Remote Wiping: How to Remotely Erase Data from Any Device
In an era where personal and business devices hold critical information, remote wiping is essential for safeguarding data in case of loss or theft. To ensure you won’t suffer any reputational damage from such occurrences, keep reading to learn about the importance of remote wiping, how it works, and the leading tools to keep your information secure, on the off chance that your gadget falls into the hands of malicious actors.

What is remote wiping and why it matters?
Let’s kick things off with a brief remote wipe definition. Remote wiping is a useful practice that lets you eradicate information on a lost or stolen gadget from a separate one.
Ordinarily, it is imperative to guarantee that sensitive information won’t get into the wrong hands in today’s computerized world. When your laptop or phone gets lost or stolen, remote wiping permits you to quickly and securely eradicate all the data on the device, preserving your safety from unauthorized info hijacking and potential data breaches.
Scenarios when remote wiping becomes essential
Now, let’s discover a few scenarios, where remote wiping can spare you from spilling your individual data into thieves’ hands:
🆘Lost or stolen phones: In case your smartphone is lost or stolen, remote wiping can help you avoid giving away your individual data, contacts, photographs, and other delicate information to malicious actors.
🆘Compromised laptops or tablets: In case your tablet or laptop, be it personal or corporate, gets stolen, remote wiping can defend your work records, logins, and other confidential information.
🆘Corporate data breaches: For businesses, remote wiping is fundamental for minimizing the harm from the information breach. It allows IT groups to rapidly secure company gadgets and ensure no touchy data is revealed to hackers.
🆘Data privacy protection: Remote wiping may be a key solution for keeping up information security and compliance, particularly when unauthorized access to your gadgets is highly possible.
How remote wiping works
Remote wiping works by triggering a command from a remote location, be it your computer or another connected device, to erase all the data on a lost or stolen device. Remote wiping command is typically sent through a cloud-based service or security app that is linked to the device.
Once the remote wiping command is running, the device will delete all its stored data, including files, photos, contacts, and app information. As a result, even if the device falls into the wrong hands, remote wiping can be the way out.
Ways to set up remote wiping on different devices
Below you can find the instructions on how to wipe your device remotely:
iOS
To enable remote wiping on your iPhone or iPad do the following:
1. Open the iCloud website and sign in to your account.
2. Navigate to the Find My iPhone feature.
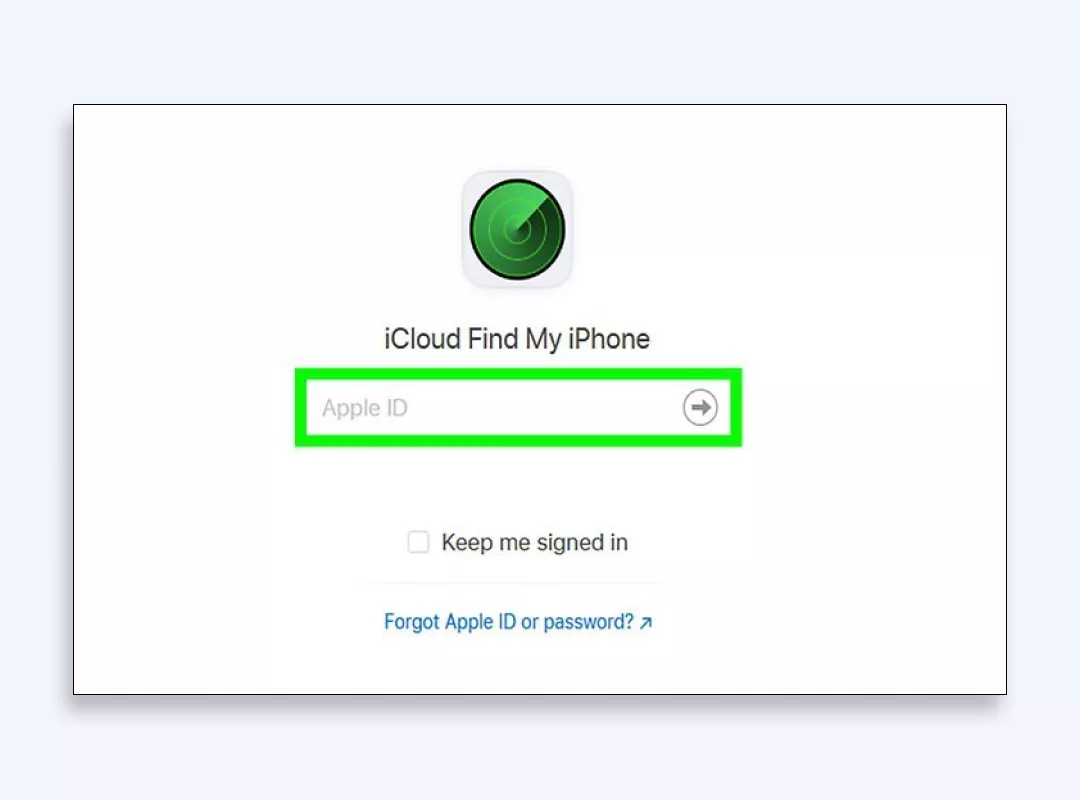
3. Locate your device on the map.
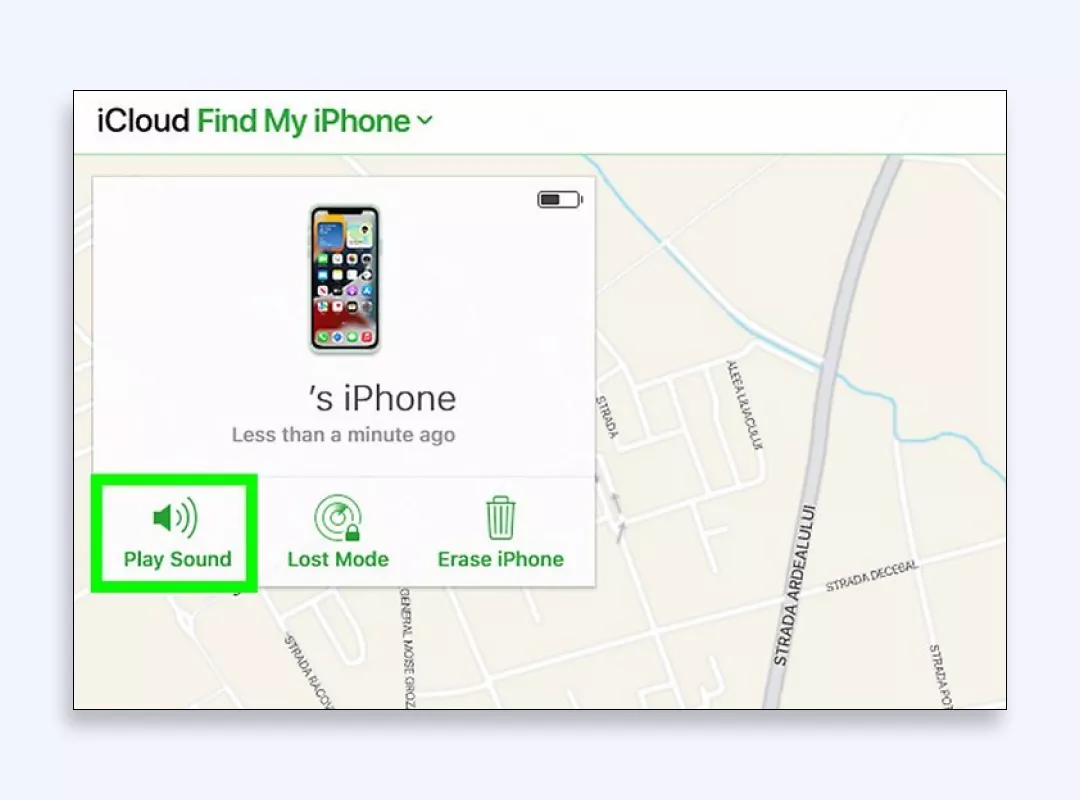
4. Select the Erase iPhone or Erase iPad option.
Android
As for remote wiping on Android devices follow these steps:
1. Download and set up the Find My Device app from the Google Play Store.

2. Ensure remote wiping is enabled on your Android device.
3. Log in to your Google account on another device or through the web.
