9 Effective VPN Alternatives: When to Use Them
Virtual private networks (VPNs) are definitely a good solution for accessing various content securely online. However, a good VPN can be costly, difficult to use or just not something you’re looking for. That’s why many users search for viable VPN alternatives. But finding the right solution can turn into a serious quest.
To help you out, we’ve prepared a detailed list of some common solutions that can be a good substitution for a legacy VPN app. Overviews of each alternative, pros and cons, and what purposes they can serve — you’ll find all this information one scroll below!

VPN alternatives explained
Overall, there are 9 secure VPN alternatives for different purposes. Let’s discuss all of them.
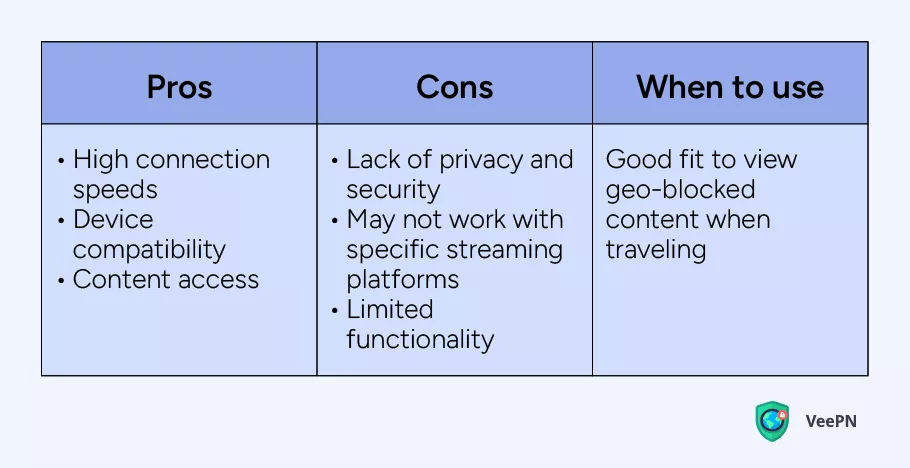
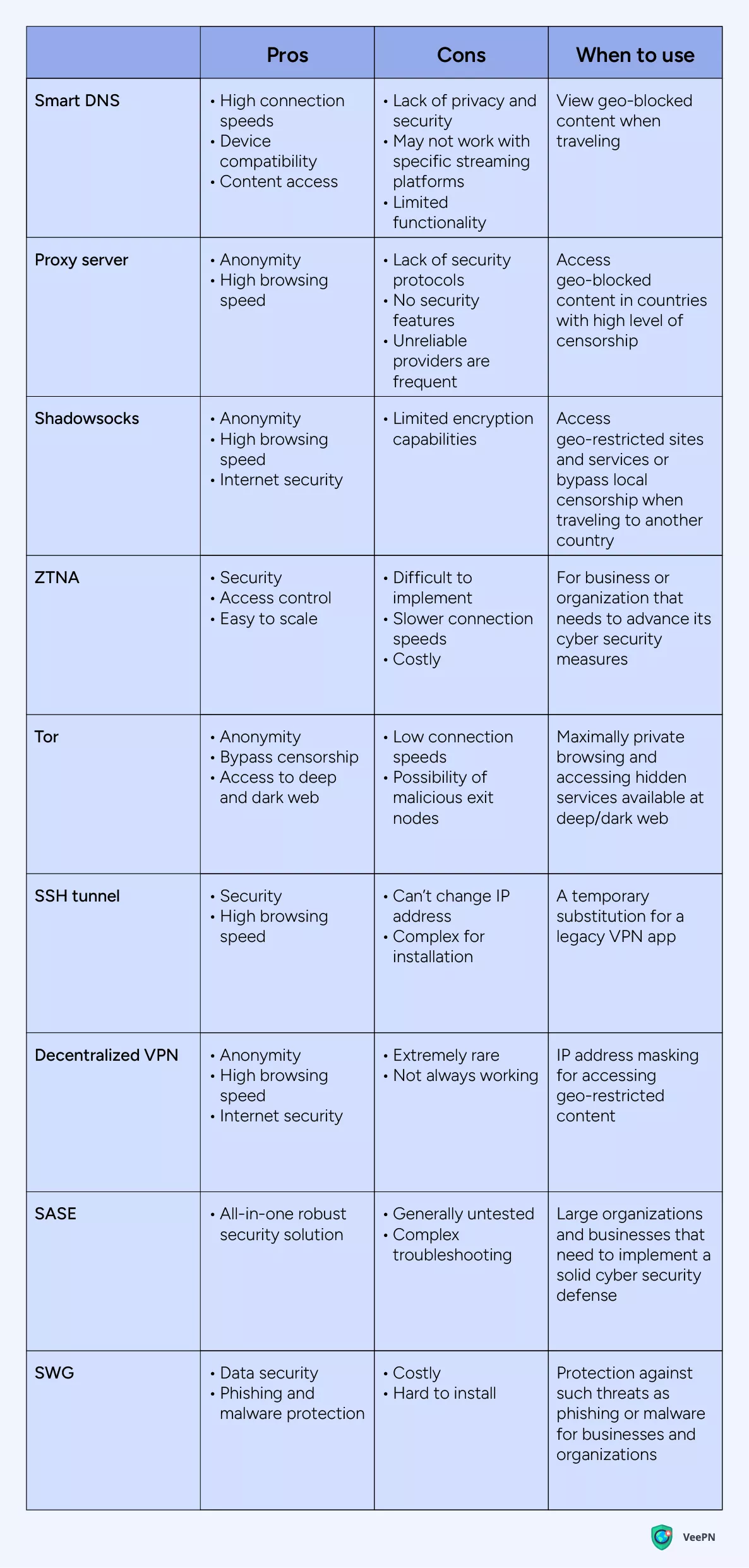
Smart DNS
Smart Domain Name System (DNS) is a technology that lets you bypass geo-restrictions to quickly access various content limited to a specific region. But Smart DNS doesn’t pass all your Internet traffic through a remote server as VPN apps do. Instead, a smart DNS just sends requests to a specific site or application you choose.
