What is Whitelisting? Safeguarding Your Digital World
Whitelisting is a powerful cybersecurity tool that outdoes blacklisting in scope and effectiveness. Such drastic measures, however, may not be necessary for most people, but they are crucial for controlling access systems within larger organizations. Generally, the whitelist approach best suits larger organizations that deal with a lot of sensitive information. But that doesn’t mean you can’t benefit from the practice. Let’s discuss whitelisting, its uses, different variations, and how it can help protect your network or device.
If you use the internet without a VPN, you might as well post your browsing history to social media for everyone to see. Anyone who wants to monitor your activity — the government, your internet service provider (ISP), certain social media sites — can easily do so with the right motivation. Luckily, protecting your privacy is as simple as installing VeePN’s Chrome extension. The extension encrypts your traffic and prevents tracking while offering access to over 2500 secure VPN servers in over 70 countries. Get VeePN’s Chrome extension now and protect your privacy the easy way.

What is a whitelist (allowlist)?
Whitelists contain items, such as applications or websites, that you or a network administrator has pre-approved within an application or private network. With a whitelist in place, you’ll experience restrictions when trying to access unsanctioned services. The strictness of the practice makes whitelisting an effective security measure in sensitive environments. An application whitelist ensures that only authorized applications can run on a device, effectively blocking malicious software and unauthorized programs.
While blacklisting relies on traditional antivirus software to identify and block known threats, whitelisting involves a guilty until proven innocent approach where you must judge and assess each item before granting access. Protecting government offices, corporate environments, and schools are common whitelisting examples could all benefit from a whitelisting approach to cybersecurity.
However, the method does have some disadvantages. If a network administrator restricts the majority of apps, sites, and services and only allows specified items, they risk hamstringing users and preventing them from completing critical tasks. If you do want to utilize whitelisting, you should formulate a practical method for managing exceptions and maintaining productivity within your organization.
What is the purpose of whitelisting?
Whitelisting is a cybersecurity measure designed to protect networks or devices from malicious software and unapproved apps or block access to unauthorized content. For example, a government network administrator may maintain a whitelist of pre-approved apps to prevent accidental — or intentional — malware infections. Institutions can also use whitelisting as a censorship tool. By controlling network access, whitelisting ensures that only authorized users and devices can connect to the network, thereby enhancing security.
Some schools and organizations may keep blacklists of restricted apps and sites. But the internet is a big place, and, with over half a million new websites created each day, maintaining a list of every questionable site in existence takes serious effort. That’s where whitelisting comes in. A well-curated whitelist will block out the worst of the web while still allowing you to perform all necessary tasks.
Benefits of Whitelisting
Whitelisting offers a range of benefits that can significantly enhance the security and efficiency of your network or device. By allowing only pre-approved applications, websites, or IP addresses, you can create a controlled environment that minimizes the risk of malicious code and unauthorized access. This approach is particularly useful for organizations that handle sensitive information, as it provides an additional layer of protection against cyber threats.
One of the key advantages of whitelisting is its ability to block malicious code before it can infiltrate your system. Unlike blacklisting, which requires you to identify and block known threats, whitelisting takes a proactive approach by only allowing trusted entities. This makes it much harder for malware and other harmful software to gain a foothold.
Whitelisting also helps in maintaining productivity by ensuring that only approved applications and websites are accessible. This can prevent employees from wasting time on non-work-related sites and reduce the risk of downloading unauthorized software that could compromise the network.
In addition to these security benefits, whitelisting can also improve the performance of your network. By limiting access to only essential applications and websites, you can reduce bandwidth usage and ensure that critical resources are available when needed.
Types of Whitelisting
While the meaning is fairly universal, different types of whitelisting services exist. Technically, you or your network administrator could create a whitelist for anything you access on your device, including apps, websites, or other services. Some software, such as a VPN client or firewall, may include its own whitelisting tools.
Application whitelists restrict the execution of applications to only those that are approved, providing an effective security measure for larger workplaces.
Here are some common whitelist types:
- IP address
- Application
- Domain/website
- VPN
Let’s discuss each whitelisting variant in more detail.
IP whitelisting with dynamic IP addresses
IP whitelisting generally refers to authorizing IP addresses so specific users can access a private network. For example, if you work remotely, you may need access to the company server. In which case, whitelisting specific IP addresses is an effective method for granting permission to the right people while avoiding unauthorized logins.
Unless you’re using a VPN, your ISP provides you with a public IP address. Because your public IP changes when you reset your router, you’ll either need to obtain a static address from your provider or use a VPN for this whitelisting method to make sense.
Application whitelisting
Application whitelisting prevents unauthorized applications from installing or running on a device or network. The practice makes sense in some governmental, corporate, and educational contexts where users only need certain apps to perform their duties. When you disallow most software, the chances of contracting malware are low. To implement application whitelisting, you can use standard vendor lists or model clear systems to ensure only authorized applications are allowed.
Domain and site whitelisting
Domain — or website — whitelisting is the practice of allowing access to specific sites within an application or network. A network administrator may block unlisted sites completely, or an application could treat entries on the whitelist differently to others. For example, whitelisting a domain in your ad blocker allows relevant pages to display advertising. Limiting access to irrelevant or distracting sites within an organization can help boost productivity.
VPN whitelisting
When you whitelist a domain in your VPN client, you instruct the software to exclude that website from its processes, which means splitting your traffic in two. Your device accesses whitelisted websites over the internet as normal, while other traffic undergoes encryption and routes through the VPN server. Whitelisting — or split tunneling — allows you to encrypt your most sensitive connections while maintaining speed in other areas.
