SDP vs VPN: The Difference Defined

Many businesses migrated to the cloud recent years, a workforce became more flexible, elaborate networks appeared. But…cyberthreats evolved as well. That’s why network security is paramount today (not that it wasn’t earlier, but now it’s especially critical). And, luckily, there are various modern approaches, like a Virtual Private Network (VPN) and a Software-Defined Perimeter (SDP). Both solutions have been helping companies to accommodate their remote workforce by enabling remote access. Yet, due to a newer nature of SDP technology, some may know little or may not have heard of it at all. And this is where our article comes in handy. So buckle up — time to understand what all the fuss is about.
What is a Software-Defined Perimeter (SDP)?
To start with, an SDP is a cybersecurity approach, often referenced by the Cloud Security Alliance, aimed at concealing networks and their infrastructure (servers, routers, and other assets) from attackers or unauthorized users. An SDP acts like a cloak of invisibility (yes, like the one in Harry Potter but it’s all magic-free) to secure the system within the virtual perimeter. You can’t attack what you can’t see, right?
Among the major use cases for SDP are:
- Secure multi-cloud access. As SDP isn’t tied to any particular cloud or network, it can secure every connection, no matter where users connect.
- Reduced third-party risk. SDPs ensure that only authorized users get hold of the needed cloud resources. Besides, users won’t see applications they’re not allowed to access.
- Faster Mergers & Acquisitions integration. SDP makes the process of IT integration with its converging networks and overlapping IPs much simpler and easier.
How SDP works
As the name suggests, a software-defined perimeter, establishes a virtual perimeter via software, which conceals the company’s infrastructure from outsiders. An SDP controls network’s resources based on identity authentication – it authorizes users with a multifactor software token (involving the device’s personal identification number, serial number, and other unique identifiers) before connecting them. The authentication process is more thorough (since a simple password is likely to be vulnerable to phishing attacks) — it requires not only one’s login and password but also geolocation, biometrics, and other data.
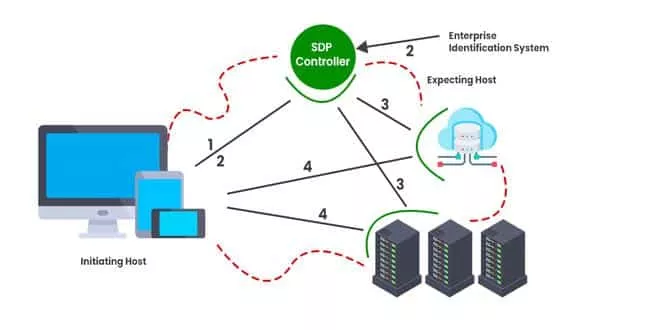
What an SPD workflow looks like
SDPs uses a zero trust network access approach (never trust, always verify) — it withholds access unless a user authenticates their identity. There are different types of SDP solutions, but a usual SDP architecture includes two main elements— an SDP Host and SDP controller. An SDP Host manages connections between user devices and applications. It’s of two types:
- An Initiating Host connects devices to an SDP controller. It gives information on who’s trying to connect to the network, requests a list of Accepting Hosts, and creates a mutual Transport Layer Security (TLS) connection with them.
- An Accepting Host connects authenticated devices to requested applications through an SDP controller.
An SDP controller identifies devices through an identification system (like geolocation, OpenID, Kerberos, and so on). It also gives access to Accepting Hosts.
So, a typical SDP workflow looks as follows:
- An Initiating Host gets a multifactor token and sends it and the user credentials to an SDP controller.
- The SDP controller passes the token and credentials to the identification system. Once identification goes through, the provider returns access rights to the SDP controller.
- The SDP controller finds an Accepting Host that will connect a device to a requested resource. Then the Initiating Host gets the IP of that host.
- The Initiating Host connects to the Accepting Host over a secure network connection. This way, the SDP enables user access.
What is a Virtual Private Network (VPN)?
