How to Secure Your Crypto: 8 Essential Measures
Looking for ways to secure crypto? Good, because the need is dire — in 2023 alone, cybercriminals stole a whopping $10.2 billion in cryptocurrency from crypto exchanges and online wallets. Desperate times call for desperate measures (read feasible solutions to protect your crypto). And we’re here to help you with that. Read along to find out all about cryptocurrency security.
Crypto wallet security
Although many believe the crypto market to be secure, it has actually faced some significant threats. Even popular legitimate platforms often fall prey to scammers. For example, the Mixin platform was recently compromised due to one of the largest cyberattacks that resulted in a $200 million loss. The thing is that all transactions are stored on a distributed public ledger. You also leave an IP footprint at crypto exchanges and other platforms, which can lead to data breaches. Now, can you do anything to boost crypto wallet protection? Sure thing! So, let’s go through the following crypto security tips:

Use VPN to secure your Internet traffic
The first and foremost measure to secure your cryptocurrency is using a virtual private network (VPN) application. But in what way a VPN for crypto is good, exactly?
- VPN encrypts all the data you send and receive, making it almost impossible to intercept and read.
- VPN adds an extra security layer against malware, viruses, and phishing attacks.
- It hides your IP address and prevents tracking by third parties, like hackers or government officials. This way, you can anonymously buy and sell crypto.
- A good VPN app comes in handy, when you travel but still need to trade your assets at your favorite exchange platform that may be unavailable in your travel destination. A VPN app can connect you to a remote server, so you’ll be able to browse the web as if you are at home and access geo-restricted sites.
You may come across a free VPN, but it may not be the best choice. Free VPNs for crypto tend to profit from selling your private data and bombarding you with ads. If you are serious about your privacy and security, it’s better to get a premium VPN instead. Keep on reading to know how to pick a credible VPN for crypto.
How to choose a VPN for cryptocurrency
Now, what should you look for in a VPN for crypto, in particular? Let’s find out.
- A strict No Logs policy. For doing crypto transactions, go for a privacy-oriented VPN that doesn’t collect and store your personal information. This means your activity remains private.
- Kill Switch. This feature cuts your Internet connection when your VPN connection drops. All to prevent third parties from accessing your real IP address.
- Absence of mass surveillance programs. Top-rated VPN providers typically come from countries where there are no surveillance agencies. For example, VPN services based in the US, UK, Australia, New Zealand, and Canada may be forced by the state to hand over user data. These countries are also known as the ‘Five Eyes’ alliance. Whereas countries like the British Virgin Islands, Panama, and Switzerland don’t force VPNs to collect and store user data.
- Simultaneous protection for multiple devices. If you do crypto transactions on several devices, you should protect your crypto on each device. That’s why it’s crucial to choose a VPN you can run on multiple gadgets with one account only.
VeePN is a VPN service that fully meets all these criteria. Based in Panama outside the 5/9/14 Eyes jurisdiction, VeePN is the most advanced and trustworthy VPN for crypto enthusiasts. The service protects all your data with AES-256 encryption — the most robust to date. This means you can browse the web even on public networks and be sure your data is protected.
Besides, VeePN has a Double VPN feature that encrypts your traffic twice, so hackers will need thousands of years to decipher your personal information. If you use several devices and want to protect your crypto wallet transactions on all of them, it’s not a problem. You are guaranteed to have up to 10 simultaneous connections on various platforms with just one VeePN subscription!
Buy crypto from a reputable source
The world of Web 3.0 is filled to the brim with scams, frauds, and hacker attacks, so you should be cautious while buying cryptocurrency. Fake crypto exchange platforms that attempt to imitate being legitimate and offer super low exchange prices as well as various too-good-to-be-true benefits pose the most serious threat.
Imagine you have to walk to a specific destination and you have two ways: one is short and lying through a dark empty street, and one is long but leads through the city center with a lot of street lighting and police patrolling the area. Which way is less risky? The second one for sure. The same thing with crypto exchanges.
