Understand How Fileless Malware Works and How to Prevent It

The digital world does not stand still, and unfortunately, neither does its dark side. Different viruses, scams, and other cyber threats have evolved significantly. As a result, it’s getting much harder for traditional antivirus software to spot and eliminate those risks.
Now, imagine that instead of getting installed on your device, a specific type of malware sneaks into an existing file or program. And while being almost impossible to detect, it can steal confidential information or infect your device’s memory code. Sounds tricky? Well, sadly, that’s exactly what fileless attacks strive to achieve.
So, how does fileless malware work and is there any chance to detect or prevent it? Let’s find out.
What is fileless malware?
Let’s learn the essentials first and kick off with the fileless malware definition.
Fileless malware is any malicious activity that carries out a cyberattack using legitimate software. To be more specific, the concept’s essence lies in its name. While traditional malware types strive to install infected files on users’ devices, fileless attacks target existing native files or programs.
To perform such attacks, hackers seek software vulnerabilities and use social engineering techniques to slip inside. Most often, the malicious code is run directly in the device’s memory, so fileless malware leaves no trace on your hard disk. This makes such viruses nearly impossible to detect when using traditional methods. Unsurprisingly, fileless malware has become one of the most widespread cyber threats. Enisa reports that such viruses are ten times more likely to succeed than other malware types.
To understand if your device is infected with a fileless virus and prevent potential risks, let’s clarify how such viruses work and what dangers they pose.
How fileless malware works
As mentioned above, fileless attacks use software vulnerabilities to compromise the system’s security and infect it with malware. In particular, an attacker can approach Windows frameworks, such as .NET, to detect those weaknesses and target previously installed applications or programs like Microsoft Office, Flash plugins, JavaScript, and so on. The attackers can also access the system via native programs, particularly Windows Management Instrumentation (WMI) and PowerShell.
To better understand how such viruses work, let’s look at a common example of a fileless attack.
- A user clicks on a malicious link or attachment included in a phishing email. Alternatively, it could be an infected pop-up or any other social engineering technique.
- A user is redirected to a malicious website that loads Flash or Java on their device.
- Once Java or Flash launches the PowerShell tool, it starts false scripts and commands.
- The malware gets into the memory code of your device. Now hackers can steal your private data, confidential files, and credentials.
The most common aims of fileless attacks
It’s about time we talk about the most probable outcomes of a fileless attack. The purpose of infecting a device with such malware may vary, yet it’s most likely related to the following malicious intentions.
- Control or track the device. When discovering your system’s vulnerabilities, a hacker may want to keep using it for further attacks, apply specific commands, or spread other types of malware.
- Steal data. Most commonly, an attacker strives to compromise your credentials, personal files, and other sensitive information.
- Set up malicious scripts. Fileless malware allows attackers to run illegitimate code without being noticed. For example, native scripts, such as macros, can be used to manipulate the system and access encrypted files.
Main types of fileless malware
While every fileless attacks the internal system files, their behavior, implementation methods, and goals often differ. Depending on those factors, fileless malware can be divided into four main categories. Let’s look at each of them.
Windows registry attacks
This technique affects legitimate Windows processes and makes malicious code invisible to traditional antivirus software. In particular, such attacks are targeted at Windows PowerShell, which is later used for various illicit activities. PowerShell can store malware for a long time since detecting it is almost impossible.
Memory injection
These fileless viruses are stored in the computer programs’ memory or random access memory (RAM). Such a trick makes malicious code challenging to discover as it is hidden within legitimate and trusted apps. As a result, unwanted activities occur when you’re using a common application, like your browser.
Rootkit fileless attacks
In this case, hackers hide the malicious code in a device’s operating system so that malware can be executed with no files installed. However, this approach is only partially fileless because, initially, an attacker needs to obtain the admin level of access to the user’s device.
Unfortunately, whether you’re dealing with a Windows registry, memory injection, or rootkit attack, it’s extremely difficult to detect. Let’s find out what to look out for when suspecting a fileless virus on your device.
How to detect fileless malware
Most traditional techniques aren’t capable of detecting fileless viruses. Neither standard methods, like whitelisting and sandboxing, nor AI and machine learning techniques are efficient. That’s because fileless malware leaves no visible traces of infection on your hard disk. Instead, it’s carefully hidden in your device memory and native Windows tools.
As a result, there are few result-driven methods of identifying fileless characteristics. Let’s briefly discuss each.
Updated Windows Defender
Due to the rapidly growing number of fileless attacks, Microsoft optimized and updated the Windows Defender tool. Its Anti-Malware Scan Interface (AMSI) can monitor suspicious behavior, scan the system’s memory, and provide boot section protection. As a result, the latest version of Defender has a better chance of bringing fileless viruses to light.
