What Privacy-Conscious Users Should Know About Encrypted SNI
Did you know that your online privacy can be compromised as soon as you request the server to enter a particular website? The thing is that the TLS 1.3 security protocol, which is supposed to protect your data from being tracked, lacks encryption at the very beginning of client-server communication. This is due to the SNI TLS extension that helps access websites with the same IPs, yet lessens users’ security at the same time.
Luckily, there is a solution to this issue called encrypted SNI (ESNI). It provides an additional encryption layer to keep your data away from hackers, censors, and online snoopers. But how does ESNI work exactly and is it enough to ensure your anonymity? Read on to find out.
What is SNI?
First of all, let’s cover the basics and explain the SNI meaning.
Server Name Indication (SNI) is an extension to the transport layer security (TLS) protocol which specifies a hostname in the TLS handshake. Simply put, the core purpose of SNI is to address the problem of accessing websites hosted on the same server and having the same IPs.
The mismatch between the common name or domain name of a website and an SSL certificate results in a “Your connection is not private” error.
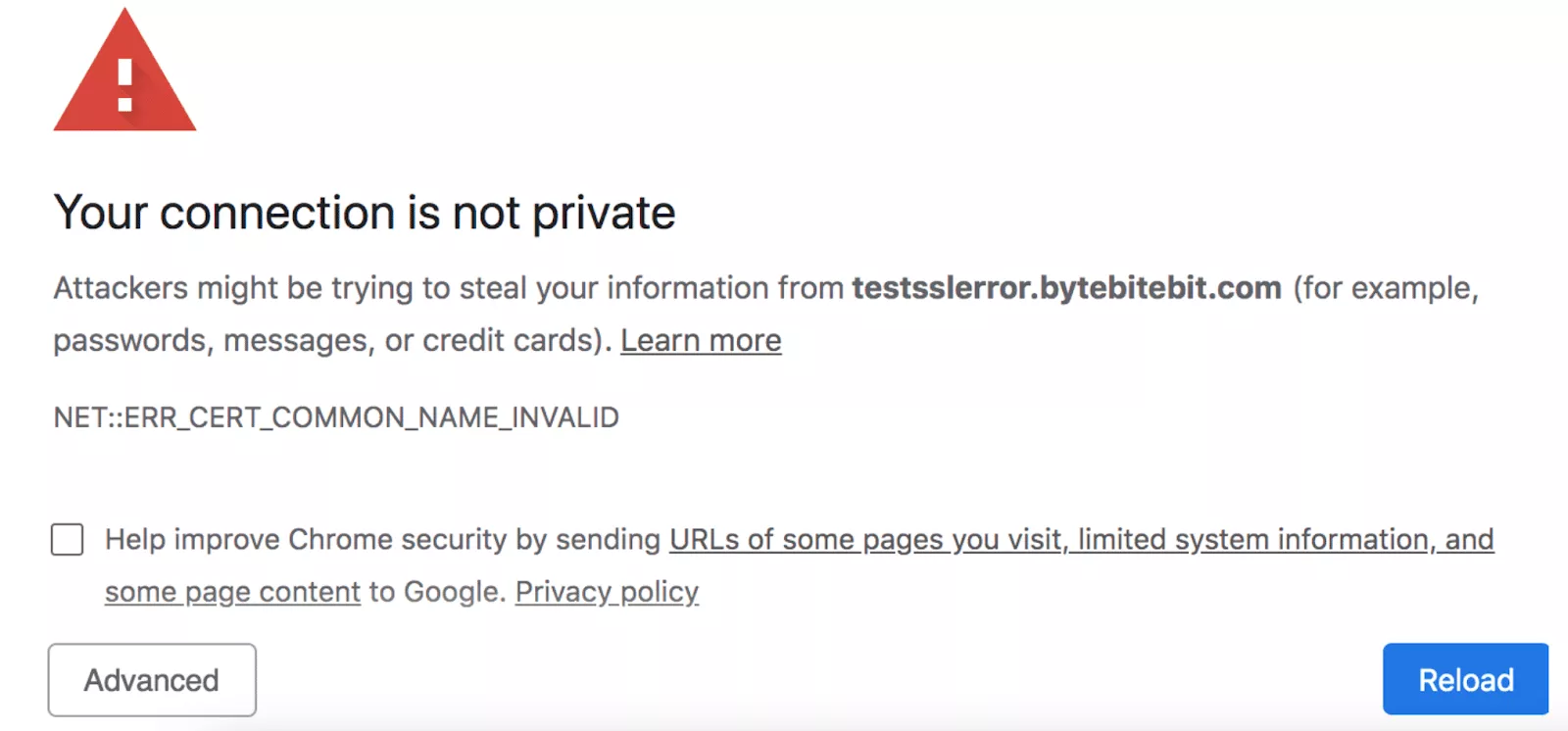
SNI helps avoid this error by enabling multiple IPs at the same TLS certificate. It streamlines the communication between a client’s device and a server hosting multiple websites with different domain names. But how exactly does it work, and what does it have to do with your privacy? Let’s clear things up.