VeePN’s Chrome browser extension allows you to whitelist websites for greater control over how your VPN behaves. Here’s how you can whitelist websites in VeePN:
- Sign up for VeePN
- Get the VeePN Chrome extension
- Launch the extension and click on the menu in the top left corner
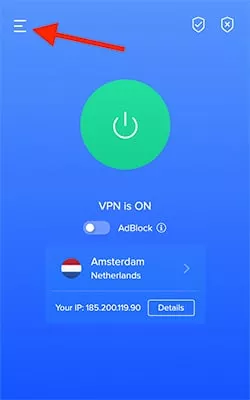
- Go to Settings
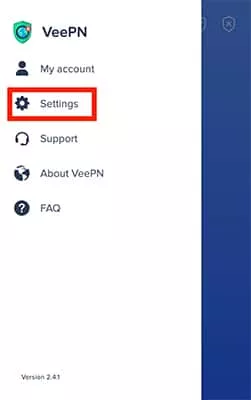
- Scroll down to Exclude websites
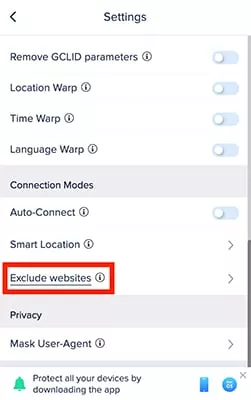
- Choose websites you want to bypass when the VPN is on
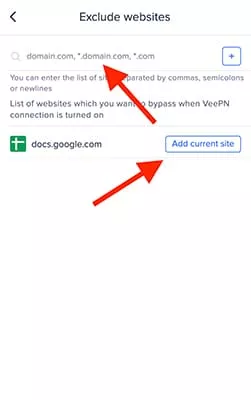
Ideally, you should only whitelist domains that don’t store or require you to enter any private information. When using a VPN, your banking provider and other services that deal with sensitive data shouldn’t be on your whitelist without good reason.
You may, however, want to whitelist particular streaming sites and other services that require a lot of bandwidth to function well. In most cases, you’ll have to decide if the risk is worth the reward when excluding a domain from the protection of your VPN.
Advertising and Email Whitelisting
Whitelisting can also be a game-changer in the realms of advertising and email marketing. By allowing only approved IP addresses or email addresses to access your network or system, you can significantly reduce the risk of spam and malicious emails. This not only enhances your overall security but also improves the efficiency of your email marketing campaigns.
In email marketing, whitelisting ensures that legitimate emails are not flagged as spam, thereby increasing the chances of important messages reaching their intended recipients. This can be particularly beneficial for businesses that rely on email communication for customer engagement and marketing efforts.
When it comes to advertising, whitelisting can help you target your ads more effectively. By allowing only approved IP addresses to access your network, you can ensure that your ads are being shown to the right audience. This targeted approach can improve the overall effectiveness of your advertising campaigns and reduce waste, ensuring that your marketing budget is well-spent.
Implementing Application Whitelisting
Implementing application whitelisting might seem like a daunting task, but breaking it down into manageable steps can simplify the process. The first step is to identify which applications are essential for your operations. Create a comprehensive list of these approved applications, ensuring that all employees are aware of which software is permitted.
Next, you’ll need to configure your systems to enforce this whitelist. This is where application whitelisting software comes into play. These tools can be set up to block any applications that are not on your approved list, providing an automated way to maintain security. The software can also help in monitoring and managing the whitelist, making it easier to keep track of which applications are allowed.
Regularly reviewing and updating your whitelist is crucial to ensure its effectiveness. This involves monitoring system logs to identify any unauthorized applications that may have slipped through the cracks. By keeping your whitelist up-to-date, you can adapt to new threats and ensure that your security measures remain robust.
Challenges of IP Whitelisting
While IP whitelisting is a powerful security measure, it does come with its own set of challenges. One of the most significant issues is dealing with dynamic IP addresses. Unlike static IP addresses, which remain constant, dynamic IP addresses can change frequently. This variability can make it difficult to maintain an effective IP whitelist, as the addresses you need to allow may change over time.
To tackle this challenge, businesses can use several strategies. One approach is to whitelist IP address ranges instead of individual addresses. This method provides more flexibility and can accommodate changes in IP addresses without compromising security. Another effective technique is DNS-based whitelisting, which uses the domain name system to resolve IP addresses. This approach can be more reliable than relying on static IP addresses.
Combining IP whitelisting with other security measures, such as authentication and authorization, can also enhance your network’s security. By ensuring that only authorized devices and systems can access your network, you can add an extra layer of protection, even if the IP address changes.
In conclusion, while IP whitelisting presents certain challenges, these can be effectively managed with the right strategies and tools. By understanding and addressing these issues, you can leverage the full benefits of IP whitelisting to enhance your network security.
Whitelisting is extreme but effective to block malicious code
When device or network security is critical, whitelisting may be the best option for keeping you or your organization safe. If you do decide to create a whitelist, being practical is important. The potential for lost productivity is massive if you don’t make a list that’s fair, balanced, and allows for the right amount of freedom. In marketing, influencer whitelisting can maximize ROI by allowing brands to leverage the reach of influencers for targeted advertising campaigns.
FAQ
Whitelisting only allows pre-approved services, while blacklisting blocks known threats, making whitelisting ideal for highly secure systems.
Yes, many mobile devices and apps allow application-specific whitelisting, especially for parental control and productivity apps.
While whitelisting is very effective, it requires regular updates to ensure that the whitelist remains secure and practical.
Whitelisting may improve speed by limiting the number of accessible websites, reducing bandwidth strain, especially in a corporate setting.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