4. Use the Find My Device tool to locate your Android device.
5. Select the option to enable remote wiping on your device.
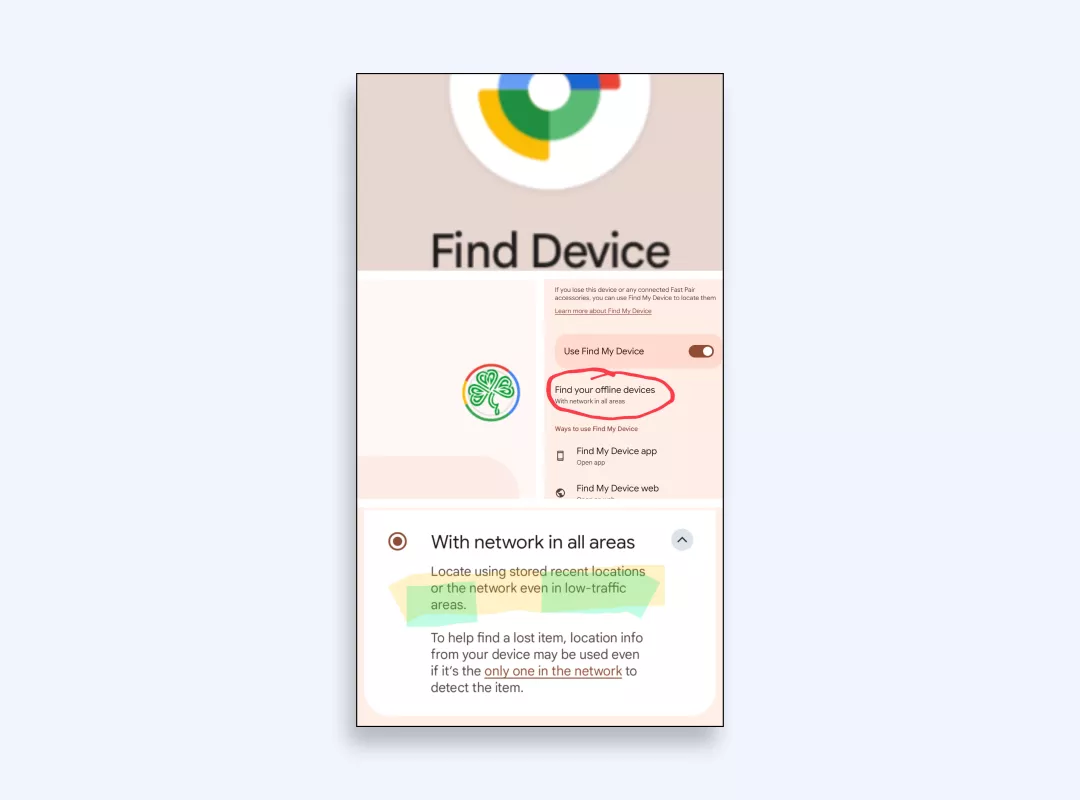
Windows
Now let’s move on to Windows remote wipe. For example, if you need a remote wipe on a laptop you’ve lost, do this:
1. Determine whether your device uses Windows Defender Security Center or Microsoft Intune for management.
2. If using Windows Defender Security Center: Access the security settings on your device and enable remote management features.