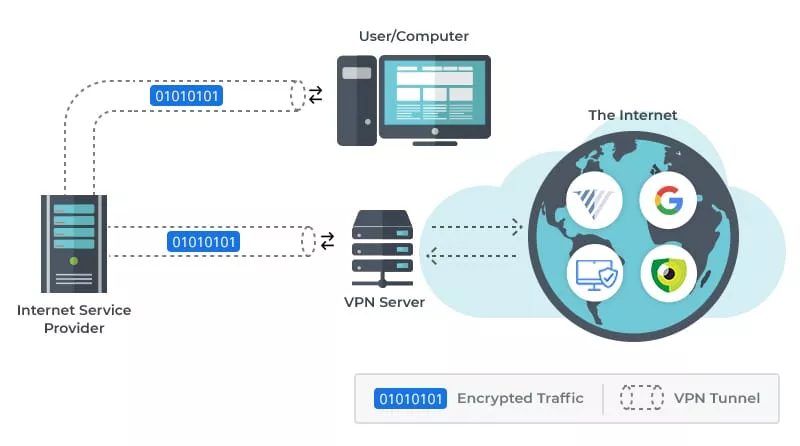
On to the next one. A VPN provides you with a private internet tunnel that creates a powerfully encrypted connection between several devices, improving remote user security. It makes sure your data travels safely without any interception, eavesdropping, and censorship. There are VPN clients for both personal and business purposes, like protecting your online presence or securing and controlling access to company infrastructure.
How VPN works
A VPN operates as an encrypted network that runs over an unencrypted one, such as the internet. It acts as an intermediary when you go online. First, a VPN obscures the user identity, providing an anonymized IP address — a new online persona. It hides their location and device type and makes the content of their data unreadable to third parties.
As in the case of SDP, one can use VPN to secure secure company resources within a company’s infrastructure. It encrypts tunnels between corporate networks and authorized end users. The tunnel secures all traffic via encryption using protocols like OpenVPN, IKEv2, and WireGuard. It lets remote users get into the internal network from anywhere they’re connected to the internet, without exposing their identity to outsiders. Once authenticated, you can get hold of resources in a trusted network. That way, only those connected to the VPN can access specific assets and get a view of network activity, which decreases the possibility of cyberattacks.
SDP vs VPN: Pros and cons list
SDP and VPN are both great options for establishing encrypted communication, but each one comes with its own pros and cons. Let’s find out what those are.
SDP Benefits
In addition to a high level of network security, SDP comes with the following security benefits:
- Support for a range of devices (including the Internet of Things (IoT)). SDP secures connections for any device demanding a set of data (not only a password and login) as credentials.
- Reduced network attack surface. An SDP decreases the possibility of a network attack since it limits broad access and hides enterprise resources from hackers. In this case, an SDP provides granular access to all assets, which creates perimeters around each resource. It means SDP grants access only when it’s necessary to carry out a task at hand through strict access control, decreasing the possibility of network threats.
- Zero trust policy enforcement. At the heart of SDP lies the “never trust, always verify” policy, meaning that a device or user will be trusted only when an SDP controller identifies it.
- Scalability and flexibility. Within an SDP, it’s easier to add a new resource (application, server, or database) because you can just add it to an existing Accepting Host (contrary to the traditional models when you need to add the resource to all cybersecurity solutions used).
- Encrypted data transfers. An SDP encrypts all connections between hosts and controllers (for example, through a mutual TLS connection).
SDP drawbacks
Of course, the SDP solution isn’t without its downsides:
- Controller vulnerability. Controllers are vital in the SDP architecture because they connect devices to protected resources. So if they’re offline, connecting one to the network will be a no-go.
- Network disruption during SDP integration. When chosen as a solution for a large company, accommodating SDP can disrupt network and infrastructure since all devices and applications will need reconfiguration.
- Configuration updates for applications. It’ll be time-consuming for system admins to update all apps and resources when integrating them with the SDP solution.
- Device limitations. Although SDP supports many modern devices, connecting old routers or vendor-specific devices to SDP software can be troublesome.
So as we can see, while an SDP significantly backs up network security, there might be some challenges during its realization.
