SSH vs VPN: Which One “Tunnels” Network Traffic More Securely
Say, you’re a writer working on your next novel. You decided to work at a coffee shop on a public (read unsecure) Wi-Fi network. The chapter is finished, and you want to send it to your editor. But you don’t realize that your neighbor on that same Wi-Fi network can launch a man-in-the-middle attack and get their hands on your honest work. Now it’s their to steal and publish. Not cool.
So, can you do something to keep your data safe? Sure! No matter your field of work, every user should look into ways to shield their data on a public network. In this case, either a VPN or SSH can be a way to go. But which is more secure any why? Let’s find out.
What is SSH?
Let’s start with some basics. How does your computer send your data from one place to another? Thanks to a network protocol — a set of rules that tells your device how to transfer your data, say, from your computer to another server. If you send data over standard communication protocols, like File Transfer Protocol (FTP), it goes as plain text — unencrypted and vulnerable. Someone could take your data and abuse it (let’s not give any of those “neighbors” this chance). So, what can you do? One of the ways is to use SSH.
SSH (short for Secure Shell) is a network protocol for securing data that travels between a device and a server over a public network, like the Internet. It can transmit data, commands, and even files. Because it’s a cryptographic network protocol, it is secure. SSH uses cryptographic keys to authenticate a user. The most common use cases for SSH are:
- Secure data transfer
- Accessing remote devices and executing commands there
SSH tunnel explained
Simply put, an SSH tunnel is an encrypted tunnel an SSH protocol creates. After SSH authenticates a client, it sends unencrypted traffic to an SSH server over an encrypted SSH tunnel. That is to protect user data. The data arrives as it is, but its whole journey is encrypted.
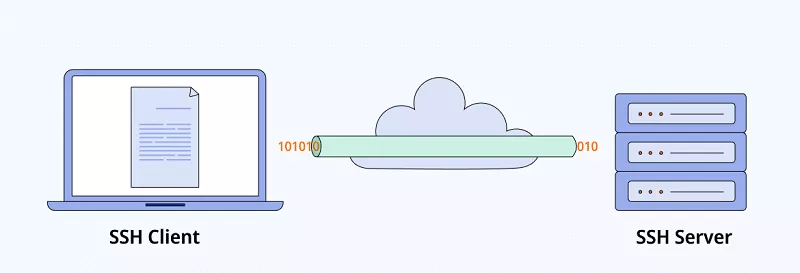
You can also create a SOCKS proxy with SSH to bypass content filters, in particular. With the SOCKS proxy running on your system, your traffic will enter the proxy and the SSH client will send it through the SSH tunnel. This is where SSH and VPN are similar — when you use either, your data seems to be coming from the SSH or VPN server from the web’s perspective. That data sent from your device to the server is encrypted. So, you can surf the web over the unprotected network without worrying about any dangers that can be looming online.
SSH: Pros and cons
Let’s go a bit further — SSH strong suits and weaknesses.
SSH advantages
- Can be used on different platforms, including major ones, like Windows, Mac, Linux
- Encrypts your data and can protect you from cybercrimes, like man-in-the-middle attacks
- Allows you to access remote devices
SSH drawbacks
- Works on an application level. You must configure each application to use the SSH tunnel
- Doesn’t encrypt all of your traffic, but only the apps you’ve configured
- Can be difficult to set up for inexperienced users
What is VPN?
And now on to our next solution.
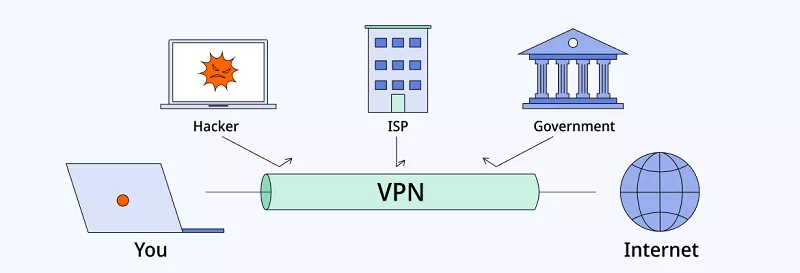
A VPN, or a virtual private network, ensures safe delivery of your data across public networks without any interception, eavesdropping, and censorship by third parties, like your internet service provider (ISP). It creates a private tunnel with an encrypted connection between several devices. A VPN reroutes your internet traffic through a remote server and hides your IP address. It provides one with a new online persona, hides their location and device type and makes the content of their data unreadable to third parties. There are VPN clients for both personal and business purposes, like protecting your online presence or securing and controlling access to company infrastructure.
VPN: Pros and cons
As with SSH, a VPN has benefits and drawbacks, too. Let’s take a look at them.
VPN advantages
- Encrypts all of your traffic
- Can encrypt traffic coming from the whole network, if you set up a VPN on your router
- User-friendly — easy installation and use with most VPN providers. You can change your IP address with a single click
- Premium VPNs let you choose any location you want. You also can connect multiple devices simultaneously with a single account
VPN drawbacks
- Free VPNs have a limited set of functions. Many of them are also unreliable
- Setting up a VPN on a server level is more complex
Difference between SSH and VPN
We can see that SSH and VPN are actually similar – both “tunnel” the traffic and encrypt your data. Ultimately, no unauthorized parties can access the information traveling through the tunnels. But let’s sum up a bit and compare the two solutions head-to-head. After all, they are two distinct security options.
| VPN | SSH | |
|---|---|---|
| User-friendly | Yes | No |
| Encrypts all of your traffic | Yes | No |
| Allows you to access remote devices | Yes | Yes |
| Easier to set up on a server level | No | Yes |
Bottom line
The similarity has definitely faded. Although both a VPN and SSH encrypt your data, its amount differs — a VPN protects all of your traffic, while you have to configure each application to use the SSH tunnel. Also, SSH is more difficult to set up and requires some level of expertise. So, protecting your data is much easier with a VPN. It also sounds like a better option for an individual user due to the user-friendly interface of most VPNs and enhanced protection.
Subscribing to a premium VPN, like VeePN, opens up a field of possibilities. You can protect your traffic with unbreakable AES-256 encryption on a public Wi-Fi and safely transfer your data without looking over your shoulder. Or access restricted content by connecting to one of the 2,500 servers in a country where that content is available — switch servers anytime you’d like. Or secure your whole home network by setting up VeePN on your router. One VeePN account — many benefits!
FAQ
Is SSH better than VPN?
Not really. Both encrypt your data and let you access filtered content. But you have to configure each application to use an SSH tunnel, while a VPN encrypts all of your traffic. Besides, an SSH can be difficult to set up for inexperienced users
Does SSH need VPN?
You don’t need to use both options at the same time since it’ll likely slow down your internet speed significantly. Also, due to the similarity of SSH and VPN functionality, either one will suffice in encrypting your data. It all depends on what your goal is. For example, if you want to encrypt all of your data while on a public network, a VPN is a way to go.
Is SSH really secure?
It’s a good security option since SSH is a cryptographic network protocol. SSH uses cryptographic keys to authenticate a user.
VeePN is freedom



