What is a Proxy Server and How Does It Work?
You may have heard that proxy servers can help mask your IP address and give you access to content that may be restricted in your location. But did you know that there’s so much more to them than just that? In this ultimate guide, we’ll explore everything related to proxies, from the proxy server definition to the “VPN vs proxy server” battle, as these two technologies are often confused. Let’s dive in!
What is a proxy server?
Here’s the simplest proxy server definition — it’s a middleman between your device and the Internet, which lets you access websites or services while hiding your real IP address (your device’s “home address” online) and location.
A proxy server example is SOCKS5 proxy that can hide your IP address by redirecting your Internet traffic through another server.
How does a proxy server work?
When you use the Internet, your device communicates with the servers of the websites you visit using your IP address. Websites can use this address to determine your location and monitor your online activities, which can lead to access restrictions.
To protect your privacy and bypass these restrictions, you can use a proxy server as a middleman between your device and the website. All data, including requests, passes through the proxy server, which replaces your IP address with its own. This makes it appear as though you’re browsing from the proxy server’s location, rather than your own.
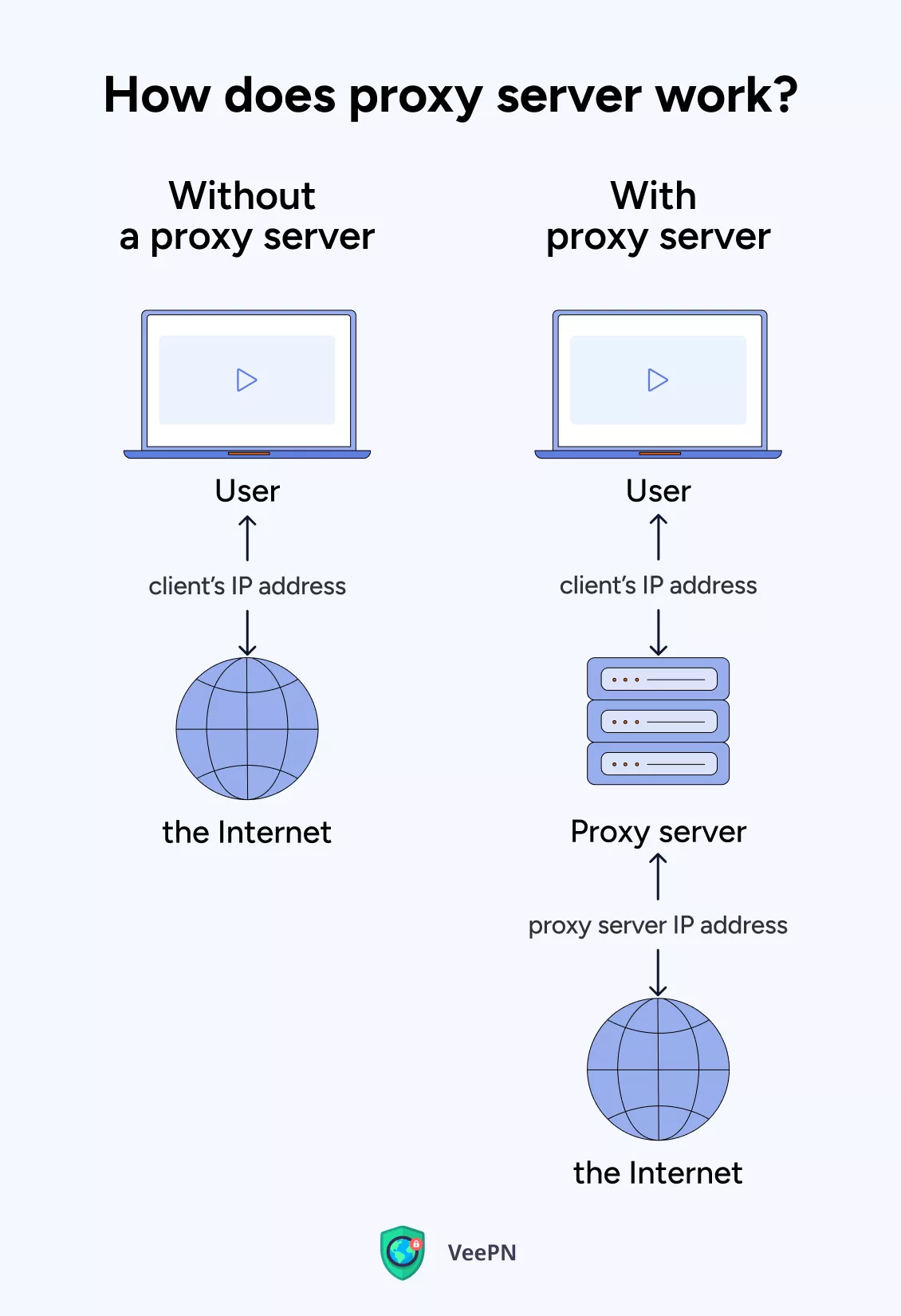
But let’s walk through this process step-by-step:
- You type a website’s address into your browser.