To keep your money safe, we’ve prepared the top 5 most reliable cryptocurrency exchanges we recommend for buying crypto from. Check the list below:
- Kraken
Why it’s secure: Kraken stores the majority of user deposits in secure offline storage. Their servers undergo constant surveillance by armed guards, and access to them by employees is tightly regulated. - Gemini
Why it’s secure: Gemini safeguards the majority of its cryptocurrency in cold wallets or hardware wallets, ensuring they remain offline and impervious to online threats such as hacking and breaches. Gemini’s offices do not house private keys; instead, these keys are dispersed geographically across secure data centers with restricted access. - Coinbase
Why it’s secure: The company confirms that 98 percent of deposits are securely stored in guarded facilities. All digital assets held on Coinbase benefit from insurance coverage against cybersecurity breaches and theft, although losses stemming from user error are not covered.Coinbase accounts are protected with multi-factor authentication, an additional security layer that enhances protection and guards against breaches and phishing attacks. - Crypto.com
Why it’s secure: Crypto.com ensures the complete offline storage of 100 percent of user cryptocurrencies, with additional security provided by a $750 million insurance coverage against theft and physical damage for its hardware storage.To safeguard user funds, Crypto.com has implemented multi-factor authentication, incorporating biometric and email verification. This layered authentication approach offers users multiple options to enhance the security of their accounts. Additionally, withdrawal protection measures are in place to further secure user funds.
- Binance
Why it’s secure: The platform monitors all withdrawal and password reset attempts, and any detected unusual activity triggers a suspension of withdrawals for a period of up to 48 hours. Sensitive user data is subjected to encryption protocols to ensure confidentiality. Stringent sign-in measures are implemented, including two-factor authentication, security notifications, and verification via SMS and email. These precautions collectively contribute to bolstering the security of user accounts.
