What Is an Evil Twin Attack and How to Prevent It

Some of the most unsettling cyber attacks are the ones you don’t notice as they happen. You may find your accounts suddenly hacked, your finances gone, and your private information posted on the internet without knowing where or when the breach occurred. You could be the victim of an evil twin attack.
Evil twin is a particularly sneaky form of cyber attack that can catch victims without them even realizing. Would you notice if you’d fallen into a scammer’s trap? Let’s examine the evil twin attack in detail and discuss how you can avoid becoming a victim.
When it comes to preventing an evil twin attack, using a good VPN is critical. VeePN encrypts all of your traffic, so even someone monitoring your connection can’t intercept any private information. On top of that, automatic Wi-Fi protection can help you avoid suspicious wireless networks. Install VeePN to secure your connection now.
What is an evil twin attack?
An evil twin attack uses a fake wireless access point that mimics another to trick people into making a connection. Because all data routes through the compromised network, scammers can intercept important information, such as passwords and financial transactions, in order to defraud you.
Fraudsters may use fake web pages that require login details to trick you into providing those details. Anyone who runs an evil twin network has complete control over what users see, where traffic goes, and what information gets intercepted and saved. If you use Wi-Fi — public or private — you’re susceptible to an evil twin attack.
What are the different types of evil twin attacks?
Captive portal and KARMA evil twin attacks are more complex variations of the same scam. While a standard attack is already quite sophisticated, hackers are always improving their tactics.
For example, the captive portal variation of evil twin generallyinvolves not only mimicking a seemingly-trustworthy Wi-Fi hotspot but also taking the legitimate network offline using a DDoS (Distributed Denial of Service) attack. With the real connection down, all users who intend to connect to that access point will unwittingly join the fake network.
Scammers could even use the captive portal variation of the evil twin attack on your home Wi-Fi or company network. If a connection drops, which sometimes happens for less nefarious reasons, most people wouldn’t think twice about reconnecting to what they assume is the correct network. But in the case of a captive portal attack, scammers replace the legitimate access point with an evil twin and direct you to a portal they control.
KARMA attacks use software to sniff out the trusted network lists of nearby devices. Many of us allow our phones, tablets, and laptops to automatically connect to access points we’ve joined in the past, and scammers can exploit this.
Once hackers know a trusted SSID (network name) they can mimic that connection and trick your device into automatically joining. The disturbing thing about this version of the evil twin attack is that you don’t need to manually connect to the compromised network.
How does an evil twin attack work?
While different types of evil twin attacks exist, the basic concepts are the same in most cases. Here’s how a typical evil twin attack works:
- Scammers configure and activate a fake wireless access point that resembles another nearby network
- People in the area connect to the compromised network expecting a safe connection
- Scammers monitor all traffic that passes through the evil twin network and save critical information, such as usernames, passwords, and credit card details
- Once satisfied, scammers shut off the connection and leave the area with all of the intercepted data
As you can see, you could fall victim to an evil twin attack and not even know it. The covertness of the connection and its resemblance to other public Wi-Fi hotspots in the area keep suspicion to a minimum. The scammer could take days, weeks, or even months to use the stolen information to defraud you, which makes identifying the causal event difficult.
Example of a real evil twin attack scenario
In 2020, hackers gained access to sensitive U.S. Department of the Interior networks using multiple methods, including an evil twin attack. Luckily, the perpetrators were performing tests for the Interior Office of the Inspector General and didn’t carry out the attack with malicious intent.
By using evil twin Wi-Fi hotspots, the team was able to capture the login credentials of authorized individuals and use those details to access legitimate networks within the department. While the hackers were trained IT professionals, they managed to successfully carry out the operation with just $200 of equipment.
Evidently, anyone with the right expertise and a bit of spare cash could perform a successful evil twin attack on a group of people, a company, or even a government organization. At this point, you should ask the question: how do you prevent an evil twin attack? Let’s find out.
3 steps to prevent an evil twin attack
Evil twin attacks can be difficult to spot, which means avoiding them takes serious effort. You can, however, mitigate the risks by following certain guidelines and being wary of every connection you make.
1. Don’t use auto connect
The KARMA variation of the evil twin attack relies on users automatically connecting to a trusted network. If you switch off the auto connect feature for your saved SSIDs, you’ll avoid falling victim to the scam.
Here’s how to stop an Android device from automatically connecting to a Wi-Fi network:
- Go to Settings > Connections > Wi-Fi
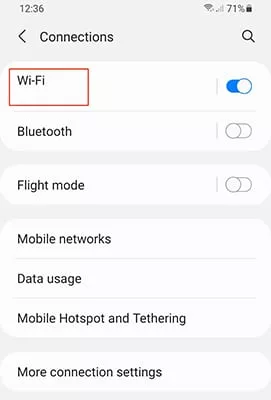
- Tap the More options button in the top right corner and select Advanced
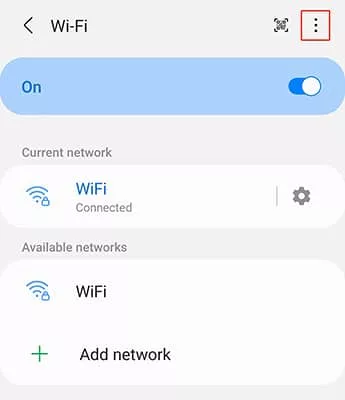
- Tap Manage Networks
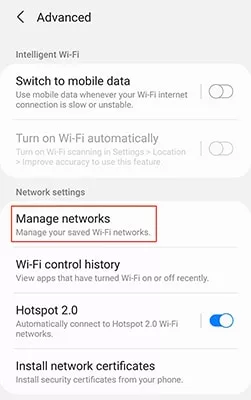
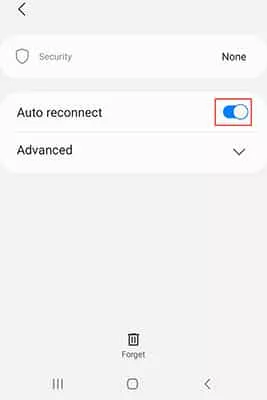
- Select the network you wish to modify and switch ff Auto reconnect
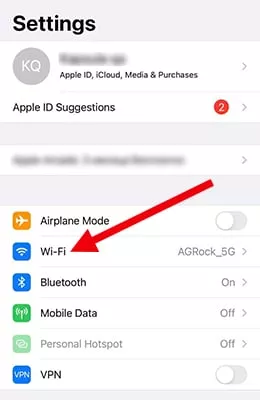
Here’s how to stop an iOS device from automatically connecting to a Wi-Fi network:
- Go to Settings > Wi-Fi
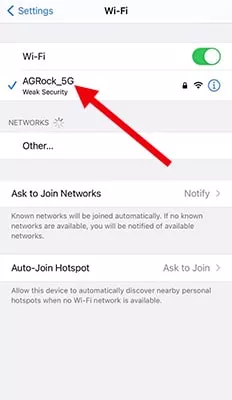
- Tap the network you want to modify
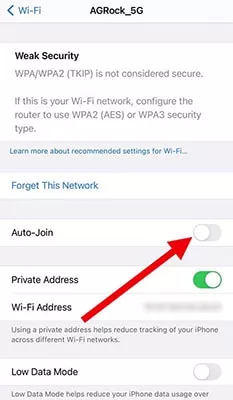
- Switch off Auto-Join
2. Avoid public Wi-Fi networks
Evil twin attacks that target individuals will generally attempt to mimic public Wi-Fi hotspots. Using an open network carries many risks, and you should avoid connecting whenever possible.
Sometimes, however, you may find yourself in a situation where you can’t avoid using public Wi-Fi. In those cases, you should take additional steps, such as using a VPN, to ensure that your connection is secure.
3. Use a VPN
Using a VPN is practically mandatory for anyone concerned about online security and avoiding evil twin attacks. A good VPN, such as VeePN, will encrypt your connection and hide your traffic from prying eyes.
On top of that, VeePN provides additional Wi-Fi protection tools to make using public connections safer and avoid getting caught in a scammer’s trap.
Here’s how you can utilize VeePN’s advanced security features to use public Wi-Fi more securely:
- Download and install VeePN
- Go to Advanced Preferences
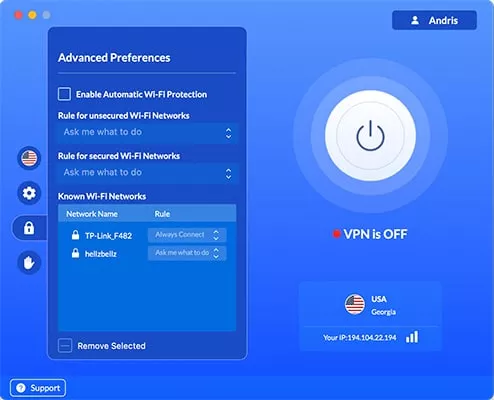
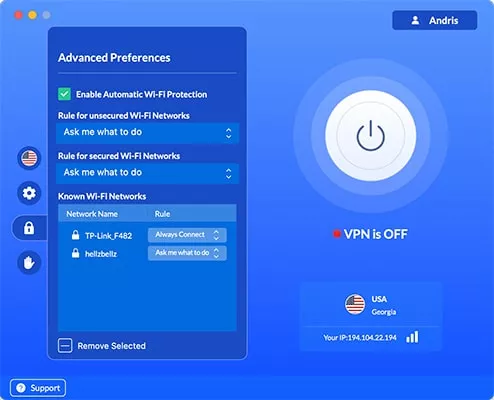
- Check Enable Automatic Wi-Fi Protection none;
- Turn the VPN on
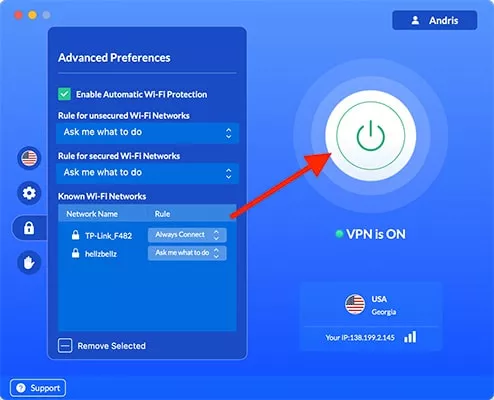
VeePN will now warn you whenever your device attempts to connect to a Wi-Fi network, giving you the opportunity to assess the situation and spot potential evil twin attacks. To play it safe, you should only ever connect to a trusted network.
Additionally, the VPN’s top-grade encryption effectively conceals your activity from anyone who wants to snoop.
Don’t be fooled by the evil twin
Evil twin attacks are sneaky, effective, and difficult to spot. If you ever need to use public Wi-Fi, you should always examine the connection first, only connect with a VPN, and not perform any sensitive tasks, such as logging into accounts, inputting financial information, or sending private messages.
Spotting the evil twin isn’t easy but once you know it exists, you’re in a better position to avoid falling for this sophisticated scam.
VeePN is freedom