Red vs Blue Team: Should Your Company Invest in These Tactics? Here’s What You Need to Know
The Red and Blue Teams are the cyber security Red and Blue Teams, respectively, specializing in distinct, but complementary roles in making your organization stronger. In the Red Team, the attackers (simulating real world cyber attacks) attempt to uncover vulnerabilities and in the Blue Team defend against these threats, to secure systems and data. Together they aid organizations in identifying weaknesses and build a strong security strategy.
In this article, we’ll dive into what each team does, how they work together, and how tools like VeePN can support both teams in securing sensitive information.
What are Red and Blue Teams?
In cybersecurity, the roles of Red and Blue Teams are foundational to understanding the defense strategy:
🔴Red Team responsibilities are to simulate attacks to identify vulnerabilities within an organization’s infrastructure and testing the relatable processes.
🔵Blue Teams defend against those simulated attacks, focusing on threat detection, prevention, and system resilience.
Let’s discuss each team in more detail:
Red Team overview
The Red Team has the mindset of the action-taker. The Red Team members advanced tactics and methods to breach security measures and gain access to the internal network, highlighting weaknesses in the organization’s defenses. That’s why the main benefit of red teaming is the provision of invaluable insights into potential areas of risk that require improvement. Red Team techniques typically include:
🔴Conducting penetration tests
🔴Using social engineering techniques
🔴Adopting tools that mimic real-world hacking methods

Blue Team overview
In contrast, the Blue Team members skills revolve around the organization’s defense. They analyze risks, implement security measures and continuously monitor company’s network for suspicious activities. Blue Team responsibilities involve:
🔵Developing security policies and incident response plans
🔵Monitoring system logs and network traffic for anomalies
🔵Conducting regular vulnerability assessments and threat hunting
So how do these teams differ? Bear with us to learn about the key differences.
Comparison of Red Team vs Blue Teams
To understand the competitive yet complementary nature of these security teams, let’s break down their objectives, tools and skill sets to see the key differences. Check the table below to understand how these two teams differ:
| Red Team | Blue Team | |
| Objectives | Identify vulnerabilities and simulate real-world attacks to improve overall security posture. | Protect the organization from cyber threats, ensure system integrity, and maintain data confidentiality. |
| Tools and methodologies | Uses sophisticated hacking tools, penetration testing frameworks, and social engineering techniques to challenge security systems. | Uses security information and event management (SIEM) systems, intrusion detection systems (IDS), and incident response tools. |
| Skillset required | Strong knowledge of offensive security, ethical hacking, scripting, and an understanding of security protocols. | Knowledge of defensive tactics, threat analysis, risk management, and familiarity with security compliance. |
While the Red and Blue Teams work towards disparate objectives (basically it’s offense versus defense), they have an identical goal — improving the enterprise’s security posture and security controls. These interactions can help provide a better understanding of the threats and vulnerabilities, and help in continual improvement of security practice.
Red and Blue Teams in practice
Companies that have successfully integrated Red and Blue Teams often experience enhanced organization’s security defense against cyber threats. Here are a few real-world red team and blue team exercises examples:
Case 1: Simulating a ransomware attack in a financial Institution
A large bank implemented a Red Team exercise to test its resilience against ransomware attacks. The Red Team, composed of ethical hackers, simulated an attack by phishing employees with realistic-looking emails containing malicious links. Once inside the security infrastructure, they escalated privileges and encrypted critical financial data to mimic a real ransomware scenario. Their goal was to test how long they could remain undetected and assess the response readiness of the Blue Team.
The Blue Team responded by monitoring logs and detecting unusual activity in user accounts. They used their Security Information and Event Management (SIEM) system to track down and isolate the affected systems within hours, preventing further damage. After the attack, the teams came together in a Purple Team debrief to discuss what vulnerabilities in the network security were exposed during the attack, improve phishing training for employees, and better detection mechanisms to respond to the attack faster.
Case 2: Preventing a data breach in a healthcare company
After a spike in healthcare-related cyberattacks, a healthcare provider used Red and Blue Teams to protect patient data. In this scenario, the team of Red Teamers played the role of a person in the organization that was attempting to leak sensitive data from within using compromised credentials. To defeat the Blue Teams’ defenses they tested weak points like unpatched software and misconfigured access controls to simply bypass the defense.
The Blue Team identified anomalies through unusual data access patterns flagged by their data loss prevention (DLP) tools. They quickly revoked the compromised credentials and applied additional controls, such as multi-factor authentication (MFA). The exercise not only revealed gaps in their access control policies but also led to better logging practices and more robust insider threat monitoring, safeguarding the organization against real breaches.
You may have noticed that both cases imply teams’ collaboration. And such cooperation even has its own term: purple teaming. This approach not only strengthens the organization’s security posture but also improves the teams’ capability. Purple Teams enable knowledge sharing by allowing defensive teams and offensive teams to learn how the other plays their game, which in the end makes for a more secure organization.
Besides purple teaming, you can advance the work of both teams by adopting a reliable VPN service to protect your Internet connection and data privacy.
Use VPN to support both teams
In addition to the efforts of Red and Blue Teams, the use of a virtual private network (VPN) can significantly improve your preventive security control. However, free VPNs often do not provide a reliable level of security, making it essential to invest in a premium service. VeePN is one such security tools that offers robust security features, including:
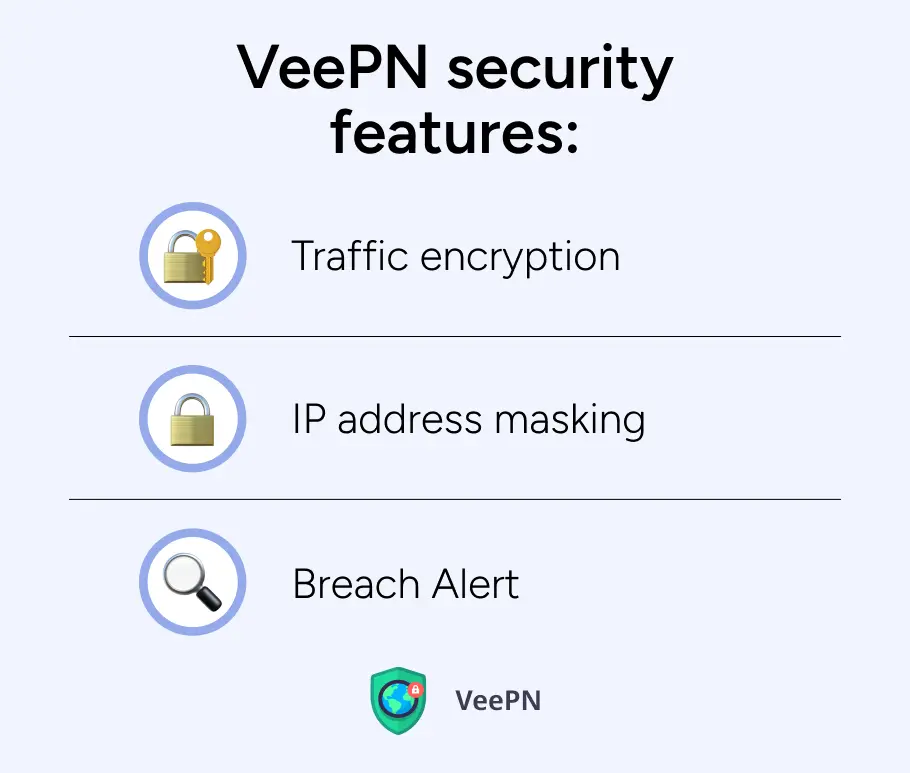
🛡️Traffic encryption: Protecting data in transit from interception and spying with military-grade encryption protocol.
🛡️IP address masking: VeePN passes traffic through a remote server to ensure the anonymity of both teams during their operations, allowing for more secure assessments and investigations.
🛡️Breach Alert: With this feature in place, your teams will be instantly notified of potential security gaps and breaches.
VeePN also provides an antivirus software for Windows and Alternative ID service that will help you improve security and privacy protection inside your company even further. Get VeePN today and secure up to 10 devices simultaneously with one subscription!
FAQ
In cybersecurity, neither the red team nor the blue team is inherently “better”: it’s a complimentary relationship. The Red Team simulates real world attacks to find vulnerabilities, and the Blue Team protects and fortifies systems by hunting down and defending against threats. Together they provide a balanced approach to making organizations more secure as a whole.
The Purple Team is a cybersecurity team that combines the Red (attack) and Blue (defense) teams. It creates conditions for easier collaboration that helps businesses to come up with defense strategies. The aim is to bring offensive and defensive efforts together to increase an organization’s security posture. In this article you can find more about purple teaming.
Red and Blue teams, augmented by a VPN, are able to secure an organization’s sensitive data. For example, during penetration testing VPN can mask Red Team’s activities and origins for detection. VPN adds a layer of encryption, allowing both teams to operate safely, without leaving any vulnerabilities. Read this article more about the role of VPN in corporate security.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