But once again, we have to warn you against fake crypto exchanges that try to mimic reputable sources. Such sites will do anything to lure you into their phishing net (pun intended): create similar, yet slightly different domain names from the legitimate websites, provide “special offers”, or convince you to buy as much crypto as you can afford. For that reason, to make sure you’re on the right website, always double-check the URL spelling. Check certificates, the team (if such info is available), and anything that verifies the platform’s legitimacy.
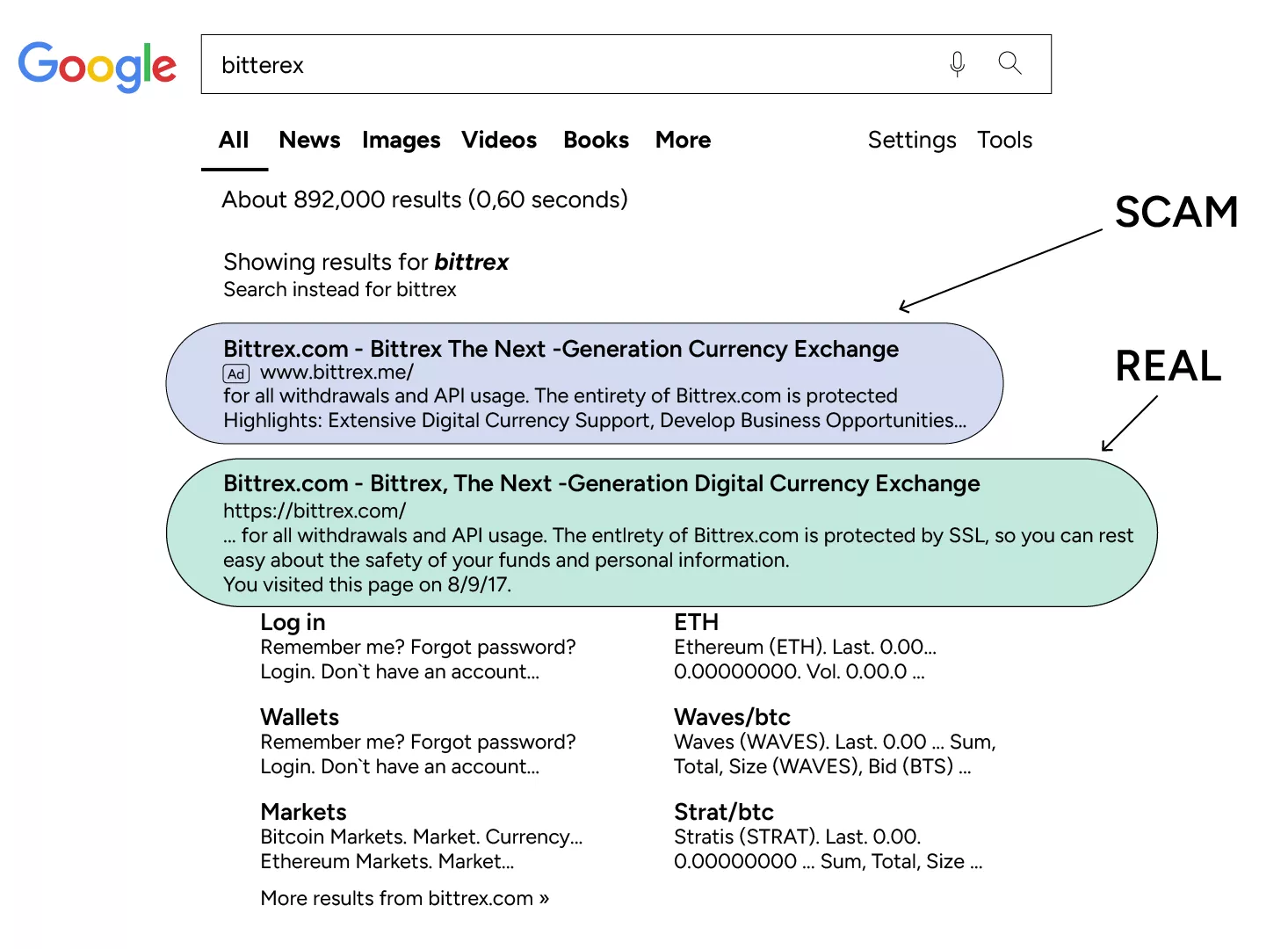
In addition to being vigilant with exchanges, you can protect your Internet privacy by browsing these platforms via Virtual Private Network (VPN). A credible VPN service will pass all your data through a separate “tunnel” where it gets encrypted and becomes unreadable by hackers, so that you’ll be able to protect your identity when you trade crypto.
Note: Be welcome to read our relatable article “How to Use VPN for Crypto Trading” to learn more.
Use a reliable wallet
Exchanges are surely useful because they let you buy and sell easily, without having to find a user for each crypto you want to deal with. Keeping cryptocurrency there can seem safe at first glance. But it’s actually not. Not from a cybersecurity perspective, at least. Exchanges can be the target of hacker attacks, phishing and smishing, as well as other dangers. Besides, some platforms can halt withdrawals, especially during downturns. The best option would be to store your crypto independent of exchanges, in multiple wallets, preferably cold (hardware) and non-custodial (you have the sole right to store your private keys) wallets — offline cryptocurrency storage. There are different types of crypto wallets, so ideally, you should store most of your crypto across several cold wallets, while keeping only a small portion of it in a software wallet. We recommend using such hardware wallets as Ledger, Trezor, and Safepal.
Create a strong password
American cybersecurity firm Digital Guardian did a poll where 61 percent of respondents said they use the same password across several websites, while 89 percent said they were sure about their password management practices. However, having the same password on various platforms is a no-go. If you want to improve your crypto assets protection, create complex and unique passwords. Changing them from time to time is also a good idea — go for at least a few times per year.