Also, smart DNS doesn’t encrypt your data, which is why it’s better to be used with secure and legitimate sites and services only. Compatible with almost all platforms and operational systems, smart DNS is a perfect solution for accessing streaming platforms while you travel to a location where your favorite content may be unavailable.
Note: VeePN is the VPN service not intended to be used for bypassing copyright regulations or other illegal behavior. For more details, please read the VeePN Terms of Service.
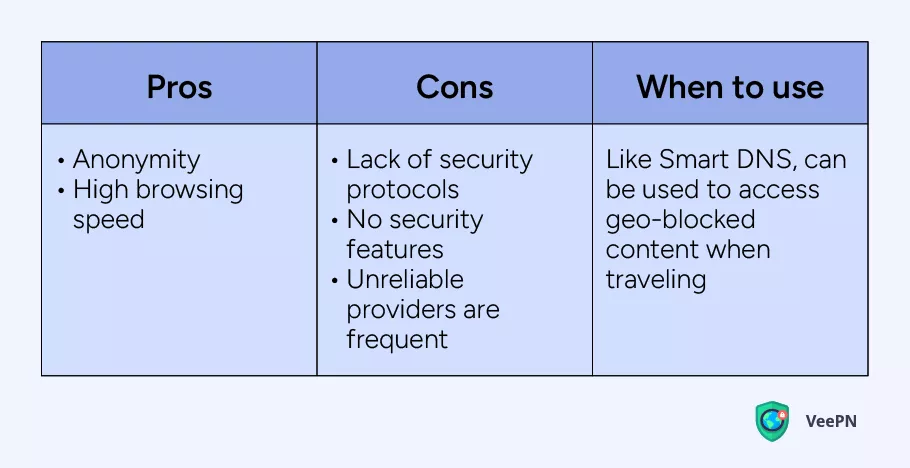
Proxy server
Imagine your traffic goes from point A to point B by a straight road, where A is your device, and B is a website you want to access. But if the site or service is unavailable in your area, the road is blocked with a turnpike, so you can’t reach point B. In this context, a proxy server is a roundabout way to point B.
Just like smart DNS, a proxy server is a good solution for accessing your favorite content in a place where a relatable site or service is unavailable. But unlike VPN, a proxy server doesn’t encrypt your Internet traffic, so it’s only a good option for accessing content and services you trust. On top of that, you can’t constantly rely on proxy server providers as they commonly don’t offer uninterrupted performance and customer support round the clock.