- The request goes to the proxy server instead of the website.
- The proxy server then sends the request to the website’s server.
- The website’s server responds with the website’s data.
- The proxy server then sends the website’s data back to your browser.
Are proxy servers legal?
Yes. But note that the legality of their use can depend on how they are being used. For example, using a proxy server to access illegal content or do something unlawful won’t be legal. Besides, some organizations or websites may prohibit the use of proxy servers on their networks or platforms.
Always check local laws and regulations before using a proxy server.
The pros and cons of using proxy servers
Proxy servers come with both good and bad. Let’s find out what benefits of using a proxy server as well as risks are there.
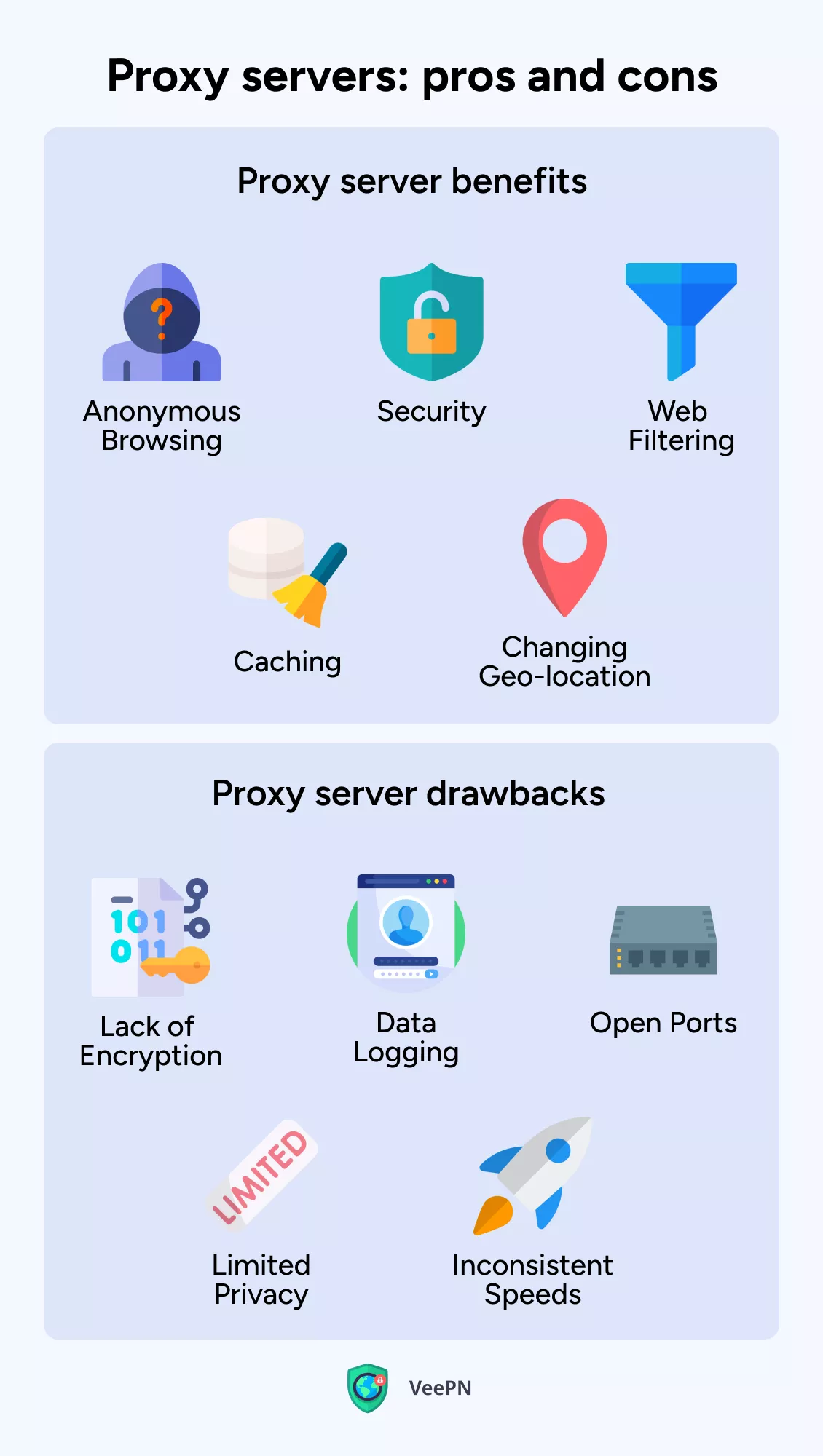
Why use a proxy server: benefits of this solution
Here’s what is a proxy server used for:
| Anonymous browsing | Anonymous proxies hide your IP address, letting you browse the Internet without revealing your identity. |
| Changing geo-location | A new IP address lets you avoid blocks based on your location. |
| Security | Different types of proxies help improve security. For example, HTTPS proxies encrypt connections to web pages to make them more secure. |
| Web filtering | Organizations can use some proxies to restrict access to certain websites or to monitor employee Internet use. |
| Caching | Proxy servers can speed up your Internet connection by caching popular websites. This reduces the number of requests made to the server, which makes browsing faster. |
What are the risks of using a proxy server?
In the meantime, proxies also come with some cyber threats you should be aware of. Here are some common risks of using a proxy server.
| Lack of encryption | Unencrypted proxies operate through an unsecured connection that attackers can easily intercept. This can compromise sensitive data like usernames and passwords and lead to data breaches and identity theft. |
| Data logging | Proxy servers may store users’ IP addresses and web request data, which can be sold to other parties. Before using a proxy, it’s crucial to read the terms and conditions. |
