal personal information from unsuspecting people using the same WiFi hotspot.
For that reason, using public WiFi is an immense risk. The good news is that you can safeguard yourself by using a virtual private network (VPN) app. A VPN creates a separate “tunnel” which all your Internet traffic goes through and becomes a bunch of symbols extremely hard to decipher. Even though hackers succeed in intercepting your sensitive information, they won’t be able to read it.
But be careful with free VPNs as they won’t protect your information for real. To make money, free VPN services sell your information to third parties like advertising agencies, so you won’t be really private with a free VPN app.
Malware downloading means you’re in trouble
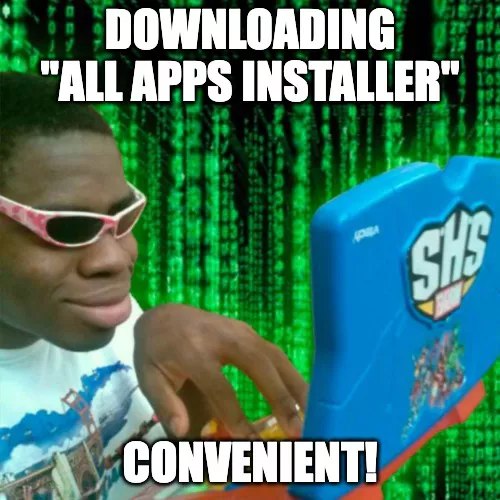
If you downloaded software that promised you to install all apps you need or provide access to free content, it’s not a reason to cheer about. In fact, it means you’ve installed malware which just makes an impression of a super useful and convenient solution.
Again, too-good-to-be-true offers on the Internet equals danger. That’s why we highly recommend you refrain from downloading and installing such ultra-helpful apps. They can really help you solve your tasks, but it’s very likely your device will be infected with a virus and your personal information will be stolen.
Malware may be masked not only as a convenient superapp but also hide behind phishing links or even be fileless. Despite being so tricky, malware is relatively easy to deal with.
First of all, just don’t download any suspicious files from sites you barely know. Second, install applications from legitimate sources such as Google PlayStore, Apple’s AppStore, and so on. Third, use VeePN which has antimalware tool called NetGuard. This app blocks all pop-up ads and detects any malware you may encounter while surfing the web.
A spoofed website always looks odd

A spoofed website is an imitation of a legitimate website that usually contains malware or collects your personal information. Spoofed websites may look just like legitimate ones but always have a strange design or weird URL names.
For example, amazon.com and amaz0n.com do look alike. But if you go to amaz0n.com you’ll end up at a spoofed website that will steal your data and no products in return.
There is no better weapon against spoofed websites than your attention. Check the URLs of such popular websites as: Amazon, BestBuy, PayPal, Netflix, and such. Design and URL addresses of legit sites are always easy to recognize. So if you have doubts, it’s better to double-check whether you are going to visit a completely secure site.
Botnets are unwelcome guests on your device

If your device slows down all of a sudden, there is a high chance it has been infected with a botnet that uses your Internet connection and computing resources for a distributed denial of service (DDoS) attack.
But even if the attack is over, it doesn’t necessarily mean that your device is healthy. The malicious software won’t disappear itself and slow down relapse can happen once again for another attack.
The best way to protect your device from botnets is to use antivirus software to detect and eliminate such a threat. VeePN offers a special security bundle that includes antivirus and breach alert apps that will help you shield your devices from viruses, cyber attacks, and other dangers threatening your online security.
Your organization’s IT team also plays a crucial role in detecting and removing botnets, ensuring your systems remain secure.
Stalking and doxxing are just disgusting
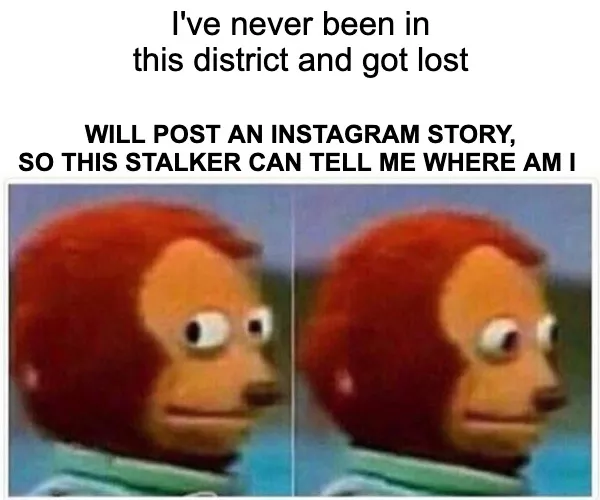
Stalkers follow their victims everywhere trying to doxx them, or in other words, reveal all their personal information for blackmailing and making it publicly available. A stalker’s motivation can vary from just having fun annoying a victim to assaulting real people.
That is why you need to remember basic safety tips that can help you prevent stalkers from following and doxxing you. First of all, don’t share much of your personal information like address, phone number, names of your relatives and so on. In the same vein, we don’t recommend you share any other details of your private life such as your hobbies, favorite places, people you often meet with, and anything else that stalkers can use to track you down.
In addition, you can use a VPN app to mask your real IP address. Since VPN connects to a remote server, your device gets an IP address of a server’s location, so a stalker won’t be able to detect your real whereabouts.
IP address hacking is easy to beat with a VPN