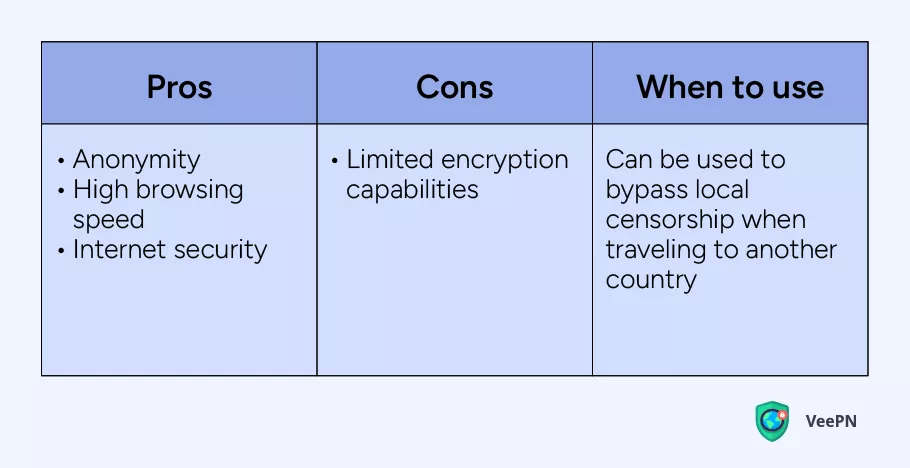
Shadowsocks
Shadowsocks is a separate proxy server protocol that helps to establish a connection between your device and a remote proxy server. That’s why it offers the same benefits as a proxy server while also encrypting your Internet traffic.
In such a way, Shadowsocks is also a reliable solution for accessing restricted content but with advanced security, so you may explore sites and services you barely know. But keep in mind that this protocol isn’t as secure as VPN apps that usually offer the most solid data encryption. If you’re relying on Shadowsocks encryption only, you still put your Internet privacy at risk.
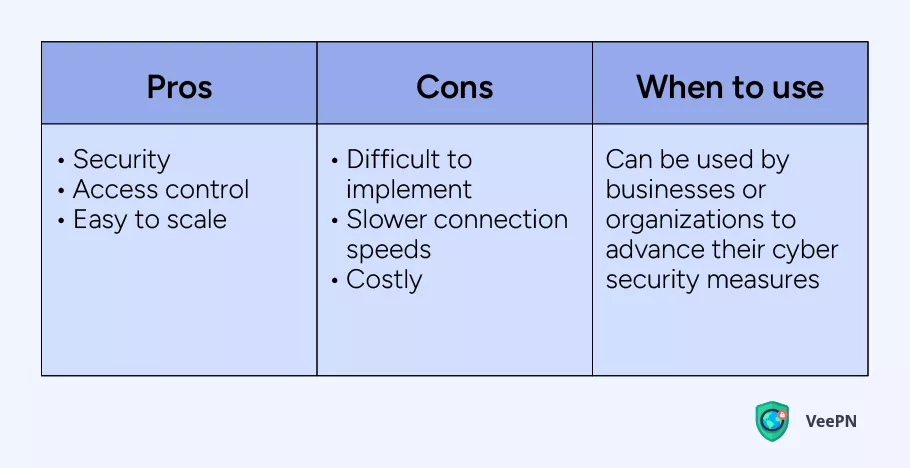
Zero Trust Network Access (ZTNA)
Trust nobody is the motto of this technology. ZTNA always assumes that users, sites, and devices are untrustworthy under any circumstances. This means every single user or device should pass the process of authentication and authorization before accessing any online resource. Granular access control, multifactor authentication, and real-time monitoring are the main security features used by ZTNA to create a solid defense around your network and devices.
Compared to VPN, this solution won’t connect you to a remote server, so you cannot use ZTNA to access geo-restricted content. ZTNA is one of the best VPN alternatives for businesses and organizations that need to take a special care of their digital security and protection against cyber threats. ZTNA can hardly be a fit for individual use.