| Open ports | Most proxies run on open ports. They can be exploited through security vulnerabilities and also boost the attack surface. |
| Limited privacy | Free proxies often operate over unsecured networks and ad-based revenue models, allowing anyone to “listen” to user traffic. These ads can also contain viruses or malware. |
| Inconsistent speeds | Free proxies can be overloaded with traffic, causing server lags and slow speeds. |
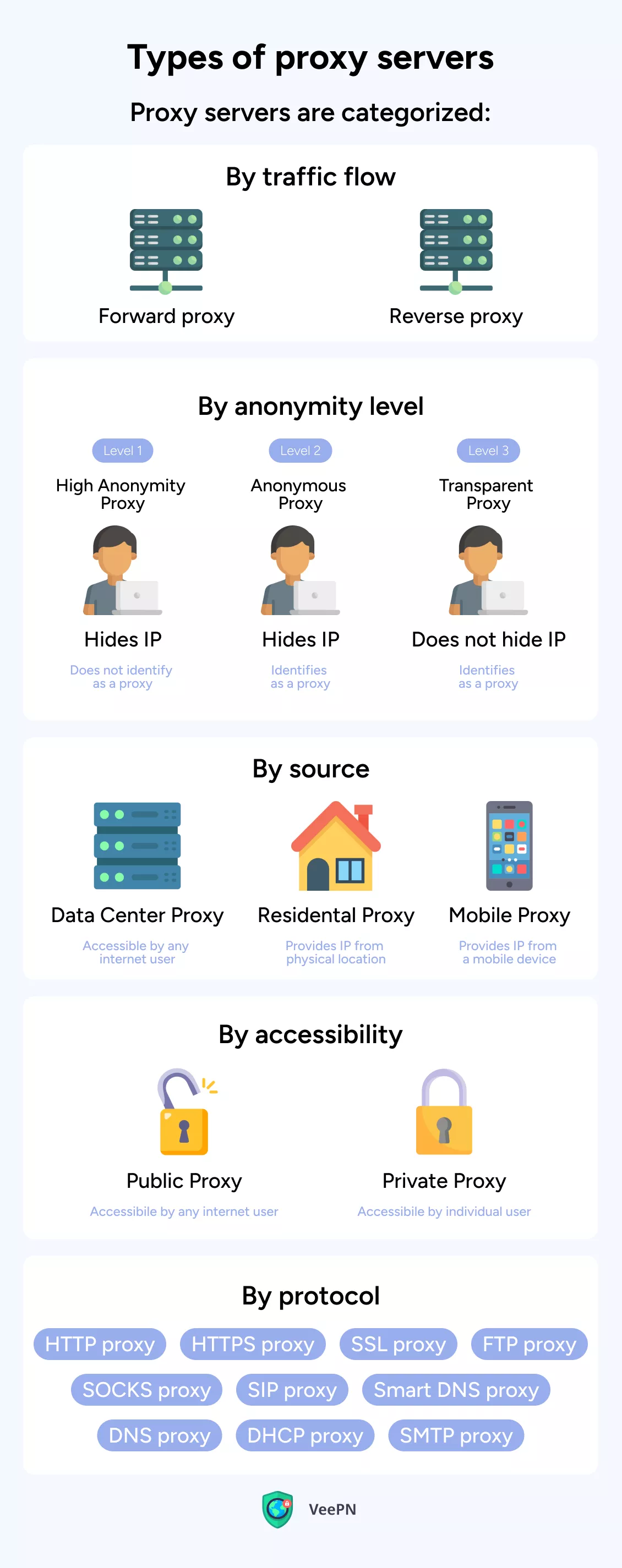
What are the different types of proxy servers?
Proxy servers come in different types, classified by their traffic flow, anonymity level, application, service, IPs, and accessibility. Here are some of the main types of proxy servers.
By traffic flow
1. Forward proxy server
📝 Definition: Often referred to as a plain “proxy,” a forward proxy is an intermediary server that sits between a client (like a web browser) and the Internet, forwarding client requests to Internet servers and returning the servers’ responses to the client.
🛠️ How it works: The forward proxy server checks if a user’s request meets the organization’s policies. If it’s allowed, the request is sent to the website’s server and its response is sent back to the user through the forward proxy server.
🎯 Main use cases:
- To control and filter Internet traffic, allowing organizations to restrict access to certain websites or types of content
- Monitor Internet use for security or compliance purposes
- Cache frequently accessed content, improving performance and reducing bandwidth usage
2. Reverse proxy server
📝 Definition: An intermediary server that sits between Internet servers and users, forwarding user requests to servers and returning the servers’ responses to users.
🛠️ How it works: Reverse proxy intercepts user requests and forwards them to the server hosting the website. The server processes the request and sends its response back to the reverse proxy server, which then sends it back to the client.
🎯 Main use cases:
- To improve website performance and security