Your IP address is one of the biggest vulnerabilities, which can be hacked and become a starting point for a broader attack. By hijacking your IP address, a hacker can intercept all your Internet traffic and get access to your personal information. Consequently, you can end up losing money on your credit cards or being blackmailed that all photos on your device will go online if you don’t pay a ransom.
You can avoid these risks by using VeePN. The application has access to 2,500 servers in 89 locations, so you can choose any to conceal your identity. Hackers simply won’t be able to see your real IP address and your traffic since it goes through a separate tunnel to a remote server and gets encrypted on its way. On top of that, you can add an extra layer of security by using a Double VPN feature which encrypts your traffic twice: on its way to a remote server and after reaching it.
Security Posture Comprehension
Consider the cyber security of your organization, its security posture can be viewed as the entire health check. It is not merely about having a couple of firewalls or antivirus systems installed but rather knowing your vulnerabilities, what can get into your system and how efficient your security controls (such as access control and intrusion detection) are collaborating to keep the bad stuff out.
A robust security posture entails the fact that you are prepared to protect sensitive information and respond promptly in case something awry. Security awareness training and periodic security questionnaires come into view at that point, they assist you in seeing the areas that are weak before the cyber threat can use them to its advantage. One of the ways your organization can be proactive and fix the vulnerabilities and ensure incident response planning is not a dust-collecting document is by performing periodic estimates of your security posture. Finally, understanding your security positioning is the initial move in ensuring that your data breaches are prevented and that your organization image remains intact.
Evaluation of Cyber Security risks
The thing is, the cyber security environment is rather a game of whack-a-mole you can keep on being attacked by different phishing schemes and scam calls, new vulnerabilities infiltrating your systems, every minute. This is why evaluating cyber security risks is one of the requirements of any organization that wishes to remain on top of the curve.
The risk management structures and vulnerability testing help security teams to determine the location of the most significant risks. This would entail considering all the possibilities of a phishing attack to the consequences of a successful intrusion. Knowing the most dangerous cyber threats, organizations are able to prioritize their security and concentrate on the things that are the most important. The goal? To ensure that the next time you get scammed by phishing email or a scam call, your systems and people are prepared to deal with it.
IT and Cyber Security Management
It is akin to spin plates in that IT and cyber security management requires maintenance of balance between security controls and frequent audits as well as employee training on security awareness. Security teams are ever searching with the latest vulnerability and cyber threats and ensuring that all systems are up to date and that all incident response plans are ready to go whenever needed.
An effective ticketing system can assist in monitoring and fixing the security breach within the shortest period of time, and frequent audits will keep your organization one step further before breach may occur. Proactive management involves not addressing a problem, but rather taking proactive steps in order to identify and address a weakness in the face of a problem. Organizations have a chance to secure their systems, data, and networks with the appropriate combination of security practices, training, and collaboration and, perhaps, rest a little more at night.
Learning the Hard Truth
This is the bitter reality about cyber security: it is never finished. Despite the number of security boundaries that you put into place or how hard your security personnel are working, there is always another security threat in the offing. Breaches may and do occur even in the best efforts of everyone. However, that does not mean that you should give up.
It is rather advisable to develop a culture of security awareness by emphasizing on security questionnaires and frequent security awareness training to keep everybody on their toes. Security memes would be an excellent laugh, but they can also act as a reminder that it is better to be proactive. The hard truth that cyber security is a continuous endeavor would help organizations to enhance their security position, better manage the impact of an incident, and use it as an incentive to continue advancing. Expressing myself, a small dose of cyber security humor, in the world of cyber security, goes a long way, with much vigilance.
Keep your cybersecurity a top priority with VeePN
These computer security memes are an ironic view on online safety and what people think about it. But every joke has a bit of truth, which means you shouldn’t take your Internet privacy for granted.
To keep these funny cybersecurity memes just a bunch of silly pictures and never become your terrible reality, keep remembering the basic security rules and use VeePN. Compatible with the majority of devices and operating systems, VeePN will protect your sensitive information with AES 256-bit encryption and ensure you stay anonymous while surfing the web.
Get VeePN now to safeguard up to 10 devices with one subscription and have a 30-day money-back guarantee.
Cybersecurity Memes to Think About
There isn’t one single universally famous cybersecurity quote, but there are a few well-known options depending on the emphasis you want:
- Serious
- “It’s not a question of if, but when”.
- “Security isn’t something you buy, it’s something you do” .
- Humorous
- “Passwords are like underwear: don’t let people see it, change it very often, and you shouldn’t share it with strangers”.
- “The most secure computer is the computer that’s off”.
The 3 A’s of cybersecurity stand for:
- Authentication verifies the identity of a user trying to access a system. This is typically done through passwords, multi-factor authentication, or biometrics like fingerprints.
- Authorization determines what level of access a verified user has. For instance, a user might be authenticated to access a system, but only authorized to view specific files, not edit them.
- Access control enforces the limitations set by authorization. This might involve firewalls, permissions settings, or other tools that restrict access based on user privileges.
A VPN plays a significant role in cybersecurity by adding an extra layer of protection to your internet traffic. Here’s how:
- Encryption: A VPN encrypts your data traffic, creating a scrambled code that only the VPN server and your device can understand. This makes it unreadable to anyone who might intercept it on the network, like hackers or snoopers on public Wi-Fi.
- Tunneling: VPN establishes a secure tunnel between your device and the VPN server. All your Internet data travels through this encrypted tunnel, shielding it from prying eyes on the public internet.
- IP masking: When you use a VPN, your actual IP address is hidden. Instead, the websites and services you access see the IP address of the VPN server, making it harder to track your location and online activity.
That’s why we recommend you try VeePN, a robust VPN service that encrypts your data with the best industry standards and offers a security bundle to provide a 360-degree defense of your devices.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