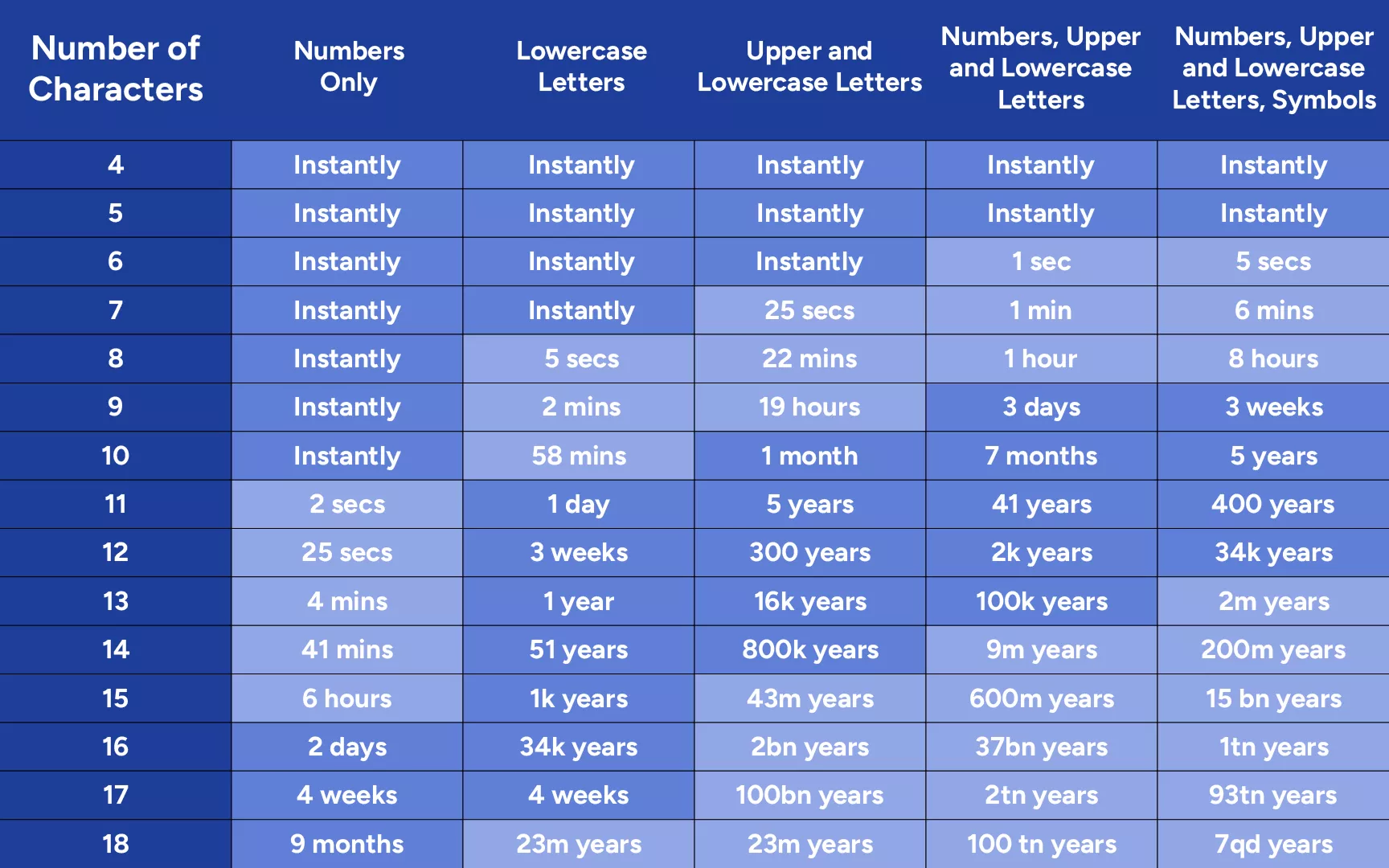
On top of that, your passwords should not be very simple. A password’s resistance to being cracked increases with its length and the inclusion of diverse elements such as letter case variations, symbols, and numbers. Take a look at the image below to see how long it takes a hacker to decipher your password with “brute force” (by simply trying to find the right symbols). That is why the use of password manager and password generation software (Bitwarden, 1Password, and Dashlane would suffice) is essential to making your crypto as secure as possible.
