SSH vs VPN: Which One “Tunnels” Network Traffic More Securely
Hey, you’re a writer working on your next novel. You decided to work at a coffee shop on a public (read unsecure) Wi-Fi network. The chapter is finished and you want to send it to your editor. But you don’t realize your neighbor on that same Wi-Fi network can launch a man-in-the-middle attack and get their hands on your work. Now it’s their to steal and publish. Not cool.
So can you do something to keep your data safe? Sure! No matter your field of work, every user should look into ways to protect their data on a public network. In this case, either a VPN or SSH can be the way to go. But which is more secure and why? Let’s find out.
Remote Access
Remote access is more significant in the world of today, where we are all connected. It is important to be able to access networks and other devices at any time and place, not just when working at home, or remote servers, but also when you just need to access files on another device at any point. Remote access has become a reality with the help of technologies such as virtual private networks (VPNs) and Secure Shell (SSH), and nowadays it is possible to work efficiently and safely at any point.
Remote access enables you to access remote servers, devices and networks across the internet, be it to help trouble shoot a server across a border or cooperate with your co-workers on a joint project. The security measures of these connections such as VPNs and SSH prevent any unauthorized accessibility and cyber threats. Although both technologies can be used to offer secure connections, they do so differently and can be applied to various situations. Learning the distinction between VPNs and SSH can assist you in selecting the appropriate solution to your requirements, either to be able to reach the whole network or only a selected server or application.
With such technologies you can access with ease and security what you need through out wherever you go. With the increased adoption of remote working and cooperation across the globe, understanding the use of remote access protocols is becoming a necessity to every individual that cares about security, as well as flexibility.
What is SSH?
Let’s start with the basics. How does your computer send your data from one place to another? Thanks to a network protocol — a set of rules that tells your device how to transfer your data, say, from your computer to another server. If you send data over standard communication protocols, like File Transfer Protocol (FTP), it goes as plain text — unencrypted and vulnerable. Someone could take your data and abuse it (let’s not give any of those “neighbors” this chance). So what can you do? One of the ways is to use SSH.
SSH (short for Secure Shell) is a network protocol for securing data that travels between a device and a server over a public network, like the Internet. An ssh connection is a secure, encrypted link between your device and a remote server. It can transmit data, commands and even files. SSH ensures all data packets are transmitted securely and in order, maintaining the integrity and confidentiality of your information. Because it’s a cryptographic network protocol, it is secure. SSH uses cryptographic keys to authenticate a user. The most common use cases for SSH are:
- Secure data transfer
- Accessing remote devices and executing commands there
SSH tunnel explained
In simple terms, an SSH tunnel is used to create encrypted tunnels that the SSH protocol establishes. After SSH authenticates a client, it sends unencrypted traffic to an SSH server over an encrypted SSH tunnel. That is to protect user data. The data arrives as is, but its whole journey is encrypted.
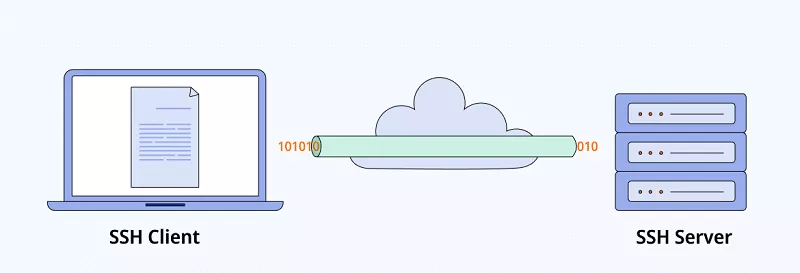
You can also create a SOCKS proxy with SSH to bypass content filters, in particular. With the SOCKS proxy running on your system, your traffic will enter the proxy and the SSH client will send it through the SSH tunnel. SSH tunnels are used for secure remote access and file transfers. This is where SSH and VPN are similar — when you use either, your data seems to be coming from the SSH or VPN server from the web’s perspective. That data sent from your device to the server is encrypted. So you can surf the web over the unprotected network without worrying about any dangers that can be lurking online.
Compared to VPNs, SSH tunnels give you more control over which applications or ports are secured, so you can customize your secure connections more.
