Symmetric vs Asymmetric Encryption: The Key Differences
Data encryption is an essential component of cybersecurity. Had we no encryption, sensitive data would easily leak into the wrong hands. Encryption turns any information into a code that is impossible to read without a special secret key. There are two ways data gets encrypted and deciphered with these keys: symmetric and asymmetric. But what’s the difference? Does it matter for your privacy and security after all?
In this article, we’ll compare symmetric vs asymmetric encryption and explain how both types impact your safety online.
Symmetric encryption vs asymmetric encryption. Two main types explained
To understand the difference between symmetric and asymmetric encryption, let’s review each of them, starting with a symmetric one:
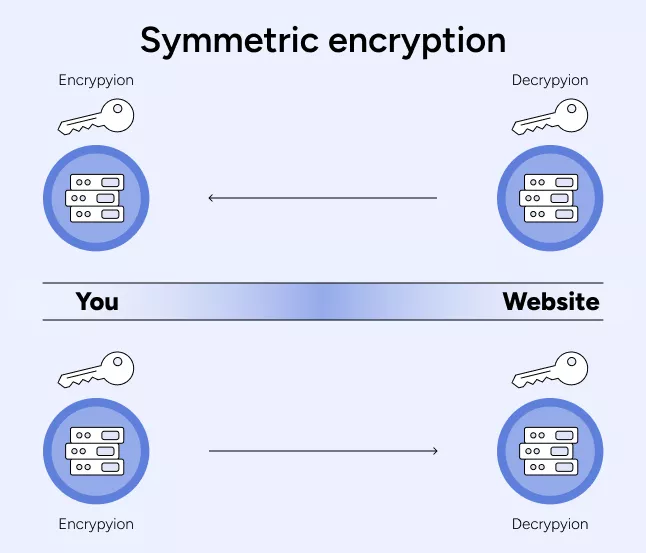
Symmetric encryption
The main peculiarity of symmetric encryption is that it requires data sender and receiver to have the same key. For example, when you access a website to watch your favorite anime or show, your device and the server must have the same key to exchange and read the coded data.
Even though symmetric encryption may seem straightforward, its main algorithms are designed to make your data as undecipherable as possible. There are several prominent symmetric encryption protocols:
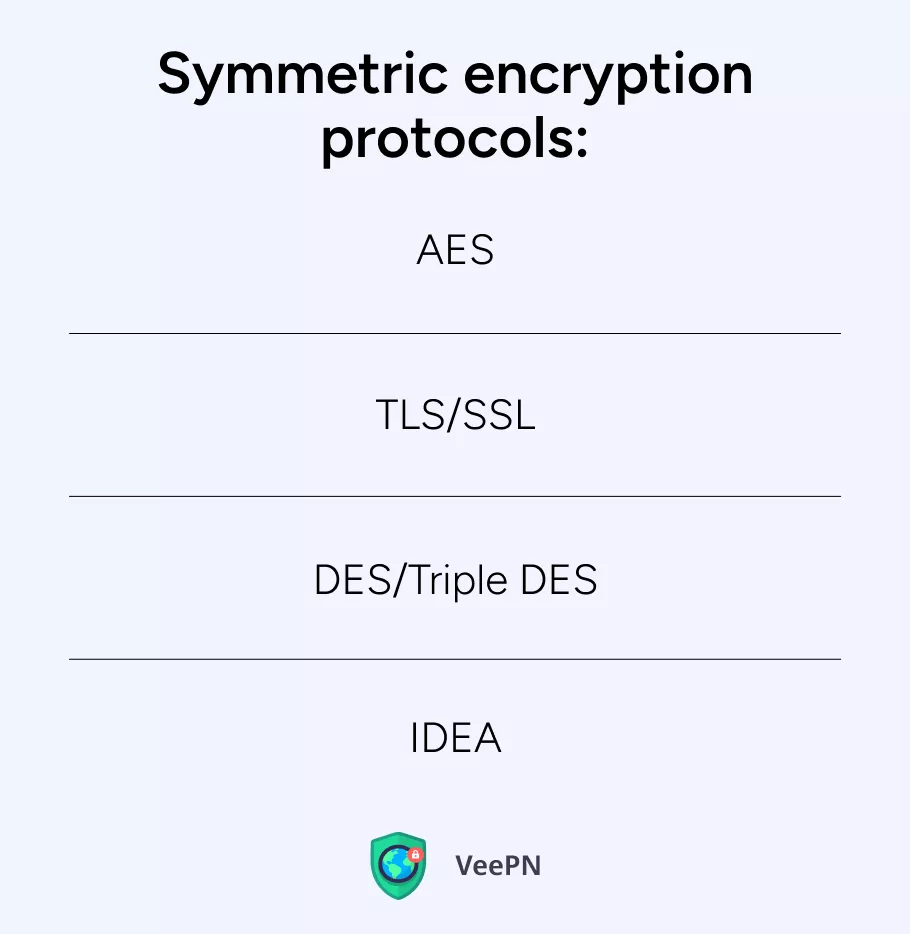
- AES. Advanced Encryption Standard is the most prominent and reliable protocol algorithm that is based on the Rijndael cipher. Think of encryption as a super-secure vault for your data. It takes your information, chops it into blocks, and scrambles it using complex math + a secret key. The result? A jumbled mess that’s impossible to read unless you’ve got the right key to unlock it. And when it comes to next-level security, VeePN doesn’t play around — it uses AES 256-bit encryption. What does that mean? The key is 256 bits long, making it insanely hard to crack. With 2^256 possible combinations, a hacker would need more time than the universe has existed to guess the right one. Basically, breaking it? Not happening.
- TLS/SSL. Transport Layer Security and Secure Sockets Layer are the most common protocols used for securing websites. Most web browsers rely heavily on TLS, so when a site you want to visit has an outdated TLS certificate, browsers like Chrome may deny access .
- DES/Triple DES. Data Encryption Standard is an old-fashioned standard that preceded AES and used the same principle, but much less sophisticated and secure. As for Triple DES, it is actually DES applied to every single data block three times. But in general, both protocols are extremely outdated and rarely used these days.
- IDEA. International Data Encryption Algorithm was expected to replace DES, but didn’t get much recognition, which is why you can seldom encounter it today. There’s not so much we can say about it.
And now, onto asymmetric encryption!
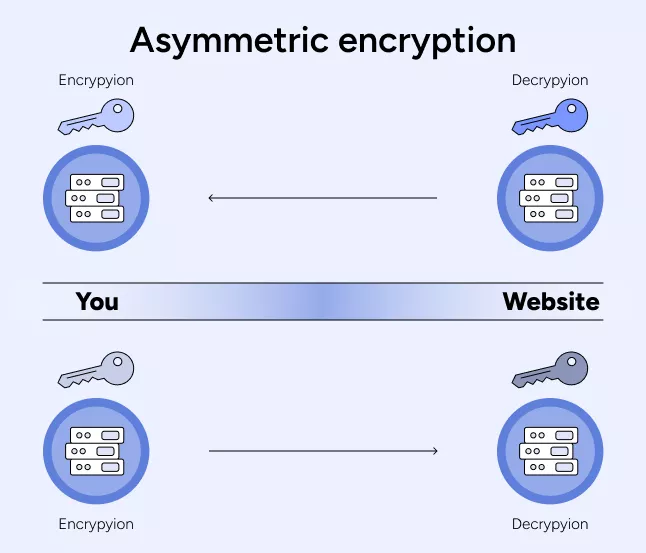
Asymmetric encryption
Unlike symmetric encryption, asymmetric one requires two types of keys: private and public. For instance, a VeePN as a VPN app connects to a remote server through an encrypted tunnel using a public key to the remote server. This server uses the public key to receive and encrypt data. Then the private key comes into play to decrypt the data and send it to the receiver. As a result, all your Internet traffic bypasses it’s usual “road” to websites, apps, games, and streaming services, but nobody can track what you do online.
To complete the above mentioned process, asymmetric encryption uses the following protocols:
To complete the above mentioned process, asymmetric encryption uses the following protocols:
- RSA. Named after Rivest, Shamir, and Adleman, this method is practically uncrackable, but also slower than a dial-up connection, which is why you won’t see it used in everyday apps and online services.
- Diffie-Hellman key exchange. Think of it as RSA’s speedier cousin. It still uses a key exchange system but makes the whole encryption process way faster, so data stays secure without slowing things down.
- TLS/SSL. We’ve discussed these protocols as a component of symmetric encryption, but TLS/SSL works perfectly with private and public keys as well. And if it works, why not then?
Now that we pinned down symmetric vs asymmetric encryption differences, here’s asummary table to round things up:
| Feature | Symmetric Encryption | Asymmetric Encryption |
| Key Type | Single shared key | Pair of public and private keys |
| Key Exchange | Requires a secure channel for key distribution | No secure channel needed |
| Encryption/Decryption | Uses the same key for both encryption and decryption | Uses the public key for encryption and the private key for decryption |
| Speed | Generally faster | Generally slower |
| Security | More secure if the key remains secret | More secure due to the difficulty of deriving the private key from the public key |
| Use Cases | Bulk data encryption, file encryption | Secure communication, digital signatures, key exchange |
So you know the difference between symmetric key encryption vs asymmetric, but we haven’t mentioned their use cases yet. Let’s explore when and where these two encryption methods are used!
When to use symmetric encryption
Speaking about symmetric encryption, it’s commonly used when:

- Speed and efficiency are paramount. Using the same key is definitely faster than using a public and then private one — that’s a solid advantage of symmetric encryption. That’s why symmetric encryption is crucial for cases when large datasets should be transitioned as fast as possible.
- Data security is a concern. Symmetric encryption uses complex coding methods which make it extremely good at protecting data from unauthorized access.
- Key management isn’t risky. Since symmetric encryption uses only one key, its handling and protection are critical. As a consequence, symmetric encryption becomes a priority method when key protection isn’t challenging because it can encrypt/decrypt data quickly and safely.
Common use cases
You can see the use of symmetric encryption in these cases:
- Data integrity protection. Symmetric encryption is perfect for protecting data that is stored on devices and various hardware but goes online. This type of encryption ensures that data is safe in its storage and can safely travel over networks without risks of being intercepted and cracked.
- Securing credit card credentials and personal information. Payment apps, web stores, online services and such require protection of their users’ banking information to avoid fraud and loss of money. Symmetric encryption is a perfect fit for such tasks as it can easily turn any sensitive information into gibberish no hackers and fraudsters can make sense of.
- Personal file encryption. If you have important files stored on your device, symmetric encryption can be a good solution to prevent unauthorized access to your information. You can even encrypt the entire databases or their separate components if necessary.
When to use asymmetric encryption
Asymmetric encryption is particularly good for:

- Risky key distribution. The risk of losing a decryption key is a major disadvantage of symmetric encryption. But that’s when an asymmetric method comes in handy as it uses public and private keys, making sure nobody will interfere in the data exchange.
- Need for secure communication channels. Asymmetric encryption can be used to establish secure communication channels, such as web browsers and messaging apps, where a public key is used to encrypt data, and the corresponding private key is used to decrypt it.
- Symmetric key exchange. When symmetric keys require a secure exchange, an asymmetric method comes to help its counterpart. The use of two keys is one of the main benefits of asymmetric encryption and it ideally serves the purpose of securing symmetric key exchange from hackers. For such cases, the use of RSA or Diffie-Hellman encryption is commonplace.
Common use cases
The most common use cases of an asymmetric encryption are:
- Email encryption. With the use of TLS/SSL, emails get protection from third-party access to prevent hackers from reading your email messages.
- Digital certificates. Asymmetric encryption uses its core principle of public and private keys to verify the identity of an individual or organization that uses digital certificates.
- Authentication and digital signatures. Verifying the authenticity of digital signatures is also one of the most common use cases of asymmetric encryption. The private key is used to sign a message, while the public key is used to verify the signature.
Both symmetric and asymmetric encryption play a huge role in keeping digital communication locked down. Symmetric encryption? Super fast and perfect for encrypting massive amounts of data in a flash. Asymmetric encryption? It steps in to securely handle the key exchange, making sure no one snatches your decryption keys.
One of the best real-world examples? Virtual private networks (VPNs). These privacy powerhouses use encryption to shield your Internet traffic from snoops, hackers, and trackers. Stick with us as we break down how these two encryption types work together in VPNs—and why they’re a must for staying secure online.
How VPNs use symmetric and asymmetric encryption methods for enhancing your security
To start with, you need to understand how a VPN app works. When your VPN app is active, it transitions all your Internet traffic through a secure “tunnel” where it gets encrypted and goes to a remote server and then to the server of a service you want to access. Making such a “hook” in data’s way to the endpoint, enables you to hide your IP address and conceal your identity online.