- Cache frequently accessed content to reduce server load and improve response times
- Perform security checks on incoming traffic, like filtering out unwanted traffic, before allowing it to reach the web server
By anonymity level
1. Transparent proxy
📝 Definition: A type of proxy that doesn’t change the request or response except for authentication and identification. It secretly takes the user’s request for Internet resources and forwards it to the destination without their knowledge.
🛠️ How it works: A transparent proxy server forwards user requests to websites without the user knowing. The website responds directly to the user, but the user doesn’t know that the request went through the transparent proxy.
🎯 Main use cases:
- Commonly used by organizations to monitor user activity and restrict access to certain websites
- To speed up website access by caching frequently requested content
Note that because the user is unaware of the proxy, it doesn’t provide any privacy or anonymity benefits.
2. Anonymous proxy
📝 Definition: A proxy server that hides the user’s IP address from the website they are accessing, providing a higher level of privacy than a transparent proxy.
🛠️ How it works: When a user sends a request through an anonymous proxy, the proxy server forwards the request to the website on the user’s behalf. The website sees the IP address of the anonymous proxy server instead of the user’s real IP address. This allows the user to browse the web anonymously.
🎯 Main use cases:
- To protect privacy online and bypass content filters or geo-restrictions
- Can also be used for malicious purposes, such as to conduct cyber attacks or evade law enforcement
3. High anonymity proxy
📝 Definition: Also known as an elite proxy, it’s a type of proxy server that hides the IP address of the user and presents itself as a regular user to the web server.
🛠️ How it works: When a user connects to a website through a high anonymity proxy, the proxy server hides the user’s IP address and replaces it with its own IP address. This way, the web server can’t trace the request back to the user, and the user’s identity remains anonymous.