We also highly recommend you back up your seed words and create a different password for your wallet, as well. While setting up your wallet software, you’ll most likely be asked to back up your seed words. If you’re new to crypto, skipping this step may be tempting. But you shouldn’t do it.
Note: Seed words are a series of random words generated by your crypto wallet during its setup. You can use them as an emergency backup to recover your account. Anyone with access to your seed words can access every account tied to these words.
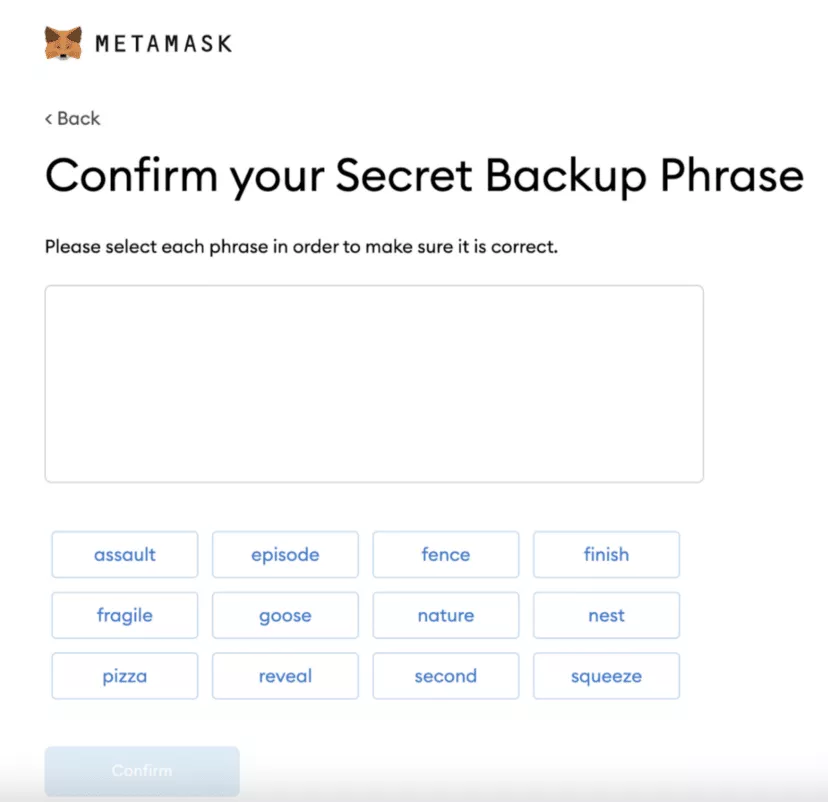
If you don’t back up your seed words, you will lose access to all your cryptocurrency the moment your device crashes. So, it’s better to write them down on a physical piece of paper and keep it in a safe place.
Use two-factor authentication and multisignature security
There isn’t such a thing as “too much security.” So, you should boost it with whatever means available, like two-factor authentication (2FA). The good news is that it’s present on most crypto exchanges and similar platforms. 2FA requires you to provide at least two verification methods, for example, a password and an SMS code, to access your account. This certainly makes breaches less likely.
But we suggest you go even further with taking care of securing your crypto and use a multisignature (multisig) wallet. A multisig wallet is a type of cryptocurrency wallet that requires multiple private keys to authorize a transaction. In a traditional cryptocurrency wallet, a single private key is used to sign and authorize transactions. However, multisig wallets add an extra layer of security by requiring more than one private key to make a transaction.