Internet Secure Connections with SSH
SSH, or Secure Shell, is a powerful network protocol for secure communication between a user’s device and a remote server. By using strong encryption and authentication, SSH ensures any data sent over the internet remains private and protected from prying eyes. One of the key features of SSH is its ability to create an encrypted tunnel—commonly known as SSH tunneling or an SSH tunnel—which acts as a secure pathway for your data as it travels between your device and a remote server.
With SSH tunneling, users can access specific services or applications on remote devices even over untrusted networks. This makes SSH a great choice for system administrators, developers and anyone who needs to transfer files, run commands or manage remote servers securely. The encrypted tunnel created by SSH not only protects sensitive data but also allows users to bypass certain network restrictions making it a versatile tool for secure remote access.
Whether you’re connecting to a remote server to update software, transfer files or manage network services, SSH provides a robust layer of security. Its strong encryption and flexible configuration options make it a go-to protocol for anyone who needs secure, reliable access to remote devices and networks.
SSH: Pros and cons
Let’s go a bit further — SSH strong suits and weaknesses.
SSH advantages
- Can be used on different platforms, including major ones, like Windows, Mac, Linux
- Encrypts your data and can protect you from cybercrimes, like man-in-the-middle attacks
- Allows you to access remote devices
- SSH can be faster than VPNs in some cases due to its lighter encryption and lower resource usage
- SSH is considered safer for accessing remote servers, though it may not provide full protection for all internet traffic
SSH drawbacks
- Works on an application level. You must configure each application to use the SSH tunnel
- Doesn’t encrypt all of your traffic, but only the apps you’ve configured
- Can be difficult to set up for inexperienced users
What is VPN?
And now on to our next solution.A VPN, or virtual private network, ensures your data is delivered safely across public networks without interception, eavesdropping and censorship by third parties, like your internet service provider (ISP). It creates a private, secure tunnel with an encrypted connection between several devices, known as a VPN tunnel, which acts as a secure, encrypted pathway for all your internet traffic. A VPN works by routing your internet traffic through a remote server, hiding your IP address. This routing process conceals your activity, bypasses restrictions and enhances privacy. VPNs encrypt all traffic on the entire device, not just specific applications, providing full protection. It gives you a new online persona, hides your location and device type and makes the content of your data unreadable to third parties. There are VPN clients for personal and business use, and using a vpn app makes setup and connection easy and convenient for users of any skill level, whether you’re protecting your online presence or securing and controlling access to company infrastructure.
Data Encryption with VPNs
Hey, you’re a writer working on your next novel. You decided to work at a coffee shop on a public (read unsecure) Wi-Fi network. The chapter is finished and you want to send it to your editor. But you don’t realize your neighbor on that same Wi-Fi network can launch a man-in-the-middle attack and get their hands on your work. Now it’s their to steal and publish. Not cool.
So can you do something to keep your data safe? Sure! No matter your field of work, every user should look into ways to protect their data on a public network. In this case, either a VPN or SSH can be the way to go. But which is more secure and why? Let’s find out.
Remote Access
Remote access is more significant in the world of today, where we are all connected. It is important to be able to access networks and other devices at any time and place, not just when working at home, or remote servers, but also when you just need to access files on another device at any point. Remote access has become a reality with the help of technologies such as virtual private networks (VPNs) and Secure Shell (SSH), and nowadays it is possible to work efficiently and safely at any point.
Remote access enables you to access remote servers, devices and networks across the internet, be it to help trouble shoot a server across a border or cooperate with your co-workers on a joint project. The security measures of these connections such as VPNs and SSH prevent any unauthorized accessibility and cyber threats. Although both technologies can be used to offer secure connections, they do so differently and can be applied to various situations. Learning the distinction between VPNs and SSH can assist you in selecting the appropriate solution to your requirements, either to be able to reach the whole network or only a selected server or application.
With such technologies you can access with ease and security what you need through out wherever you go. With the increased adoption of remote working and cooperation across the globe, understanding the use of remote access protocols is becoming a necessity to every individual that cares about security, as well as flexibility.
What is SSH?