Tor browser
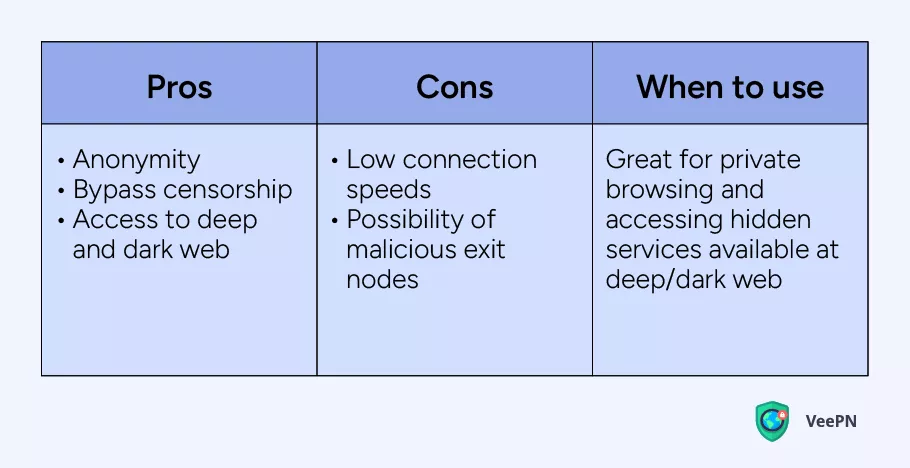
Tor is an open-source browser for anonymous web surfing. The browser uses a private network of servers created by volunteers called nodes or relays. When you use Tor, your traffic goes through thousands of such nodes, so that it’s impossible to track it. This browser lets you access any website, even within a deep and dark web.
Tor browser works almost like VPN, but since it passes traffic through so many nodes, it significantly slows down the connection speeds. That is why we can recommend using Tor only when you need to cover your identity with hundreds of encrypted connections to stay anonymous online. However, since the network of nodes is supported by random people, you can’t be sure that none of them have intentions to steal your sensitive data when it passes through their exit node.
Secure Shell Host (SSH) tunnel
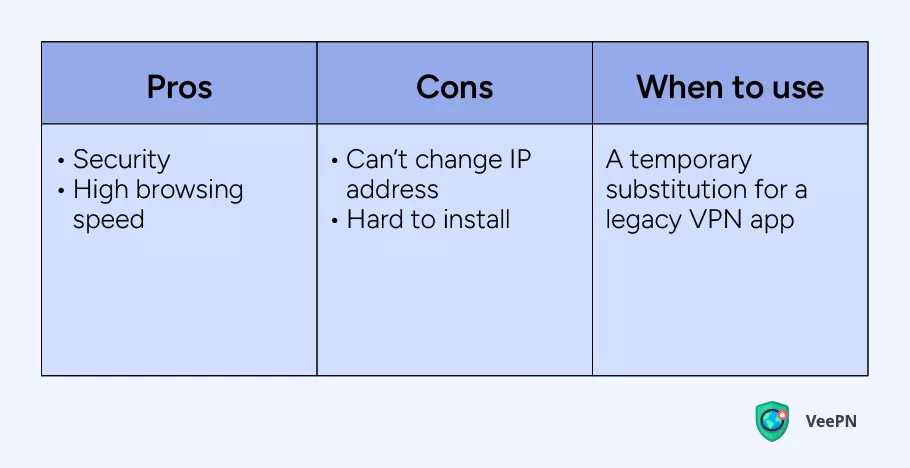
SSH tunnels work like a VPN but don’t change your IP address, so you can’t use it for accessing geo-blocked content. In fact, SSH is a protocol that secures your Internet traffic by passing it through an isolated tunnel, so that you can be sure nobody snoops on your data and you access any website without restrictions. This solution can be a good alternative when your VPN add doesn’t work for some reason.
Note: VeePN is not intended to be used as a means of copyright circumvention. For more details, read the VeePN Terms of Service and the Terms of Use of a relevant platform.
