Dark Web Monitoring: The Key to Safeguarding Your Data
Around 978,957 cases of data exposure on the dark web have been reported for the last 6 months, which is a 10% increase when compared with the first half of 2024. Owing to its anonymity, the dark web has become a convenient source of sensitive data hackers can use to attack their victims.
For that reason, many businesses start to front-run these threats and monitor dark web leak sites to know whether they’re at risk. In this article, we’ll describe what dark web monitoring is how it helps businesses stay protected, and what VeePN can do to shield your business from data breaches.
What gets sold on dark web leak sites?
Before we talk about dark web monitoring, let’s find out what information can be sold on dark web leak sites:

Stolen credentials
Your login details, email addresses, and passwords can be “a valuable asset for sale” on dark web digital marketplaces. Buying and selling personal information on the dark web has become a routine for hackers. The infamous dating site Ashley Madison data breach can provide a chilling example in this respect. In 2015, hackers exposed over 30 million user accounts, revealing personal information and causing significant personal and professional damage by selling their user’s credentials on the dark web.
Corporate secrets and intellectual property
No organization is immune to cyber attacks which means corporate secrets and other sensitive information often leak to dark web marketplaces. For instance, NVIDIA suffered a data breach, where hackers not only stole employee credentials but also leaked proprietary source code and design documents for sale. Such incidents can seriously damage a company’s competitive advantage, market position, and reputation.
Malware, ransomware, and phishing kits
Since the dark web has become a place where cybercriminals can prepare for their attacks anonymously, spread of such “services” as Ransomware-as-a-Service, phishing kits, and ready-to-go malware is also common. Anyone who intends to scam users and businesses can buy such instruments and target them towards their victims.
Under circumstances of constant threats stemming from the dark web, monitoring the hidden part of the Internet is essential for businesses if they want to be well-prepared for cyber attacks. So, it’s time to discuss how dark web monitoring works.
How dark web monitoring works
Dark web monitoring works like a specialized search engine, penetrating areas of the Internet invisible to conventional security tools. These dark web monitoring tools include:
🔎Threat intelligence. Continuous scanning of dark web forums, marketplaces, and communication channels to identify potential threats before they affect a company.
🔎Threat hunting. Proactively searching for signs of compromised data, leaked credentials, or planned cyberattacks targeting specific companies.
🔎Fast incident response. Rapid detection and mitigation of potential security breaches to reduce potential damage.
Benefits of dark web monitoring
Speaking about the major benefits of dark web monitoring, we can highlight the following:

😎 Keeps your sensitive data locked down. Dark web monitoring spots leaks before hackers can pounce, giving you a head start on securing your info before it’s exploited.
😎 Saves you from costly nightmares. Proactive monitoring = fewer data breaches. Fewer breaches mean no drained bank accounts, no ransomware shakedowns, and no stress.
😎Immediate detection: Companies have real-time awareness about potential security threats.
😎Dark web alert readiness: As soon as any digital threat emerges, businesses will know about it and take action to stay one step ahead of emerging threats.
But we need to say that dark web monitoring is obviously no silver bullet. That’s why you should take into account other aspects of cybersecurity to ensure 360-degree protection of your company.
Best practices to complement dark web monitoring
Adopting these best practices will significantly improve your cyber defense against various digital threats and complement your dark web protection activities:

☝️Educate employees. Human error remains the most significant security vulnerability. Regular cybersecurity training can dramatically reduce risks and raise awareness among your workers about the importance of cybersecurity in the company.
☝️Secure all endpoints. Implement comprehensive security protocols across all devices and network access points to ensure the risks of invasion “from the outside” are minimal.
☝️Use a VPN. Using a virtual private network (VPN) app is an essential layer of digital protection thanks to its ability to encrypt all your Internet traffic and mask real IP addresses. Actually, VPNs are an underrated cybersecurity tool ignored by many organizations. That’s why we would like to prove to you that using a VPN is essential for your digital security. Keep on reading to learn why!
How VPN enhances cybersecurity
Using a VPN can improve your online security in the following ways:
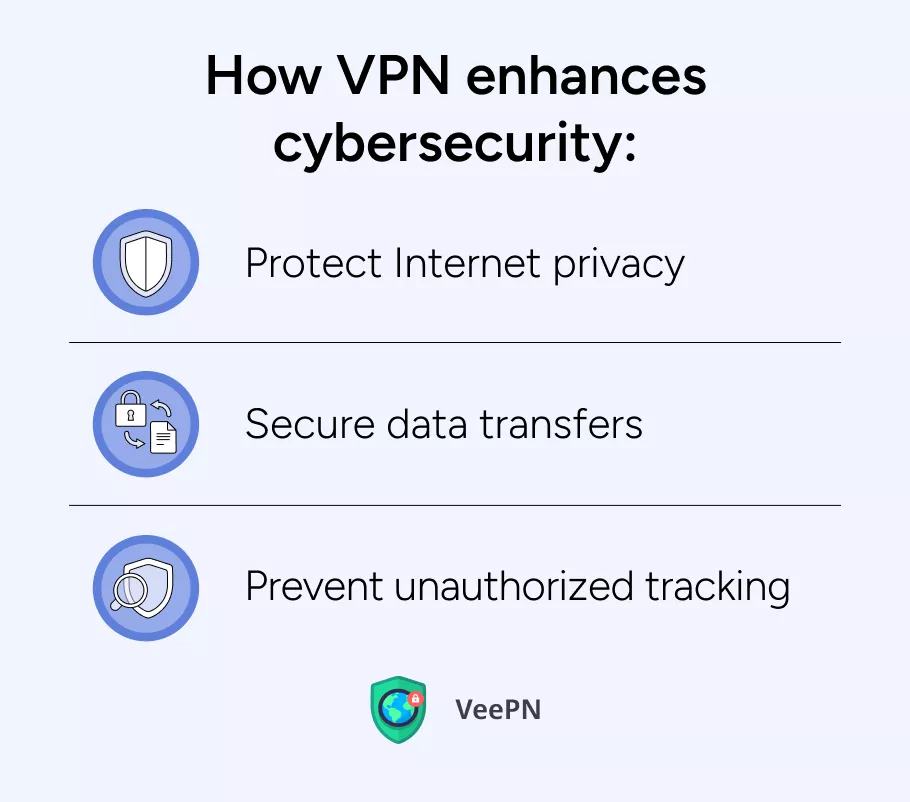
👍Protect Internet privacy. As we have mentioned, a VPN can encrypt Internet connections and mask IP addresses, so that nobody can see what your company staff is doing online and where it is located.
👍Secure data transfers. Since all Internet traffic is encrypted and goes through a remote server, you can create secure tunnels for sensitive information exchange.
👍Prevent unauthorized tracking. Once VPN lets you conceal your identity online, you can prevent tracking by third parties which ensures hackers won’t get any valuable information for preparing an attack on your company.
⚠️Warning: Free VPNs often lack robust security features and may even sell user data to third parties.
Why choose VeePN for cybersecurity protection?
VeePN can become your reliable cybersecurity tool as it offers a wide range of advanced security features and benefits such as:

🛡️Anonymous Email: Creates a fake email address that forwards all messages to your real one that remains anonymous in such a way.
🛡️Data breach scanner: When your sensitive information leaks, this feature will immediately notify you.
🛡️AES 256-bit military-grade encryption: The most reliable encryption standard to date. Even if hackers intercept your traffic, they won’t be able to decipher it without a unique decryption key.
🛡️Money-back guarantee. VeePN offers a 30-day money-back guarantee period, so you can test our solution without investing much money upfront.
VeePN is compatible with all major operating systems and platforms, so you can use one subscription with up to 10 devices. Get VeePN today to complement your dark web monitoring with a robust all-in-one cybersecurity tool!
FAQ
Yep! As long as you’re using a legit service, dark web monitoring is 100% safe. These tools scan sketchy marketplaces and forums for your leaked data without actually exposing your info. Think of it like a security guard for your personal details—if your passwords, emails, or financial data show up in the wrong places, you’ll get an alert ASAP. Just make sure you’re using a trusted provider to avoid scams or shady data collection.
Surprisingly? Yes! Using the dark web (through Tor or other tools) isn’t illegal—but what you do there absolutely matters. If you’re just browsing for research, privacy reasons, or curiosity, you’re in the clear. But if you’re buying stolen data, illegal goods, or doing anything shady, that’s a one-way ticket to serious trouble. Stay smart, stay legal.
For sure! Services like Have I Been Pwned, Aura, and other monitoring tools keep an eye on dark web leaks, scanning forums, databases, and shady marketplaces for stolen email addresses, passwords, and credit card info. If your data pops up, they’ll notify you, so you can change passwords and lock things down before hackers make a move.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