Let’s start with the basics. How does your computer send your data from one place to another? Thanks to a network protocol — a set of rules that tells your device how to transfer your data, say, from your computer to another server. If you send data over standard communication protocols, like File Transfer Protocol (FTP), it goes as plain text — unencrypted and vulnerable. Someone could take your data and abuse it (let’s not give any of those “neighbors” this chance). So what can you do? One of the ways is to use SSH.
SSH (short for Secure Shell) is a network protocol for securing data that travels between a device and a server over a public network, like the Internet. An ssh connection is a secure, encrypted link between your device and a remote server. It can transmit data, commands and even files. SSH ensures all data packets are transmitted securely and in order, maintaining the integrity and confidentiality of your information. Because it’s a cryptographic network protocol, it is secure. SSH uses cryptographic keys to authenticate a user. The most common use cases for SSH are:
- Secure data transfer
- Accessing a specific machine or server remotely and executing commands there
SSH tunnel explained
In simple terms, an SSH tunnel is used to create encrypted tunnels that the SSH protocol establishes. After SSH authenticates a client, it sends unencrypted traffic to an SSH server over an encrypted SSH tunnel. That is to protect user data. The data arrives as is, but its whole journey is encrypted.
You can also create a SOCKS proxy with SSH to bypass content filters, in particular. With the SOCKS proxy running on your system, your traffic will enter the proxy and the SSH client will send it through the SSH tunnel. SSH tunnels are used for secure remote access and file transfers. This is where SSH and VPN are similar — when you use either, your data seems to be coming from the SSH or VPN server from the web’s perspective. That data sent from your device to the server is encrypted. So you can surf the web over the unprotected network without worrying about any dangers that can be lurking online.
Compared to VPNs, SSH tunnels give you more control over which applications or ports are secured, so you can customize your secure connections more.
Internet Secure Connections with SSH
SSH or Secure Shell is a potent network protocol of secure communication involving the device of a user and a remote server. SSH can keep any data transmitted throughout the internet confidential and inaccessible to the prying eyes by employing a strong encryption and authentication. The most notable aspect of SSH is the fact that it can create an encrypted tunnel which is often referred to as the SSH tunneling or an SSH tunnel that is a secure communication channel through which your data is encased as it flows between your device and a remote server.
Using the SSH tunneling, users are at a position to use access particular services or applications in remote devices despite the unreliability of the network. This is why SSH is a great option to the system administrators, developers and all those who are required to transfer the files, execute commands or operate the faraway servers in a safe manner. The secured tunnel developed by SSH does not only have a defence of sensitive data but also enables users to overcome some restrictions within the network thus a resourceful tool of safe remote access.
SSH is a strong security layer whether it is just to update software on a remote server or to transfer files or control network services. Its great encryption and customizable features turn it into a protocol of choice of every single person who must have a safe and reliable access to remote devices and networks.
SSH: Pros and cons
Let’s dig deeper — SSH strong suits and weaknesses.
SSH advantages
- Can be used on different platforms, including major ones, like Windows, Mac, Linux
- Encrypts your data and can protect you from cybercrimes, like man-in-the-middle attacks
- Allows you to access remote devices
- SSH can be faster than VPNs in some cases due to its lighter encryption and lower resource usage
- SSH is considered safer for accessing remote servers, though it may not provide full protection for all internet traffic
SSH drawbacks
- Works on an application level. You must configure each application to use the SSH tunnel
- Doesn’t encrypt all of your traffic, but only the apps you’ve configured
- Can be difficult to set up for inexperienced users
What is VPN?
And now on to our next solution.A VPN, or virtual private network, ensures your data is delivered safely across public networks without interception, eavesdropping and censorship by third parties, like your internet service provider (ISP). It creates a private, secure tunnel with an encrypted connection between several devices, known as a VPN tunnel, which acts as a secure, encrypted pathway for all your internet traffic. A VPN works by routing your internet traffic through a remote server, hiding your IP address. This routing process conceals your activity, bypasses restrictions and enhances privacy. VPNs encrypt all traffic on the entire device, not just specific applications, providing full protection. It gives you a new online persona, hides your location and device type and makes the content of your data unreadable to third parties. There are VPN clients for personal and business use, and using a vpn app makes setup and connection easy and convenient for users of any skill level, whether you’re protecting your online presence or securing and controlling access to company infrastructure.