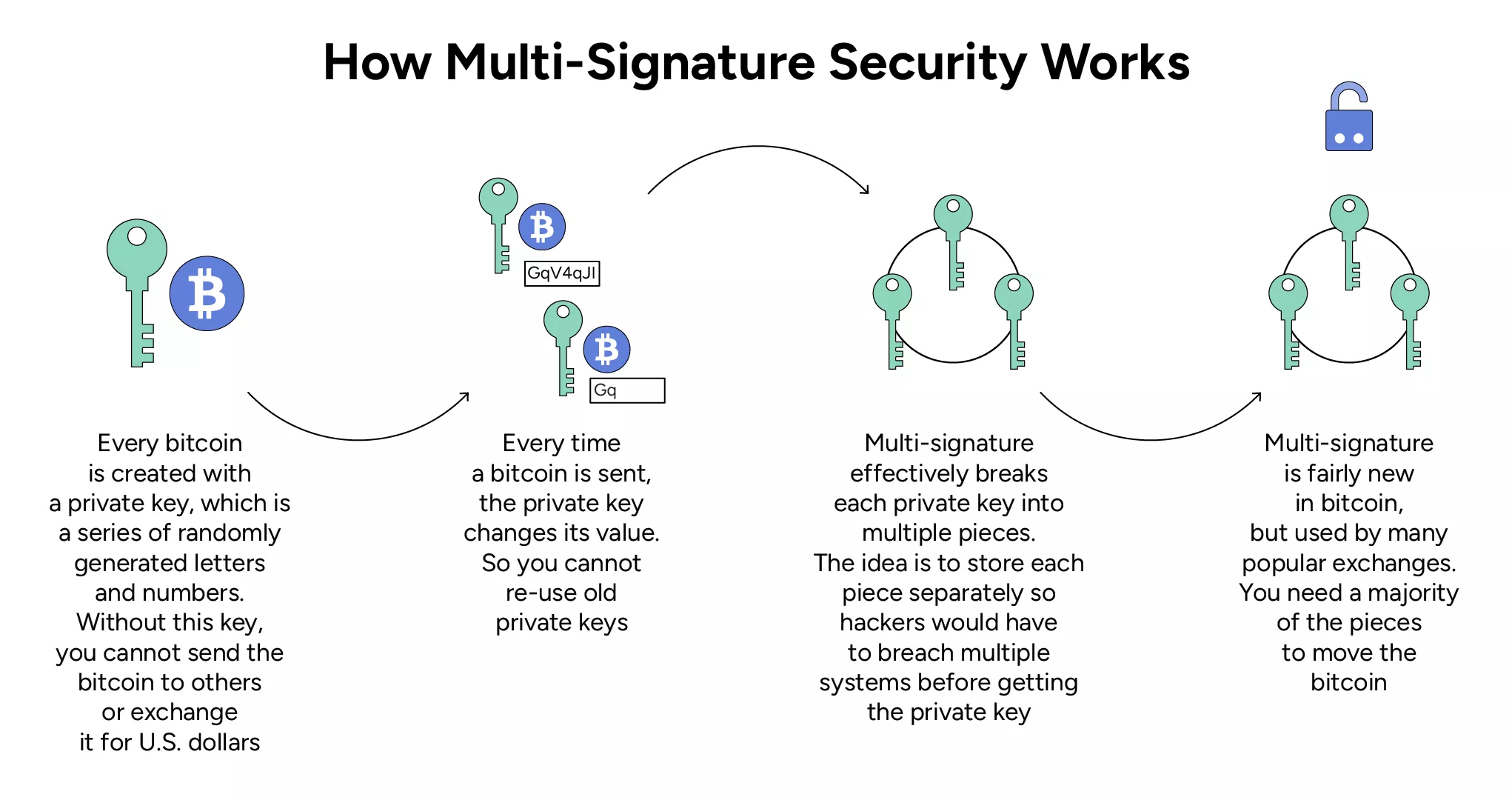
For Bitcoin, we recommend using such multisig wallets as Blue Wallet, Electrum, and Sparrow Wallet. As for Ethereum, pay attention to Safe Wallet and Rabby Wallet. Combined with hardware wallets, it’s the best way to protect your crypto!