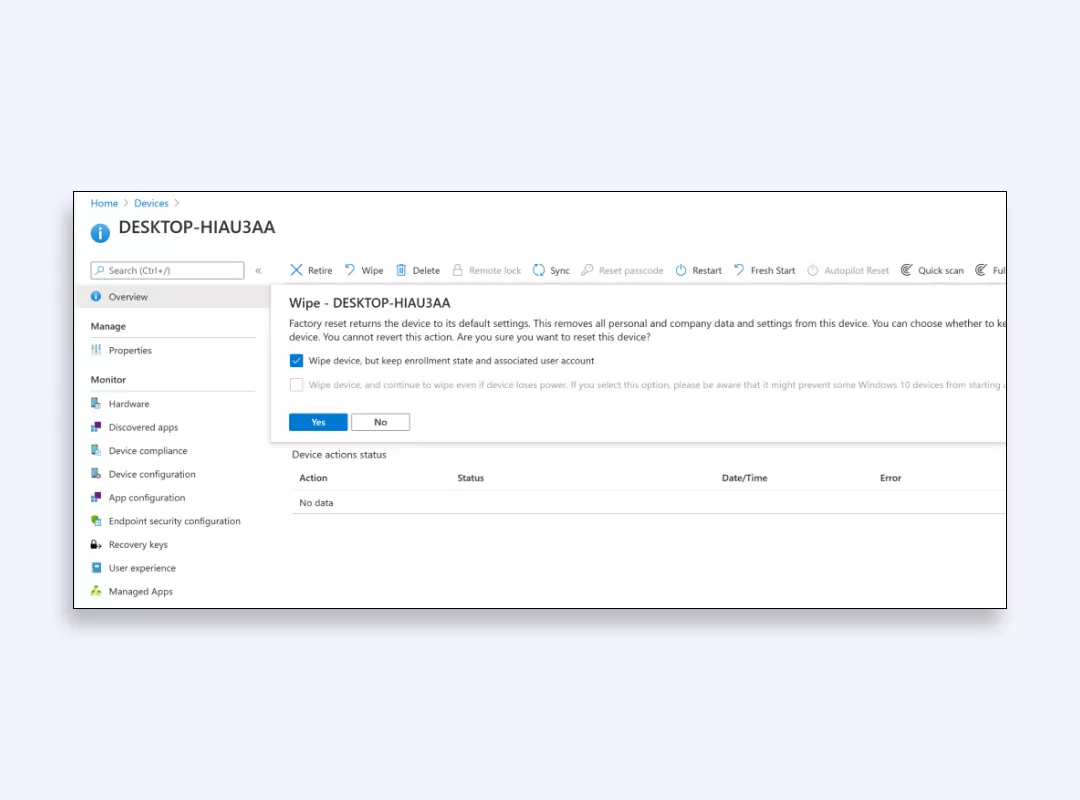
3. If using Microsoft Intune: Configure the device for Intune management and enable remote wipe options.
4. In the event of loss:
- Log in to the corresponding management portal (Windows Defender Security Center or Intune).
- Locate your device in the portal.
- Select the option to initiate a remote wipe.
MacOS
For Mac computers, you can enable remote wiping in the following way:
1. Enable the Find My Mac feature on your Mac through the iCloud settings.
2. Log in to your iCloud account on another device or through the web.
3. Navigate to the Find My Mac section.