Data Encryption with VPNs
Online privacy and security is based on the use of VPNs, or virtual private networks. When you get connected to a VPN server, your traffic is diverted and a tunnel is created encrypted which blocks off the data to the hackers, ISPs and other third parties. It is a process which involves using sophisticated data encryption protocols in order to assure confidentiality and tamper-resistance to all the data packets transmitted or received.
VPNs will provide you with an opportunity to navigate the web, and you can even use the public Wi-Fi without any concerns about the risk of breaking in. A VPN does not only hide your actual IP address, but also allows you to bypass geo-blocking and access material which could otherwise be blocked in your location. That is why VPNs can be adopted by individuals who want to be privy as well as organizations that want to safeguard sensitive data about their business.
Having a VPN means that you will have secure and encrypted internet connections between all your devices thus your internet traffic is safe at all times. Whether you are working from home, watching movies or just browsing the internet, using VPN will provide you with the assurance that your information will not be stolen.
VPN: Pros and cons
As with SSH, a VPN has its advantages and disadvantages too. When using a VPN, you should choose a trustworthy vpn provider to ensure your privacy and security are protected. Advanced users may also set up their own vpn server for more control over their VPN connection. Let’s see them.
VPN advantages
- Encrypts all of your traffic Can encrypt traffic from the whole network, if you set up a VPN on your router
- User-friendly — easy installation and use with most VPN providers. You can change your IP address with a single click
- Premium VPNs let you choose any location you want. You also can connect multiple devices simultaneously with a single account
VPN drawbacks
- Free VPNs have limited functions. Many of them are also unreliable
- Setting up a VPN on a server level is more complex
SSH vs VPN
We can see that SSH and VPN are similar – both “tunnel” the traffic and encrypt your data. Both SSH and VPN are designed to maintain data integrity by protecting sensitive information during transmission. Ultimately, no unauthorized parties can access the information traveling through the tunnels. But let’s summarize a bit and compare the two solutions head-to-head. After all, they are two different security options.
VPN
SSH
User-friendly
Yes
No
Encrypts all of your traffic
Yes
No
Allows you to access remote devices
Yes
Yes
Easier to set up on a server level
No
Yes
Best Practices for Remote Access
Securing remote access to servers, devices and networks requires more than just choosing the right technology—it’s about following best practices to minimize risks and maximize protection. Here are some essential tips for using VPNs and SSH protocols safely and effectively:
- Use strong, unique passwords for all remote access accounts and change them regularly.
- Enable two-factor authentication (2FA) wherever possible to add an extra layer of security.
- Keep your software up to date, including VPN apps, SSH clients and server software, to protect against known vulnerabilities.
- Understand the differences between VPNs and SSH and choose the one that fits your needs—VPNs for encrypting all network traffic, SSH for accessing specific servers or services.
- Configure port forwarding and proxy settings carefully to allow only authorized users to connect to your remote servers.
- Audit and monitor your connections regularly to detect any unusual activity or security breaches.
- Educate users about secure protocols and security guidelines when accessing remote networks and devices. By following these best practices, you’ll keep your remote access connections secure, reliable and resilient to cyber threats. Whether you manage a fleet of remote servers or just connect to your home network from afar, a proactive approach to security will keep your data and devices safe.
Conclusion
The similarity is gone. Although both a VPN and SSH encrypt your data, the amount differs — a VPN encrypts all of your traffic, while you have to configure each application to use the SSH tunnel. Also, SSH is more complex to set up and requires some level of expertise. So, protecting your data is much easier with a VPN. It also seems like a better option for an individual user due to the user-friendly interface of most VPNs and added protection.
Signing up for a premium VPN, like VeePN, opens up a world of possibilities. You can protect your traffic with unbreakable AES-256 encryption on a public Wi-Fi and transfer your data without looking over your shoulder. Or access restricted content by connecting to one of the 2,500 servers in a country where that content is available — switch servers anytime you’d like. Or secure your whole home network by setting up VeePN on your router. One VeePN account — many benefits!
FAQ
Is SSH better than VPN?