Indicators of Attack (IoAs)
Instead of trying to determine how a virus has gotten into the system, this technique inspects the worrying signs of a potential attack. This approach comprehensively verifies internal code execution and its abnormal behavior.
Threat hunting
An organization may hire a professional team to conduct threat hunting if a fileless attack is suspected. In this case, experts will inspect large volumes of your company’s data on multiple devices, using advanced techniques and testing tools. They can spot existing viruses and help you prevent future attack attempts.
How to prevent fileless malware attacks?
Of course, preventing a cyber threat is always better than coping with its consequences. Let’s look at several simple yet effective steps you should take to establish fileless malware protection.
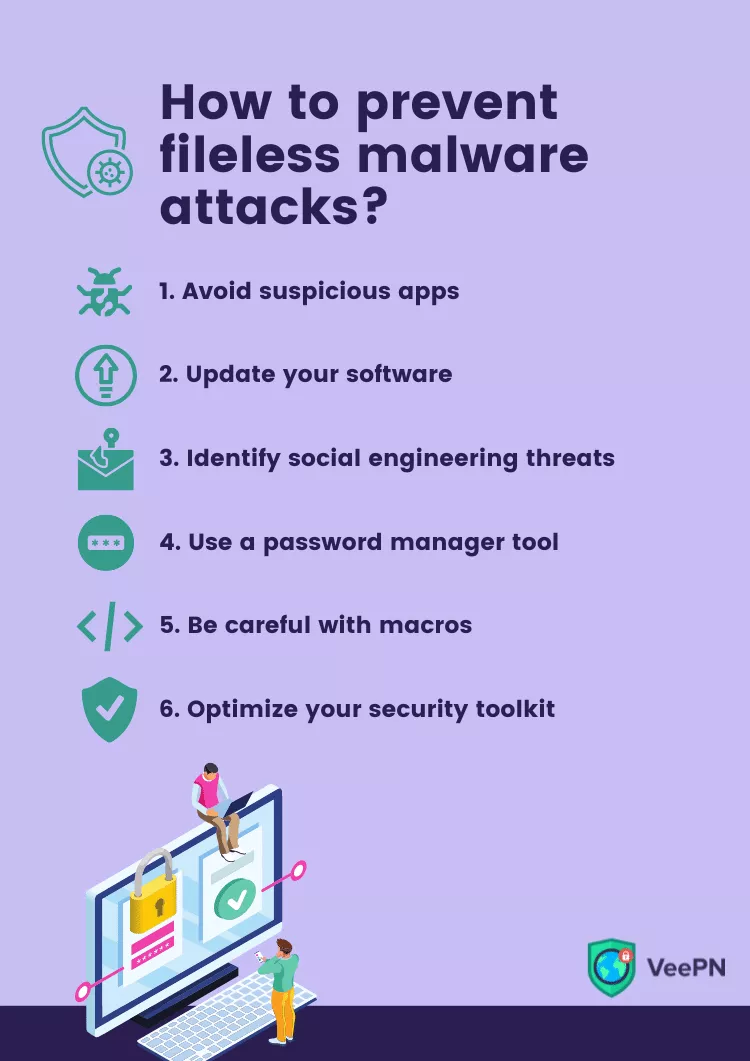
1. Do not download and install suspicious apps
It all starts with a link, popup, or email attachment that may turn out to be a trap set by a hacker. Do your best to avoid any unverified websites and distrustful files. For an organization, it’s important to train staff to stick to the basic rules of cyber hygiene.
2. Regularly update your software
A bug or virus may sit quietly in your device’s memory for months, even years, if you neglect updating your operating system and programs. Using the latest software versions is a simple trick that can save you tons of effort and prevent numerous threats.