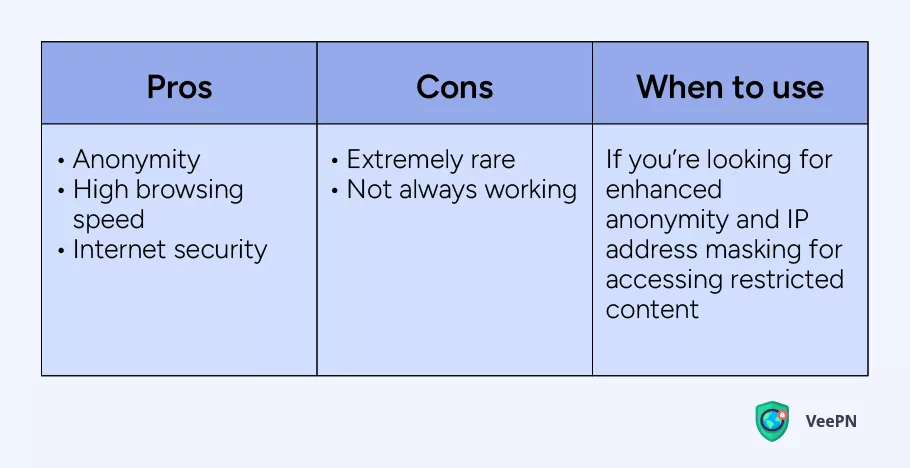
Decentralized VPN
Decentralized VPN is a combination of a conventional VPN with a technology used by Tor browser. This means you can change your IP address and stay maximally anonymous online. However, very few decentralized VPNs are working today, so their prime time is yet to come.
But if you want to be an early adopter and try this new word in the realm of cybersecurity, then why not?
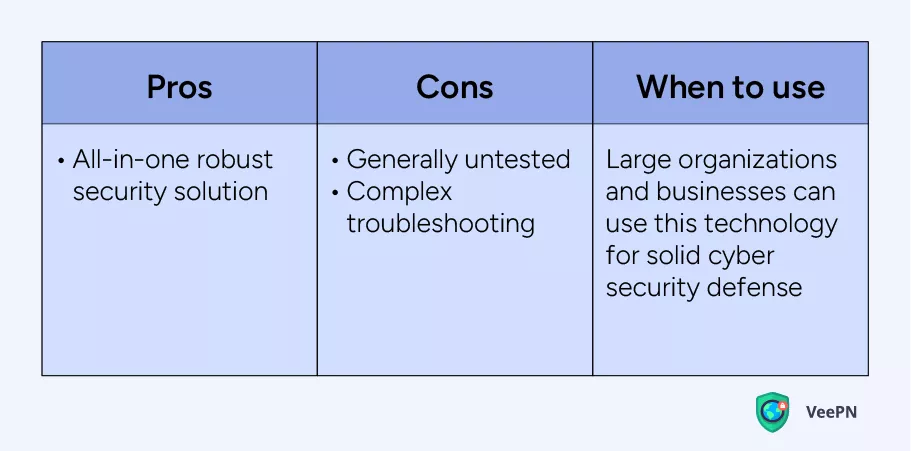
Secure Access Service Edge (SASE)
SASE is a combination of security solutions usually delivered as a cloud-based service. It includes the above-mentioned ZTNA and such components as:
- Software-Defined Networking (SDN). A network architecture managed and controlled via software, providing centralized control and dynamic adjustment of network configurations.
- Security Web Gateway (SWG). A security solution that blocks unsecured or potentially malicious data traffic from entering a network, ensuring safe Internet access.
- Cloud Access Security Brokers (CASBs). Security checkpoints between the service provider and user that enforce security policies when accessing cloud-based resources, ensuring data protection and compliance.
- Firewall as a Service (FWaaS). A cloud-based firewall solution that inspects and filters data traffic, similar to traditional firewalls on individual computers, but designed to enhance security in cloud computing environments.
Overall, SASE is a relatively new solution and it particularly fits large organizations where data security should be protected in as many ways as possible. For now, it’s difficult to imagine it makes sense to set up SASE for private use.