🎯 Main use cases:
- For online privacy and security purposes
- To bypass Internet censorship and access geo-restricted content without revealing the user’s location or identity
- To protect against online tracking and monitoring
By source
1. Data center proxy
📝 Definition: A type of proxy server that uses IP addresses provided by data center providers, rather than an Internet service provider (ISP).
🛠️ How it works: Routes requests through servers located in data centers and often uses dedicated IP addresses that are not shared with other users. These servers can handle a large volume of requests and provide users with a high level of anonymity and speed.
🎯 Main use cases:
- To gather data for various purposes, such as web scraping, market research, and ad verification
- For web activities that require a high level of anonymity
- To bypass content restrictions or geo-blocks
2. Residential proxy
📝 Definition: A type of proxy server that uses an IP address provided by an ISP to mask a user’s real IP address.
🛠️ How it works: When a user sends a request through a residential proxy, the request appears to be coming from a legitimate residential IP address, rather than a data center IP address.
🎯 Main use cases: For web scraping, social media management, and other activities that require multiple requests to be made from different IP addresses to avoid being detected and blocked.
3. Mobile proxy
📝 Definition: A type of proxy server that uses a mobile device’s Internet connection to access the Internet.
🛠️ How it works: When a user goes online through a mobile proxy, their Internet traffic is routed through the mobile carrier’s network instead of their own ISP.
🎯 Main use cases:
- For web scraping, ad verification, and accessing geo-restricted content
- Can also provide enhanced security and privacy when browsing the Internet
- Bypass network restrictions
By accessibility
1. Public proxy
📝 Definition: a type of proxy server that can be accessed by anyone online without any authentication. Due to their open accessibility, they are often slow, unreliable, and used for malicious activities like hacking, phishing, and spamming.
🛠️ How it works: You know, the usual — a user connects their device to a public proxy server. The server then sends the user’s requests to the website and sends the website’s response back to the user.
🎯 Main use cases:
- Bypass content filters or access geo-restricted content.
- For web scraping and testing and debugging web applications.
2. Private proxy
📝 Definition: A type of proxy server only accessible by authorized users.
🛠️ How it works: The process is similar here — a private proxy server receives the authorized user’s requests and then forwards them to the destination website. The response from the website is sent back to the proxy, which in turn sends it back to the user.
🎯 Main use cases:
- For security purposes
- For web scraping
- For accessing geo-restricted content
By protocol
1. HTTP proxy
📝 Definition: Also known as a web proxy, it’s a type of proxy server that handles HTTP requests and responses between a client and a server. HTTP proxies let users browse the web with a different IP address but offer no extra privacy or security.
🛠️ How it works: HTTP proxy intercepts a client’s request and evaluates it. It serves the request from its cache or forwards it to the appropriate server. Once the server responds, the proxy intercepts the response and serves it to the client or caches it.
🎯 Main use cases:
- To mask a user’s IP address and encrypt web traffic
- To block certain types of content or restrict access to certain websites
- To cache frequently accessed websites, which can improve performance and reduce bandwidth usage
2. HTTPS proxy
📝 Definition: A type of proxy server that is used to handle encrypted traffic (HTTPS).
🛠️ How it works: When a client sends an HTTPS request, the proxy server first establishes an SSL/TLS connection with the client and decrypts the request. It then evaluates the request and either serves it from its cache or forwards it to the appropriate server. Once the server responds, the proxy server intercepts the response, encrypts it, and sends it back to the client.
🎯 Main use cases:
- To provide secure access to the Internet and protect sensitive information from prying eyes
- To filter web traffic and to enforce security policies
3. SSL proxy
📝 Definition: A broader term that encompasses proxies that handle SSL/TLS connections, including HTTPS proxies.
🛠️ How it works: Intercepting and decrypting SSL/TLS requests from clients, SSL proxy can serve requests from its cache or forward them to the appropriate server. When the server responds, the proxy encrypts and sends the response back to the client.
🎯 Main use cases:
- Used in corporate environments to monitor and control employee Internet usage and protect against security threats
- For content filtering, compliance monitoring, and troubleshooting network issues related to SSL/TLS traffic
- Help organizations comply with regulatory requirements by allowing them to inspect encrypted traffic
4. FTP proxy
📝 Definition: An FTP (File Transfer Protocol) proxy is a server that sits between a client and an FTP server to control and filter file transfers.