Not really. Both encrypt your data and let you access filtered content. But you have to configure each application to use an SSH tunnel, while a VPN encrypts all of your traffic. Besides, an SSH can be difficult to set up for inexperienced users
Does SSH need VPN?
You don’t need to use both at the same time since it’ll slow down your internet speed significantly. Also, since SSH and VPN have similar functionality, either one will suffice in encrypting your data. It all depends on what you want. For example, if you want to encrypt all of your data while on a public network, a VPN is the way to go.
Is SSH really secure?
It’s a good security option since SSH is a cryptographic network protocol. SSH uses cryptographic keys to authenticate a user.
VPN: Pros and cons
As with SSH, a VPN has its advantages and disadvantages too. When using a VPN, you should choose a trustworthy vpn provider to ensure your privacy and security are protected. Advanced users may also set up their own vpn server for more control over their VPN connection. Let’s see them.
VPN advantages
- Encrypts all of your traffic Can encrypt traffic from the whole network, if you set up a VPN on your router
- User-friendly — easy installation and use with most VPN providers. You can change your IP address with a single click
- Premium VPNs let you choose any location you want. You also can connect multiple devices simultaneously with a single account
VPN drawbacks
- Free VPNs have a limited set of functions. Many of them are also unreliable
- Setting up a VPN on a server level is more complex
Difference between SSH and VPN
We can see that SSH and VPN are actually similar – both “tunnel” the traffic and encrypt your data. Ultimately, no unauthorized parties can access the information traveling through the tunnels. But let’s sum up a bit and compare the two solutions head-to-head. After all, they are two distinct security options.
| VPN | SSH | |
|---|---|---|
| User-friendly | Yes | No |
| Encrypts all of your traffic | Yes | No |
| Allows you to access remote devices | Yes | Yes |
| Easier to set up on a server level | No | Yes |
Best Practices for Remote Access
Securing remote access to servers, devices and networks requires more than just choosing the right technology—it’s about following best practices to minimize risks and maximize protection. Here are some essential tips for using VPNs and SSH protocols safely and effectively:
- Use strong, unique passwords for all remote access accounts and change them regularly.
- Enable two-factor authentication (2FA) wherever possible to add an extra layer of security.
- Keep your software up to date, including VPN apps, SSH clients and server software, to protect against known vulnerabilities.
- Understand the differences between VPNs and SSH and choose the one that fits your needs—VPNs for encrypting all network traffic, SSH for accessing specific servers or services.
- Configure port forwarding and proxy settings carefully to allow only authorized users to connect to your remote servers.
- Audit and monitor your connections regularly to detect any unusual activity or security breaches.
- Educate users about secure protocols and security guidelines when accessing remote networks and devices. By following these best practices, you’ll keep your remote access connections secure, reliable and resilient to cyber threats. Whether you manage a fleet of remote servers or just connect to your home network from afar, a proactive approach to security will keep your data and devices safe.
Conclusion
The similarity is gone. Although both a VPN and SSH encrypt your data, the amount differs — a VPN encrypts all of your traffic, while you have to configure each application to use the SSH tunnel. Also, SSH is more complex to set up and requires some level of expertise. So, protecting your data is much easier with a VPN. It also seems like a better option for an individual user due to the user-friendly interface of most VPNs and added protection.
Signing up for a premium VPN, like VeePN, opens up a world of possibilities. You can protect your traffic with unbreakable AES-256 encryption on a public Wi-Fi and transfer your data without looking over your shoulder. Or access restricted content by connecting to one of the 2,500 servers in a country where that content is available — switch servers anytime you’d like. Or secure your whole home network by setting up VeePN on your router. One VeePN account — many benefits!
FAQ
Not really. Both encrypt your data and let you access filtered content. But you have to configure each application to use an SSH tunnel, while a VPN encrypts all of your traffic. Besides, an SSH can be difficult to set up for inexperienced users.
You don’t need to use both options at the same time since it’ll likely slow down your internet speed significantly. Also, due to the similarity of SSH and VPN functionality, either one will suffice in encrypting your data. It all depends on what your goal is. For example, if you want to encrypt all of your data while on a public network, a VPN is a way to go.
It’s a good security option since SSH is a cryptographic network protocol. SSH uses cryptographic keys to authenticate a user.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