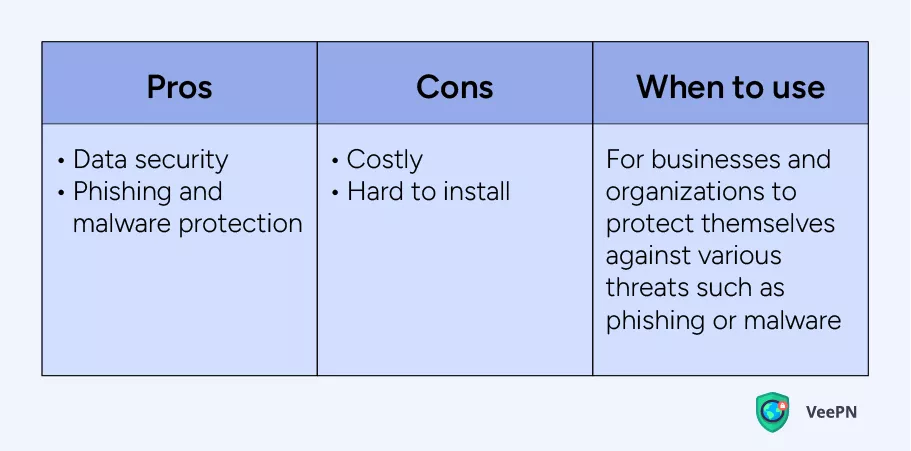
Secure Web Gateway (SWG)
SWG is an interface that separates your device from the “external” Internet. Using access control policies and blocking unauthorized access requests SWG works as a good anti-phishing and anti-malware protection.
It doesn’t mask your IP address like VPN but can protect your device from various threats that you may be even unaware of. So if you need to ensure you visit only secure sites and services, SWG can be your go-to. However, its price and complex installation imply that it’s a technology designed for business rather than individual use.
Choose your fighter to surf the web with comfort and security
Wrapping up, here’s a table to compare all alternatives to VPN software and pick the one that suits your needs best:
But there are many cases when you still need a VPN app. So when exactly? Let’s find out!
When should you stick to VPN?
It’s hard to argue that VPN is the best option when you need enhanced privacy and security without losing connection speeds and ability to access online content anywhere.
But free VPN apps don’t provide such advantages, which is why it’s better to use premium services like VeePN due to following benefits:
- Comprehensive security. VeePN keeps your online activity and data secure with a strong combination of features. This includes military-grade encryption, the latest VPN protocols, a built-in Kill Switch, and even Double VPN for an extra layer of protection.
- High connection speeds. VeePN offers WireGuard®, a cutting-edge VPN protocol known for its balance of simplicity and strong encryption.
- User-friendly interface. It’s extremely easy to navigate through any VeePN app, be it Chrome extension, PC version, Android app, or Smart TV application. Just pick a remote server and enable VPN connection in a couple of clicks without getting confused.
- No Logs policy. VeePN doesn’t collect your personal information for selling it to third parties, so you can use VeePN and be confident we won’t share your sensitive data with anyone.
- Access to streaming services. When you travel and can’t access your favorite streaming services, you can use special streaming-optimized servers by VeePN and watch your favorite movies or listen to music as if you are at home.
- Adblocking. In addition to security and streaming features, VeePN offers NetGuard, a strong adblocking feature that blocks any targeted ads in your browser and prevents third parties from tracking your online activity for comfortable and anonymous web surfing.
Try VeePN, a universal web browsing solution
If any of the suggested VPN alternatives don’t fully cover your needs, VeePN can be a good option. VeePN will provide you with impeccable security, access to the required content and high connection speeds to make your web browsing experience as comfortable as possible.
Download VeePN right now and have a 30-day money-back guarantee!
VPN alternatives
An alternative to VPNs is the use of proxy servers, which reroute Internet traffic through a different server to hide the user’s IP address and access geo-restricted content. Another option is the Tor network, encrypts your traffic through a series of volunteer-operated servers. Read this article to learn about other VPN alternatives.
The Tor network is often considered more secure than a VPN for maintaining anonymity and privacy. Additionally, a combination of VPN and Tor, known as decentralized VPN can further enhance security by adding layers of encryption and anonymization. Read this article to learn more.
Yes, VPN alternatives, such as SSH tunnels, proxies, and Tor, are generally legal. However, their legality can depend on the country and the specific use case. While using these tools for legitimate purposes, like securing personal data or accessing geographically restricted content, is usually legal, using them for illegal activities, such as bypassing government censorship in restricted countries or engaging in unlawful activities, can be illegal. Always check local laws and regulations to ensure compliance.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan