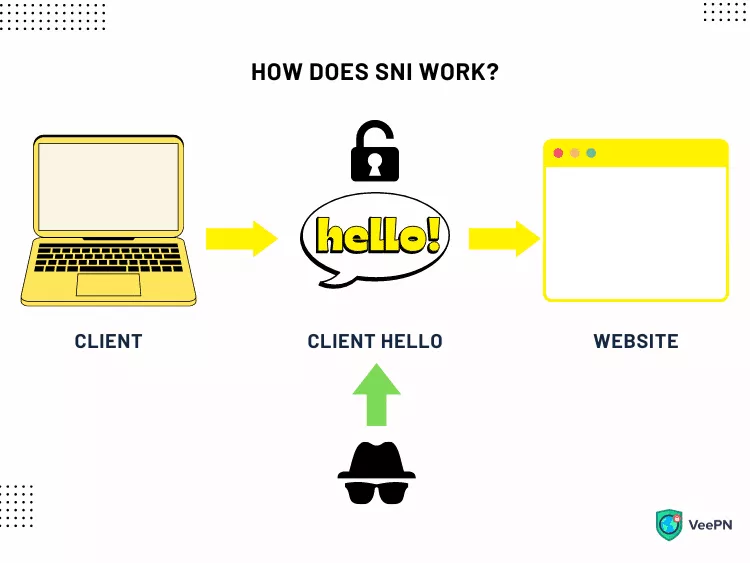
How does SNI work?
When a user’s device is sending a request to a server, their communication starts with the TLS handshake. This is the process of exchanging certain messages between the two parties involved. At this point, they verify each other, arrange the cryptographic algorithms, and adjust session keys. And here comes the SNI extension. It makes the hostname known at the beginning of the TLS process, called Client Hello, not afterward. As a result, there is no mismatch between your request and the website’s domain name.
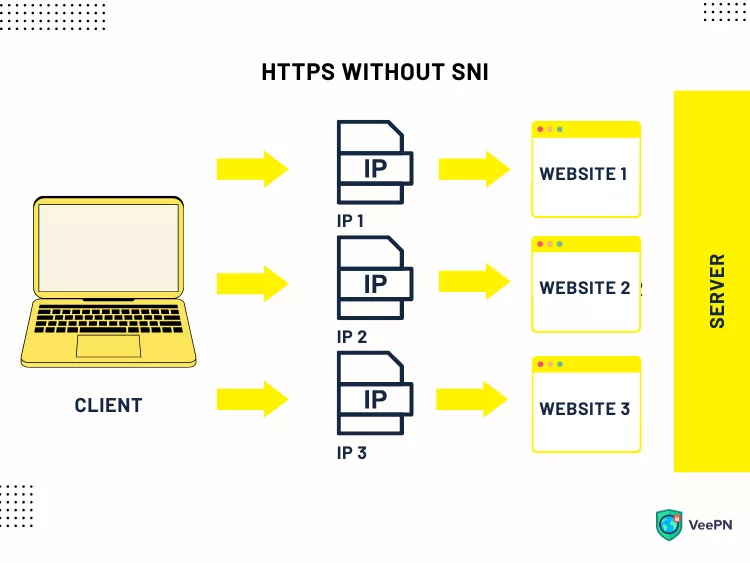
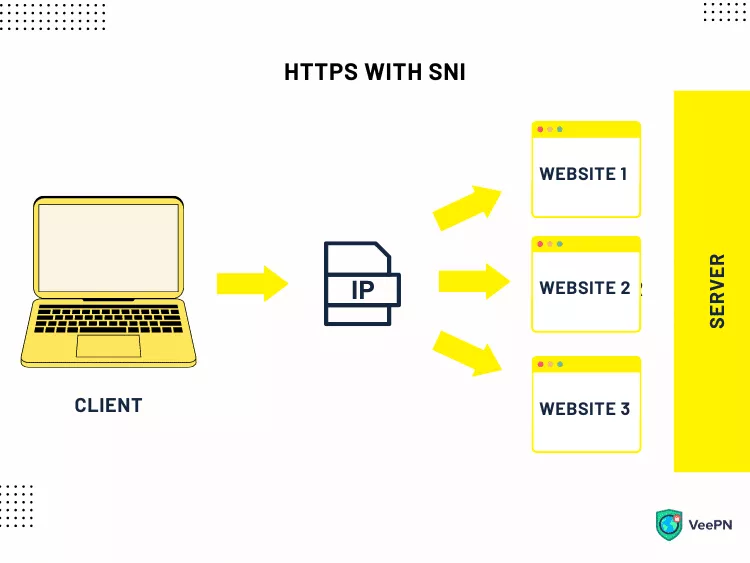
For example, you want to enter https://www.examplewebsite.com, which is hosted on the same IP address as https://www.anotherwebsite.com, https://www.examplewebsite.io, and some others. Thanks to the SNI extension, the connection will be instantly established, although the website’s name doesn’t match the SSL certificate name.