And now, let’s see how this happens in detail:
Asymmetric encryption for key exchange
Asymmetric encryption comes first in protecting your data with VPN:
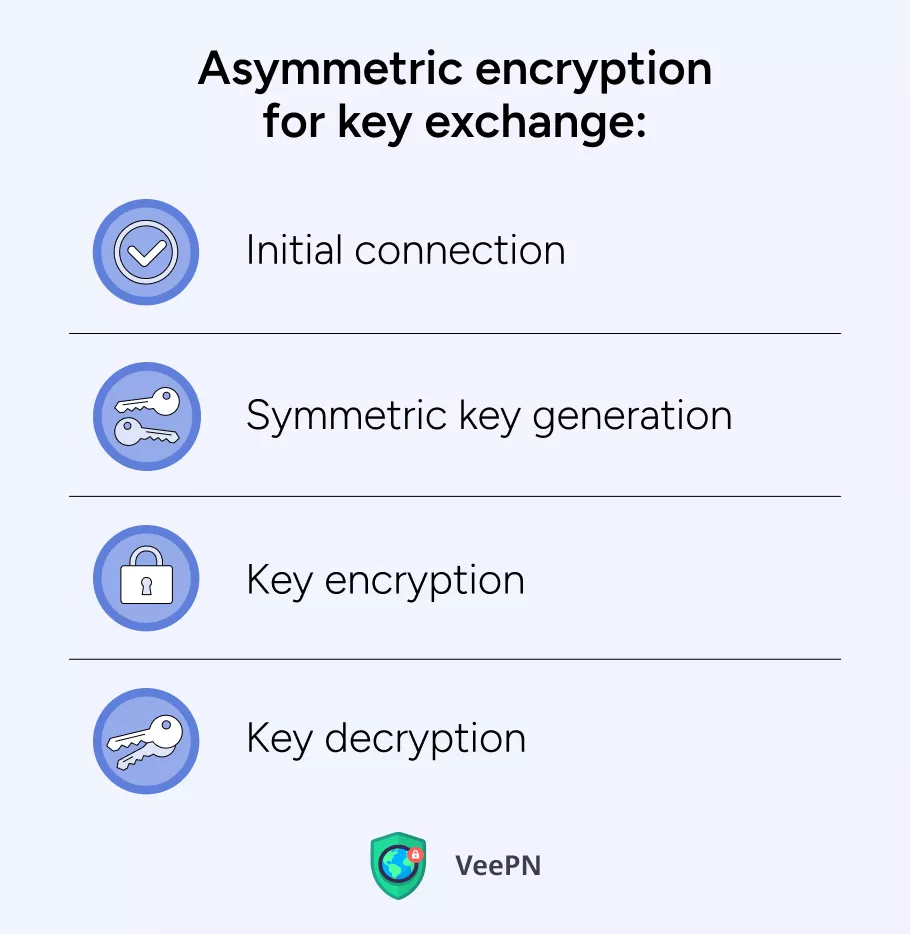
- Initial connection. When a user connects to a VPN server, the server sends its public key to the user.
- Symmetric key generation. The user generates a random symmetric encryption key to be used for subsequent communication.
- Key encryption. The user encrypts the symmetric key using the server’s public key and sends it to the server.
- Key decryption. The server decrypts the symmetric key using its private key, obtaining the shared data.
Symmetric encryption for data transmission
The role of symmetric encryption in securing your data with VPN is rather simple:
- Data encryption. Once the shared symmetric key is established, all subsequent data transmitted between the user and the VPN server is encrypted using this key.
- Data decryption. The VPN server decrypts the data using the same symmetric key, and then forwards it to the destination.
We have to highlight that free VPNs commonly lack reliable encryption protocols, which is why they still can be unsafe to use. At the same time, we suggest you try VeePN — a premium VPN app that uses the most reliable encryption method. There’s a common belief that VPN encryption seriously slows down the Internet speed, but VeePN uses a WireGuard® protocol for optimized data encryption and ensuring high connection speeds. In addition to solid encryption, VeePN offers extra security features such as KillSwitch, NetGuard, and even Breach Alert — notifications about your personal data leakage.
Ensure your privacy and security with VeePN
We would live in a much darker world without symmetric and asymmetric encryption. Frauds, scams, and hack attacks would be even more widespread than they are today. However, your Internet privacy is still at risk as hackers and other malicious actors are extremely inventive in coming up with new ways of stealing your personal information.
You can safeguard yourself by using VeePN which offers bulletproof security but also lets you enjoy high-speed Internet connection, access games, and stream media even when you need to travel abroad. Subscribe to VeePN right now and use it on up to 10 devices without extra charges!
FAQ
Symmetric encryption is a cryptographic method where the same key is used for both encrypting and decrypting data. It is efficient and fast, commonly used for securing large amounts of data. However, the main challenge is securely sharing the encryption key between parties. Read this article to get more information about symmetric encryption.
Asymmetric encryption is a method that uses two keys: a public key for encryption and a private key for decryption. This method allows secure communication between parties without needing to share the private key, as only the public key is distributed. It provides stronger security than symmetric encryption but is slower and more resource-intensive. Read this article to learn more.
Symmetric encryption is used when large amounts of data need to be encrypted quickly, such as in securing databases, file transfers, and VPN connections. It’s ideal for scenarios where the communicating parties have already established a secure way to exchange the encryption key, like in closed networks or secure sessions. Check this article to explore the common use cases of symmetric encryption.
Asymmetric encryption is typically used in situations where secure key exchange is crucial, such as in digital signatures, secure email communication (for example, PGP), and SSL/TLS for secure web browsing. It’s also used to establish a secure channel for exchanging symmetric encryption keys in protocols like HTTPS. This article uncovers more details about the most widespread asymmetric encryption use cases.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