4. Locate your Mac on the map.
5. Select the option to remotely erase your Mac.
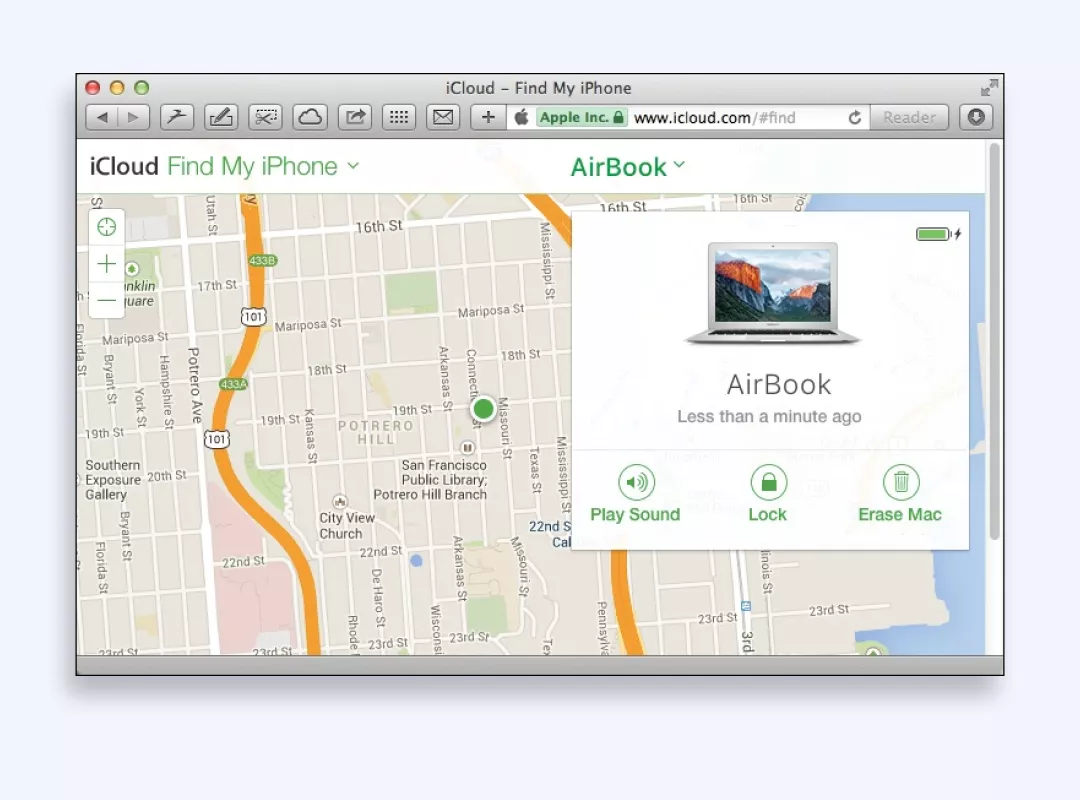
Limitations of remote wiping
Sure, remote wiping is a helpful solution for preventing data loss, but it’s vital to be mindful of its impediments:

⛔Possible interferences: The remote wipe command may be hindered if the gadget is turned off, has no web connection, or doesn’t have any power left.
⛔Data recovery dangers: In a few cases, the erased information may still be recovered by IT specialists, in spite of the fact that the chances are minimal.
⛔Protection scope: Remote wiping covers the information on the gadget itself, not any cloud-based or network-connected information that will have your private data stored.
⛔Other components: The adequacy of remote wiping can moreover be influenced by components such as gadget settings, network connection, and the speed of the remote wipe command execution.
Best practices for secure remote wiping
To guarantee the viability of remote wiping and keep up the security of your information, consider taking these best practices:
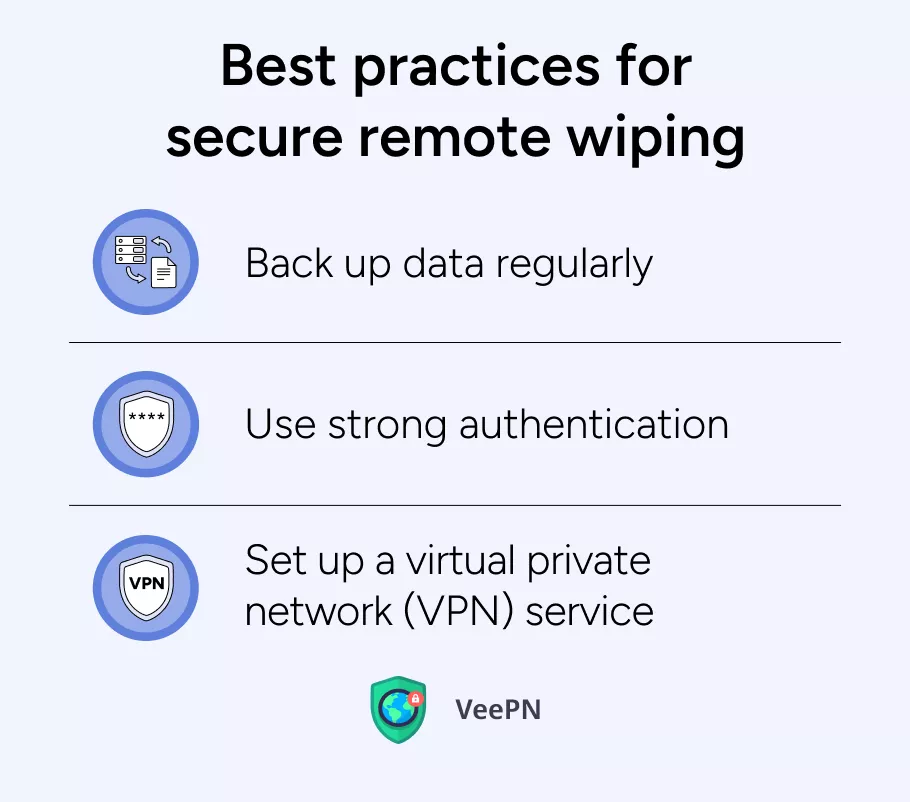
☝️Back up information frequently: Routinely back up your device’s information to keep a distance from cases of a remote wipe with full data loss.