Avoid fake software
With booms in crypto, an increase in fraudulent apps isn’t far behind. Yes, hackers can steal crypto by enticing a person to download a fake wallet or use a fake app. For example, there are plenty of fake versions of the popular Ethereum wallet. Scammers go as far as advertising these fakes on social networks. To avoid this type of scam, download a wallet from the developer’s official website only. That said, you should avoid click-through ads online.
Create wallet backups
In addition to the security measures we’ve already covered, creating backups for your software wallets is also an essential step for securing your crypto. Of course, so-called seed phrases are the most common method for backing up your wallet. However, you have to refrain from a temptingly easy way to record your seed phrase by writing it down on a piece of paper.
Instead, you can create a wallet recovery file. This file is encrypted and commonly stored on cloud services such as Google, Dropbox, or iCloud, allowing for easy wallet recovery. It’s important to note, though, that storing sensitive data in the cloud implies security risks.
The other way to back up your wallets is to use multi-party computation to split your private key into several components. These elements are stored both locally and remotely, thereby creating more barriers for hackers who attempt to steal your private key data.
Avoid public Wi-Fi
Find public Wi-Fi tempting? So do hackers! Doing crypto transactions on open networks makes you vulnerable, and anyone on public Wi-Fi can easily intercept your traffic. Hackers can often detect if you’re visiting crypto sites and can even see your transactions. This won’t necessarily let them steal your crypto, but your crypto activity out in the open for scammers is certainly not appealing.
This may be obvious, yes, but using secure Internet while logged into your crypto accounts is key. For maximum safety, consider investing in VPN. A good VPN will encrypt all of your data and hide your web activities from snoopers. Need more details? We’ve got you covered.
This may be obvious, yes, but using secure Internet while logged into your crypto accounts is key. For maximum safety, consider investing in a Virtual Private Network (VPN). A good VPN will encrypt all of your data and hide your web activities from snoopers. Need more details? We’ve got you covered.
Try VeePN – a top-notch VPN for crypto
Scammers will most likely come up with more ways to steal crypto. So taking care of your security is your go-to. But there is one way to hold your crypto and keep it safe whatever hackers come up with: to use VeePN.
Download a VeePN and have a 30-day money-back guarantee. At the moment, you can pay for subscription with Bitcoin (BTC), Ethereum (ETH), Ripple (XRP), Litecoin (LTC), Dash (DASH), Monero (XMR), Zcash (ZEC), and Bitcoin cash cryptocurrencies. Just like that.
Best ways to secure your crypto
To secure your crypto wallet, choose a reputable wallet type like hardware wallets, use a strong password and enable two-factor authentication. Regularly back up your wallet, keep software updated, be wary of phishing scams, secure private keys, and consider cold storage for significant amounts. Learn other ways to protect your crypto wallet in this article.
The best way to secure cryptocurrency is to use a reputable and secure wallet, such as a hardware wallet, employ strong passwords, and enable two-factor authentication. Additionally, consider cold storage for significant amounts of cryptocurrency and stay informed about the latest security practices in the cryptocurrency space. Find out other best practices in this article.
While cryptocurrencies don’t have a native “lock” feature, you can enhance security by using reputable wallets, implementing two-factor authentication, safeguarding private keys, and regularly backing up your wallet. Consider using a VPN service to protect your data online. By using a VPN app, all your data goes through a separate encrypted tunnel, thereby becoming indecipherable by hackers. In such a way, you hide your identity and relatable information that fraudsters may exploit to steal your crypto.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