VPN benefits
Now let’s see what VPN security has to offer:
- Secure connection. VPN provides high-quality security online through top-notch encryption algorithms. It encrypts all of your traffic and takes your data away from the prying eyes.
- Access at the network level. This point directly refers to a lack of granular security — once a user connects to the network via a VPN, they have unrestricted access due to missing granular access control policies. It may mean that some non-admin users can get hold of critical infrastructure (when they shouldn’t).
- Geo-restrictions removal. You can access geo-blocked content in your area or work from various locations around the world, not looking over your shoulder when connecting to public Wi-Fi.
- Low maintenance. A VPN remains a relatively cost-effective and easy-to-maintain option, especially if you’ve been using one for a long time. Using a top VPN client doesn’t mean you have to spend a fortune. Luckily, there are many affordable options at reasonable prices.
VPN drawbacks
At the same time, here’s where a VPN may fall behind:
- Slower connection speeds. Encryption and rerouting of your traffic takes time, and it can slow down your internet connection. However, using top VPN services with fast protocols and robust infrastructure will make speed drops virtually invisible.
- Access at the network level. This point directly refers to a lack of granular security — once a user connects to the network via a VPN, they have unrestricted access to all the resources. It may mean that some non-admin users can get hold of critical infrastructure (when they shouldn’t).
- Unstable connections. Unfortunately, connection drops may not be out of the ordinary when using a VPN. And when your encryption connection fails, so do your online defenses. So, it’s critical to use a VPN with a kill switch feature.
- Complex configuration. It’s essential to correctly configure a VPN to prevent any leaks and deny cybercriminals a chance to find some loopholes. Besides, VPN should be thoroughly monitored so it wouldn’t drop, leaving the entire network vulnerable to outside threats.
That said, when choosing a VPN client, you should make sure it has robust infrastructure as well as critical features like a kill switch.
How to improve your security
Last but not least…you probably already know it by this point, but we can’t stress enough how dangerous the internet realm can be. So you should do all it takes to battle the beast (read intrusive third parties that should mind their own business). Here’s what you can do:
- Update software. To prevent hackers from exploiting software vulnerabilities, keep your eye on every update that comes for the software you use.
- Keep your passwords strong. Change your passwords from time to time to keep your data safe. Keep in mind that a strong password is a long streak of symbols that don’t convey any sensible information. Besides, you should rely on a two-factor authentication service whenever possible. For example, it’d require to type a code received via a phone in addition to a password.
- Get educated. Imagine that the online environment is a dark alley where you may come across many risks. And to deal with those risks, you have to learn how to defend yourself. That’s why you should learn more about cybersecurity risks you may face. Besides, every company should train their employees on security and ensure that they know how to protect themselves online.
- Use a VPN (especially on a public network). A VPN boosts user security and privacy, encrypting their traffic and masking their IP address. If you’re looking for a trustworthy option, check out VeePN, which can run on up to 10 devices, including routers. VeePN provides top-notch encryption in the form of double VPN and a range of vital features that will build up your security online (kill switch is one of them!).
SDP vs VPN: A wrap-up
SDP and VPN are distinct solutions for maintaining online security. Although each has its downsides, the benefits of both do outnumber their drawbacks. SDPs have less proven enterprise success as they’re newer than VPNs. Despite this, they’re actively gaining traction in the field. If you wish to boost corporate security, you should weigh the pros and cons of both solutions before choosing one. And if you seek to strengthen your personal security and safety online, a VPN client is a sure-fire way to do so.
FAQ
Is SDP a VPN?
No. A Software-Defined Parameter (SDP) and a Virtual Private Network (VPN) are different cybersecurity solutions. While SDP relies on segmentation and user authentication to develop a protective perimeter, VPN creates a tunnel providing a secure encrypted connection between devices and the internet.
What is SDP in networking?
An SDP is an effective solution to network security. It aims to conceal networks and their infrastructure from attackers or unauthorized users.
What is SDP security?
An SDP uses a zero-trust approach: it restricts access into the network unless a user verifies their identity. Besides, SDP provides granular access, meaning that the user doesn’t get hold of all the resources but a specific one which they’re allowed to access.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