☝️Use solid verification: Use strong passwords, fingerprint scans, or multi-factor authentication to keep unwanted folks outta your devices.
☝️Set up a virtual private network (VPN) service: Utilize a premium VPN, such as VeePN, to scramble your web activity and ensure your data is safe even if your device is lost or got snatched by someone.
Why are data encryption and VPNs crucial for data security?
Data encryption is essential for protecting sensitive information, as it scrambles the data so that it’s unreadable to anyone without the proper decryption key. So even if your device is lost or stolen, the data cannot be accessed by unauthorized parties.VPNs, such as VeePN, play a crucial role in data security by encrypting your Internet traffic and masking your IP address. This helps prevent eavesdropping and ensures that your online activities and data remain private, even on public Wi-Fi networks. But why should VeePN be your go-to choice? Let’s discuss this in detail!
VeePN – an ideal solution for securing your sensitive data
VeePN is a premium VPN service that offers advanced security features to protect your data:
🛡️AES 256-bit encryption: VeePN uses AES 256-bit encryption (real fancy stuff) to keep your Internet traffic locked up tight. No snoopers allowed!
🛡️IP address masking: VeePN hides your real IP address, so nobody can spy on what you’re doing or figure out where you are.
🛡️Advanced security features: Kill Switch, Breach Alert, and Alternative ID make sure your data stays safe, even if your connection drops.
🛡️No Logs policy: We don’t keep logs of what you do online. What happens on VeePN stays with you!Our solution works on all major devices, and one subscription covers up to 10 gadgets. Grab VeePN now and give it a shot—30-day money-back guarantee, no worries!
FAQ
Remote wiping’s pretty good for getting rid of data, especially if someone snatches your phone with critical data stored in it. You just hit a button, and bam — everything’s gone.
But here’s the thing — if the phone has no Internet, the wipe won’t work until it gets back online. And if some smart guy pulls out the SIM card or shuts off Wi-Fi, you’re outta luck. That’s why it’s good to have stuff locked up tight with passwords or encryption.
All in all, it’s a solid way to erase stuff, but don’t count on it like it’s magic.
A phone can be remotely wiped. Most phones got that feature built in even — Apple’s got “Find My iPhone,” and Android’s got “Find My Device.” You just log in from another gadget, hit the erase button, and everything’s gone.
But it’s not that perfect either. If the phone’s turned off or ain’t connected to the internet, the wipe won’t happen till it gets back online. And if someone’s real sneaky, they might block it by yanking out the SIM or turning off Wi-Fi.
So yeah, remote wiping works, but it ain’t instant unless the phone’s still connected.
You can remotely wipe a PC, but it depends on what kind of setup you got. If you’re using something like Microsoft’s Intune, Apple’s Find My Mac, or certain business security software, you can log in from another device and wipe it clean.
But just like with phones, the PC’s gotta be online for it to work. If it’s turned off or not connected, the wipe won’t happen until it gets back online. And if someone’s really smart, they might block it by yanking out the internet connection or messing with the settings.
So it’s possible, but it ain’t foolproof. Best to keep important stuff encrypted, just in case.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