However, while SNI solves one of the most significant TLS issues, it causes another one instead. The initial phase of the TLS handshake lacks encryption, so this part of the users’ journeys compromises their privacy. Fortunately, you can overcome this challenge with the encrypted SNI.
What is encrypted SNI (ESNI)?
Now, when you know what SNI is and how it works, let’s clarify the meaning of encrypted SNI.
Encrypted server name indication (encrypted SNI or ESNI) is an additional feature of the SNI extension aimed at securing the initial phase of the TLS handshake.
Without SNI encryption, hackers can use various techniques, such as phishing or man-in-the-middle (MITM) attacks, to trick users, steal sensitive information, or redirect them to malicious websites. And that is the main reason why ESNI was created. It’s set to secure SNI as the most vulnerable stage of the TLS process, preventing online snoopers and third parties from spotting clients’ requests at the Client Hello.
Let’s look at how secure SNI works in more detail.
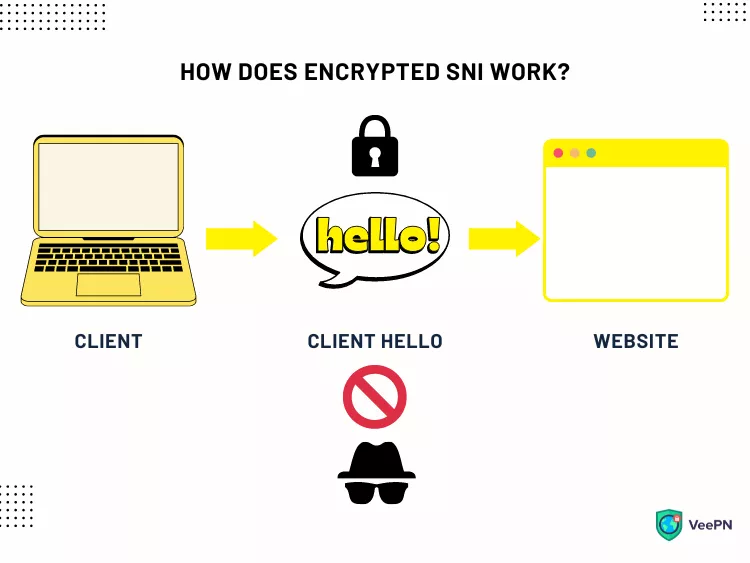
How does encrypted SNI work?
The key goal of encrypted SNI is to secure the connection between a client’s device and a server at the very beginning of their communication. The problem is that at the Client Hello stage, the TLS encryption keys aren’t yet approved.
To eliminate this vulnerability, encrypted SNI provides an alternative solution – a public key attached to the DNS record. This approach helps verify and secure the connection before the TLS protocol encrypts a user query. A client uses a public key that encrypts the SNI record, which can then be decrypted only by the relevant server.
To be more precise, here’s how exactly SNI encryption works:
- A user’s device sends a request to a DNS server to discover the site’s IP address.
- The DNS server’s response includes the website’s IP address and encrypted public key.
- The device sends a Client Hello request to the IP address, while the SNI is encrypted with the help of the private key.
- The server delivers the website’s TLS certificate.
- While the TLS handshake process occurs, no third parties can monitor the user’s current activity thanks to the encrypted SNI.
Unfortunately, SNI encryption is currently not supported by most web services and browsers. Some rare exceptions are Mozilla Firefox and Cloudflare. As for the most common uses of ESNI, it doesn’t only protect from nosy snoopers, but is also one of the most widespread approaches to resisting online censorship.