🛠️ How it works: The client sends FTP commands to the proxy, which then relays them to the FTP server on behalf of the client. The proxy can perform functions like caching files, filtering file types, and enforcing access control policies.
🎯 Main use cases: Commonly used in enterprise environments to manage and secure file transfers.
5. SOCKS proxy
📝 Definition: A server that allows clients to bypass firewalls and access network resources.
🛠️ How it works: The client establishes a connection with the SOCKS (SOCKets Secure) proxy server and sends its request. The proxy server then routes the request to the destination server and returns the response to the client.
SOCKS proxies can work with any protocol, but they don’t inspect the data sent.
🎯 Main use cases:
- For anonymous browsing
- Accessing restricted content
- Bypassing network restrictions
6. SIP proxy
📝 Definition: A SIP proxy is a server that manages Session Initiation Protocol (SIP) traffic between two endpoints.
🛠️ How it works: The SIP proxy receives SIP requests from clients and forwards them to the appropriate endpoint. It can also modify SIP headers, perform routing functions, and enforce security policies.
🎯 Main use cases: Commonly used in Voice over IP (VoIP) systems to manage call signaling and provide security features like authentication and encryption.
7. Smart DNS proxy
📝 Definition: A type of proxy server that routes a user’s DNS requests through a remote server to access geographically restricted content.
🛠️ How it works: When a user tries to access a website, the Smart DNS proxy server intercepts the DNS query and resolves it with a DNS server that is located in a country where the content isn’t restricted. This allows the user to access the content they want.
🎯 Main use cases: Commonly used to access streaming services that may be restricted in certain countries.
8. DNS proxy
📝 Definition: A type of proxy server that intercepts Domain Name System (DNS) requests from a client and forwards them to a DNS server.
🛠️ How it works: When a client sends a DNS query, the DNS proxy intercepts the request and forwards it to a DNS server. The DNS server resolves the query and sends the response back to the DNS proxy, which then forwards it to the client.
🎯 Main use cases: To improve network performance by caching DNS requests and reducing DNS resolution times.
9. DHCP proxy
📝 Definition: A Dynamic Host Configuration Protocol (DHCP) proxy is a type of proxy server that acts as an intermediary between DHCP clients and DHCP servers.
🛠️ How it works: Similar here — when a client sends a DHCP request, the DHCP proxy gets the request and forwards it to a DHCP server. The DHCP server assigns an IP address to the client and sends the response back to the DHCP proxy, which then forwards it to the client.
🎯 Main use cases: Commonly used in large networks where multiple DHCP servers are present to reduce the amount of broadcast traffic on the network.
10. SMTP proxy
📝 Definition: Simple Mail Transfer Protocol proxy is a type of proxy server that acts as an intermediary between an email client and an email server.
🛠️ How it works: When an email client sends an email, the SMTP proxy intercepts the message and forwards it to an SMTP server. The SMTP server delivers the email to the recipient’s email server, and the SMTP proxy gets the response and sends it back to the email client.
🎯 Main use cases: Commonly used in email security solutions together with a DMARC policy to filter out spam and malware and to improve email deliverability.
Finally, proxy servers are often confused with a virtual private network (VPN), but these are two different technologies that can interconnect. Let’s learn the difference.
VPN vs proxy server: What’s the difference?
The main difference between a proxy server vs a VPN is that a VPN creates a private, encrypted connection between your device and a remote server, while a proxy simply forwards your requests to the Internet on your behalf.
Proxies are typically used to mask the user’s IP address or to filter Internet content, whereas VPNs are used to protect the user’s privacy and security. A VPN encryption encompasses all Internet traffic and makes it difficult for others to intercept or track user’s online activities. Simply put, a VPN is like a secure envelope that hides the contents of your letter from prying eyes, while a proxy is like a postman who reads your letter before delivering it to the recipient.
