Phishing vs. Spear Phishing: Which is More Dangerous and How to Stay Safe
Imagine you’re sitting at your desk, sipping coffee. An email pops up and it’s from your bank—or so it claims. The subject line screams urgency: “Your account has been compromised! Act now!” You hesitate, your heart skips a beat, and you click the attached link without hesitation. Moments later, you realize something feels off, but it’s too late.
Now, what if that email wasn’t an obvious attempt to scam you, but instead a carefully crafted message sent by your boss with their signature attached? It asks you to quickly approve a wire transfer or share sensitive company data. It looks so convincing, you wouldn’t think twice.
These two scenarios illustrate the difference between two cybercriminal masterminds: Clumsy Pete aka phishing scam we are all aware of, and Sneaky Sam aka spear phishing, who pays attention to every detail. In this guide, we’ll describe the difference between phishing vs spear phishing, expose their tactics, show you how to spot the signs, and arm you with the tools to stay one step ahead.
What is phishing?
Phishing attacks use links to fake sites that look like legitimate ones to trick you into revealing sensitive data.
Here are some of the main characteristics of phishing attacks:
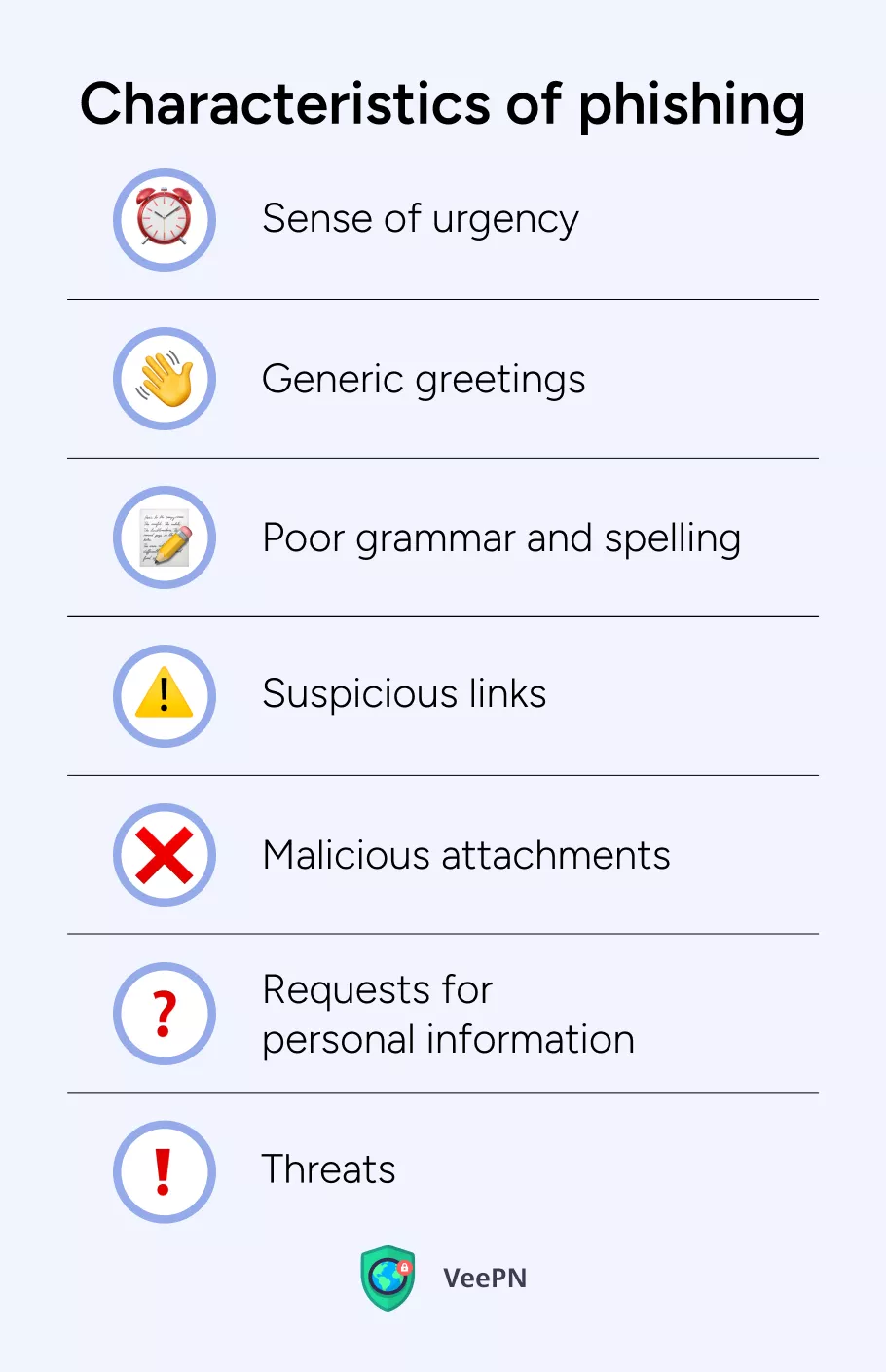
🚩Sense of urgency: Phishing emails use severe pressure to push you into acting immediately without thinking about the consequences.
🚩Generic greetings: Instead of using your name the phishing message starts with generic salutations such as Dear Customer or Dear Sir/Madam.
🚩Poor grammar and spelling: These fraudulent messages often show language mistakes.
🚩Suspicious links: Phishers design fake websites to steal your data by giving you spoofed links to follow.
🚩Malicious attachments: These emails have harmful attachments that could damage your computer with malware.
🚩Requests for personal information: A scammer needs your sensitive details to run their fraud.
🚩Hostile language: When you don’t want to follow a criminals’ requests, they may use threatening language to force you to share your personal information.
What is spear phishing?
Spear phishing uses precise methods to aim at individual targets or their workplace.
Spear phishing emails represents a refined and well-targeted for phishing attack. Here are some of its key characteristics:

🚩Personalization: Hackers create targeted phishing attacks that incorporate specific facts to make messages seem trustworthy. They use this knowledge to craft personalized messages targeting both the specific person or their workplace for business email compromise and whaling attacks.
🚩Social engineering: The hackers use social engineering methods to trick users into clicking on malicious links or opening malicious file. Scammer attempt to trigger strong emotions like anxiety or make you feel curious about the message and take an impulsive action and share their sensitive information.
🚩Impersonation: Most spear phishing attempts fake identity of someone the victim already trusts such as colleagues, direct supervisors, or their bank.
🚩Credible content: To make scams seem real the attackers may attach relatable media or other content in their messages.
These attacks succeed better than normal phishing because scammers customize them specifically for targeted victims. Still, we need to discuss clear differences between spear phishing vs phishing, so you can take a relatable action immediately.
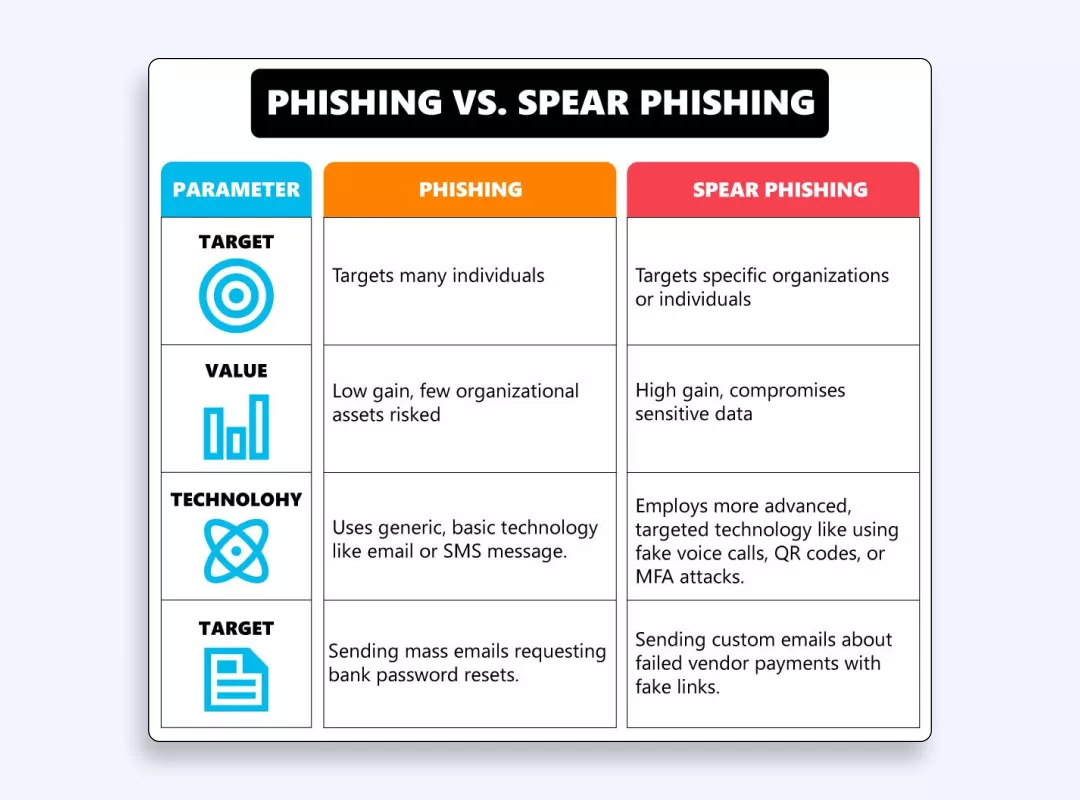
Key differences between phishing and spear phishing
Even though Clumsy Pete and Sneaky Sam are cybercriminals “working” in the same field, their methods do differ:

↔️Target audience: Phishing targets many, while spear phishing targets specific individuals.
↔️Personalization: Phishing lacks personalization, while spear phishing involves tailored messages.
↔️Channel of distribution: Phishing uses basic channels of communication such as emails and SMS, while spear phishing focuses on fake voice calls, quick response (QR) codes, or multi-factor fatigue attacks.
↔️Sophistication: Phishing is straightforward, while spear phishing uses sophisticated tactics.
↔️Potential impact: Phishing can lead to individual data loss, while spear phishing can cause significant harm to businesses.
To help you identify key clues, here’s an infographic comparing phishing and spear phishing messages.
But let’s test how well you know Clumsy Pete and Sneaky Sam!
Phishing vs. spear phishing: quick Test
Here are two scenarios. Decide which one is a classic phishing attack done by Clumsy Pete and which one is a spear phishing attack that Sneaky Sam definitely stands behind!
Scenario 1:
- You receive an email from “Amazon Support” with the subject line “Urgent: Account Security Breach.”
- The email body is poorly written with grammatical errors.
- It asks you to click a link to verify your account information.
Scenario 2:
- You receive an email from your “boss” asking you to urgently transfer a large sum of money to a specific account.
- The email is well-written and uses your company’s official logo.
- The request seems unusual but the email appears to be from a trusted source.
Answers and explanations:
- Scenario 1 is a classic phishing attack — a typical Clumsy Pete. It’s a generic message sent to a wide audience, using a common tactic of creating urgency and fear.
- Scenario 2 is a spear phishing attack. Sneaky Sam has targeted a specific individual (you) and used information about your workplace and relationships to make the email seem legitimate. This is a more sophisticated and personalized attack.
Do you understand the difference? But what are the risks both Clumsy Pete and Sneaky Sam can cause for your online security? Let’s find out!
Risks of phishing and spear phishing attacks
The common traps of getting caught in both phishing and spear phishing are:

⚠️Financial loss: Once they have your bank account details, Pete and Sam will quickly find every way possible to steal all your money.
⚠️Malware infection: Phishing emails contain virus-infected files or links that can put viruses or spyware on your device.
⚠️Reputational damage: Businesses hit by phishing attacks may lose customers’ trust and face possible legal penalties.
⚠️Insider threats: Spear phishing may focus on a particular company through its own workers who don’t realize they are giving crucial info to hackers.
Sneaky Sam proves himself a smarter con artist when compared to Pete. Specific people targeted by spear phishing attacks face greater danger because these criminals design better scams compared to a common phishing.
How to stay safe from phishing and spear phishing attacks
To prevent spear phishing attacks as well as common phishing and never meet Clumsy Pete and Sneaky Sam, follow these simple steps:

🛟Verify email senders: Always check the sender’s email address and avoid clicking on suspicious links.
🛟Use multi-factor authentication: This adds an extra layer of security to your accounts.
🛟Email filtering tools: Use such instruments like SpamTitan, Spambrella, or Mimecast to block suspicious messages before they reach your inbox.
🛟Password managers: Rely on password managers such as Keeper, 1Password, or LastPass to avoid login credentials reuse.
🛟Secure Internet access with a VPN app: use a virtual private network (VPN) to secure your connection. But remember that free VPNs aren’t safe as they can still leak your personal information to third parties. Consider using a premium service like VeePN instead.
Protect your data against phishing and spear phishing with VeePN
Using VeePN offers several advantages:

🛡️Encrypting connections: VeePN uses AES 256-bit encryption that is considered the most reliable standard so far. By using this standard, the app secures your Internet traffic, so hackers won’t be able to read a bit of your sensitive data.
🛡️Masking IP addresses: Since VeePN passes all traffic through a remote server, you can hide your IP address to conceal your identity and location from prying eyes.
🛡️Anonymous Email: This feature allows you to generate a fake email address that keeps your real one hidden. Attackers will believe they have your email, but your actual address stays private while still receiving forwarded messages from the fake one.
🛡️NetGuard: VeePN blocks any malware, so that even if you did click on a phishing link, this feature will protect your device from being infected.
You can use one VeePN subscription to secure up to 10 devices simultaneously. Download VeePN today and enjoy a 30-day money-back guarantee!
FAQ
Spear phishing uses personalized and very believable emails or messages to trick chosen individuals into letting out valuable details or downloading harmful computer programs. Spear phishing emails look more convincing because they tailor information for each user, including their name, job title, and workplace. The attackers try to carry out three things: steal data, pretend to have permission they don’t have, and attack the victim’s computer systems.
Hackers phish companies through fake communication from executive, employee, or supplier emails to steal cash or corporate intelligence. A BEC attack tricks someone into believing they’re talking to an executive through company emails. Bad guys make spear phishing emails look real to fool certain individuals into offering up secret details or opening risky URLs. Spear phishing works by focusing on picking out single people while BEC relies on stealing money from how businesses handle payments.
VPNs cannot block all kinds of phishing attacks. The VPN makes your Internet connection private by encrypting your traffic and taking your real IP address out of view. The encryption helps keep you safe, but it can’t tell you if incoming messages are fake or dangerous. Protect yourself by using a VPN along with email filters, antivirus protection, and user training that teaches how to avoid being phished.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