How encrypted SNI helps avoid censorship
Online freedom is one of the greatest concerns these days. According to the Freedom House, only eighteen countries have free access to the global web. Governments of totalitarian and authoritarian states strive to control the browsing activities to prevent people from viewing international resources and communicating via social networks or messengers.
In particular, online censors use SNI as the most vulnerable part of the TLS 1.3 encryption to determine users’ online activities and limit their access to certain content. At the Client Hello stage, censors, along with other third parties, can easily detect which server a person is trying to access and block it.
And that’s where Encrypted SNI comes to the rescue. It provides more Internet freedom by protecting every single stage of the user’s request to the server and hiding their traffic from Internet service providers (ISPs) and other third parties. However, to be completely reliable, ESNI can be empowered with some additional security measures.
What else do you need to stay private with encrypted SNI?
Except for ESNI itself, some additional security protocols will help you avoid unwanted monitoring even more effectively. Let’s take a closer look at the most important ones.
DNS over HTTPS (DoH) protocol
Even if you’re using ESNI, meticulous snoopers can still find a way to take a peek at your traffic. So it’s worth getting an extra security layer such as DNS over HTTPS protocol (DoH), which runs DNS queries through an additional HTTPS encryption session.
DNS over TLS (DoT) protocol
DNS over TLS (DoT) is another powerful network security protocol that encrypts DNS queries and responses through the TLS protocol.
Domain Name System Security Extensions (DNSSEC)
This set of specifications strengthens DNS protocols by ensuring cryptographic SNI authentication of responses coming from authoritative DNS servers. With the help of DNSSEC, you can enhance your protection against various cyber threats, such as DNS spoofing and hijacking.
Other ways to enhance your online privacy
If you’re striving to complete anonymity when surfing the web, there are many alternative ways to make your online activities invisible and well-protected. In addition to encrypted SNI with DoH, DoT, and DNSSEC protocols, you may consider the following Internet privacy tips.
1. Choose the most private browser
Many aspects of your online anonymity depend on the chosen browser. And guess what? The most popular browsers, such as Google Chrome, Microsoft Edge, and Safari, lack many important security features. At the same time, some less-known options can better protect you from third-party monitoring. To name a few, these are Ungoogled Chromium, Iridium, LibreWolf, Brave, Mozilla Firefox, and The Tor Browser.
2. Use a proxy server
You can also hide your online activities by spoofing your IP address and rerouting your traffic to a proxy server. However, while being quite effective for bypassing certain online limitations, proxy servers cannot fully protect your identity since they do not encrypt your connection. As a result, a proxy won’t keep you away from viruses and other cyber threats.
3. Protect yourself with a VPN
When it comes to private browsing and online security, a virtual private network (VPN) is probably the most powerful solution. A reliable VPN service can help you stay completely anonymous since your data travels through an encrypted tunnel and cannot be compromised by third parties. In general, VPN tools are focused on the following purposes:
- Hiding your IP address to make your online presence invisible to third parties
- Providing privacy and security features to protect your personal data from various cyber threats, including MITM attacks, phishing, and DDoS attacks
- Ensuring access to the free Internet and fighting against online censorship
Want to stay secure online? Try VeePN! It’s a trustworthy VPN service that protects your data thanks to the most powerful AES-256 encryption protocol. On top of that, VeePN provides the NetGuard feature to keep you safe from online trackers, intrusive ads, and third-party monitoring. And, if your VPN connection suddenly fails, VeePN will ensure no sensitive data will be lost with the help of the KillSwitch feature.
FAQs
What is SNI?
Server Name Indication (SNI) is a TLS security protocol extension that helps avoid hostname mismatch in the TLS handshake. It streamlines the communication between a client device and a server by revealing the hostname at the initial Client Hello stage. However, this TLS phase lacks encryption and is vulnerable to third-party monitoring.
What is encrypted SNI?
Encrypted SNI (ESNI) is an extra privacy feature securing the Client Hello phase of the TLS handshake. It encrypts SNI extension with the help of a DNS public key. As a result, the communication between a client’s device and a server becomes inaccessible for hackers and online snoopers. For more details, read this article.
Does TLS 1.3 support SNI?
Although the SNI extension wasn’t originally added to the TLS 1.3 protocol, it has become its essential component. Without TLS SNI, it’s impossible to run multiple SSL certificates on the same IP address. If TLS 1.3 lacks SNI, your connection to a server will likely be interrupted by a “Your connection is not private” error.
VeePN is freedom