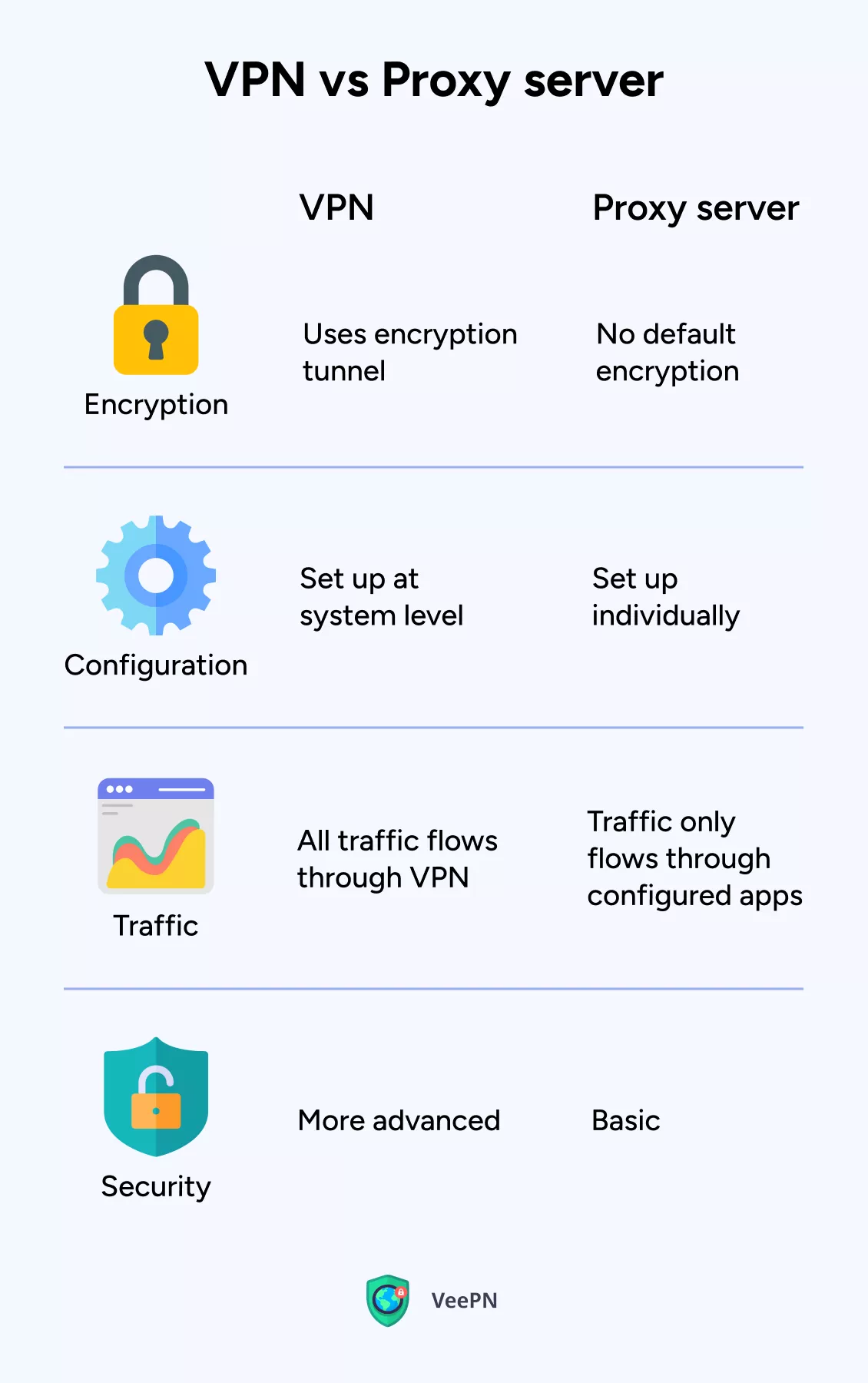
But although there are differences between a VPN and a proxy, a VPN can act as a proxy. VeePN VPN is one such service.
Boost your online security with VeePN: avoid blocks effectively
VeePN reroutes your Internet traffic through a VPN server and makes it appear like you’re accessing the Internet from a different location with your IP address changed. This is similar to how a proxy server acts, but with the added benefit of encrypting user’s traffic and a higher level of security. For extra security, you can also go for the Double VPN feature.
That said, you can get all the benefits in one package with a reliable VPN — protect your data with the strongest encryption method and bypass online restrictions with VeePN’s servers across 89 locations in 60 countries, including the US, Argentina, Italy, Greece, Egypt, Poland, and many more. Choose your pricing plan and see for yourself. No complicated setups and risks.
VeePN is freedom