3. Learn to identify social engineering techniques
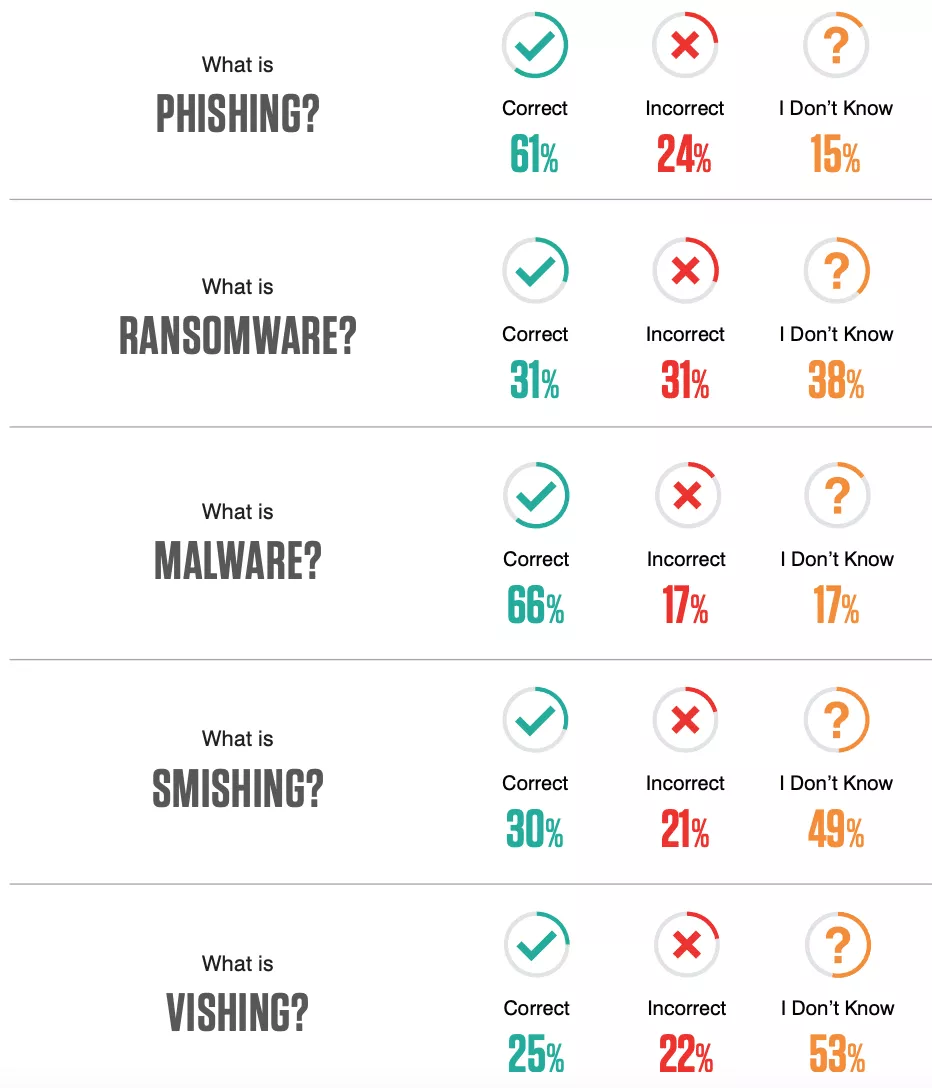
Did you know that nearly 40% of people aren’t aware of what phishing is? Yes, that’s right, users often fall victims to scams simply because they aren’t informed about the specifics of those threats. So it’s worth learning social engineering techniques’ characteristics to avoid their harmful effects.
4. Adopt a password manager tool
A powerful password manager can be a lifesaver. For large businesses and organizations, it’s crucial to create strong passwords for all employees’ accounts and store them in a safe place. As follows, it will be much more difficult for hackers to compromise your company’s cybersecurity, steal credentials, and spread fileless viruses.
5. Be careful with macros
In computer programming, macros are rules or patterns that replace some pieces of code to allow for more streamlined, automated commands and actions. Unfortunately, this tool is often used in fileless malware attacks to run malicious code on your device. To prevent this, do not overuse macros and enable them only for trusted files and documents.
6. Optimize your security toolkit
You can enhance your cybersecurity and avoid various risks, including phishing attacks and fileless malware, by adopting some additional tools. In particular, using a virtual private network (VPN) is one of the most effective ways to shield your device and network. VPN doesn’t only protect your online privacy by encrypting and rerouting your traffic, but also keeps you away from malicious websites, dangerous links, and potentially harmful pop-ups.
Enhance your cybersecurity with VeePN
Striving to avoid malware and securing your browsing activities? Check out VeePN. This powerful VPN tool will protect your data thanks to reliable AES-256 encryption. It also provides the NetGuard feature that will help you stay away from dangerous websites, stop unwanted online trackers, and omit suspicious pop-up ads. Wait no more and try VeePN to safeguard yourself against fileless viruses.
FAQs
What is an example of fileless malware?
One of the earliest fileless malware examples was Duqu 2.0 having infected Kaspersky Labs in 2015. In 2017, a fileless virus called Operation Cobalt Kitti performed a massive attack against an Asian corporation. Some other well-known examples of fileless malware are Meterpreter, UIWIX, and WannaMine.
How is fileless malware detected?
There are not many effective methods of detecting fileless attacks. Here are some of the most result-driven ones:
- The latest version of Windows Defender
- Indicators of Attack (IoAs)
- Threat hunting
For more details, read this article.
VeePN is freedom