Is TeamViewer Safe? Essential Safety Guide
Imagine that you are working on your PC, and suddenly the cursor gets crazy. What will be the first thing that comes to your mind? How will you feel? Perhaps most users will worry because somebody breaks privacy. That’s why you should be careful while using TeamViewer. In 2016, there were incidents involving external password breaches that allowed hackers to target users’ financial accounts, highlighting the necessity of security precautions when using the software.
It is an online collaboration tool that many people around the world use these days. It allows users to control other devices remotely, share the desktop, arrange online conferences and share files. But usually, it is used for letting another person install the software on your PC or fix some bug remotely. Only a single click and a definite individual get access to your device and all information you store. TeamViewer has so many advantages, among which are:
Simple installation and updating
Easy access to remote devices
Compatibility with major platforms
Free of charge
Assistance with increase sales potential
Help with quick and easy file transfer
Provides top-quality customer support
Helps detect issues to other users
Makes communication easier
Despite the high sensitivity of TeamViewer, lots of people trust it completely and use it regularly. But is TeamViewer safe or not?
What is TeamViewer?
Brief Overview of TeamViewer and Its Purpose
TeamViewer is a powerful remote access software that allows users to remotely access and control computers, share their desktop, organize online meetings, and transfer files. Its primary function is to enable someone else to take over a user’s computer remotely, which is particularly useful for troubleshooting issues or installing software. Given its sensitive functionality, TeamViewer requires high-level security measures, making it a trusted choice for both individuals and businesses who need to remotely access devices securely.
Explanation of Remote Access Software and Its Uses
Remote access software, like TeamViewer, provides the capability to access and control a remote computer or device from another location. This technology is incredibly versatile and has a wide range of applications. For instance, it allows IT professionals to provide remote technical support, enables teams to collaborate online regardless of their physical location, and facilitates remote work by allowing employees to access their work computers from home. With remote access software, users can seamlessly connect to their remote computers, ensuring productivity and connectivity no matter where they are.
What Security Features Does TeamViewer Have?
TeamViewer comes up with a high–quality standard AES 256-bit encryption and is also used by VeePN. It is equipped with two-factor authentication, whitelist trusted devices, and password reset for cases with suspicious activities. Relying on just a password is insufficient; two-factor authentication acts as an extra barrier against unauthorized access by requiring additional verification methods. Every person can easily improve the tool security by installing proper settings, including detailed access control. Despite all its well-known benefits, the actual facts prove that one must be very careful while using TeamViewer. There are a few unpleasant situations that lead to mass information leaks. Back in 2016, users had problems with PayPal and bank accounts, and in 2017 hackers took people’s devices under their control due to discovered vulnerability.
Luckily, the developers managed to fix the loophole immediately, and the problem was solved. As you can see, tweaking the settings of TeamViewer is important. Go on reading and find out how you can do it.
TeamViewer Security Features
Advanced Encryption Methods Used by TeamViewer
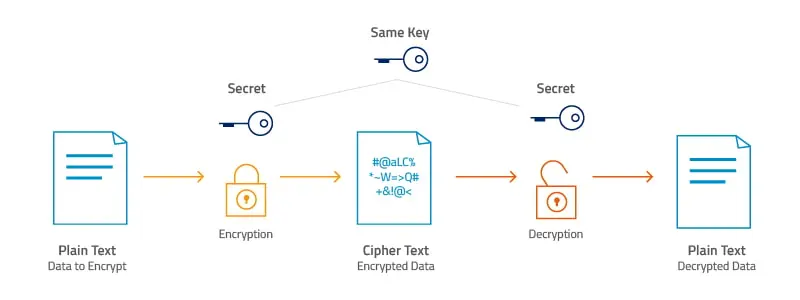
TeamViewer employs advanced encryption methods to ensure secure remote access. The software uses end-to-end encryption (E2EE) with 256-bit AES, which guarantees that data is fully protected throughout every remote session. Additionally, TeamViewer encryption uss RSA-4096 key exchange to secure data transmission. This robust level of encryption makes it extremely challenging for unauthorized users to intercept or gain access to the data being shared during a remote session. By implementing these advanced security features, TeamViewer ensures that only authorized users can remotely access and control devices, providing peace of mind for both personal and professional use.
The Ways for Improving TeamViewer’s Remote Access Software Safety
Consider a few effective tips on making your TeamViewer experience safer:
- Exit TeamViewer when you do not use it. It is recommended to open the program only when you use it. Avoid running TeamViewer in the background. Thanks to these simple steps, you can minimize the risks of becoming a subject of vulnerabilities. Visit the Remote Control section and refuse the option to start the TeamViewer system.
- Update the tool constantly. It will help you enjoy fresh security fixes for safe remote access.
- Strong passwords for better TeamViewer security. Password protection is essential to stop hackers from breaching your account. You can look for recommendations on how to create a strong password.
- Using two-factor authentication with TeamViewer. Thanks to it, you will build extra obstacles for hackers to penetrate into your account. A mobile device can receive one-time passcodes or host a 2FA app, providing a secure method for users to authenticate their identity. You need to visit the website of TeamViewer and let the system activate the option for you automatically.
- Always remember to check all devices that are recognized by your system and make sure that they are reliable.
- Refuse the easy access option. It allows the devices that you find reliable to connect to your account easily without any passwords. While it may seem to be quite convenient at first glance, actually, it makes your PC more prone to hackers’ attacks. It is recommended to enter the Remote Control section and untick the option called “Grant Easy Access.”
- Agree on whitelisting and blacklisting when it comes to the connection that you find reliable.
- Use a VPN. It will encrypt your performance, and nobody will be able to check your activities and penetrate them.
What Two Factor Authentication Option to Choose?
You can practice all mentioned above options to increase the chances of security using TeamViewer leaks and not let any hackers spoil your activities. Still, there is one that you should consider more than others. VPN is a good way to stay safe and do not worry about the leak of personal or business information. VeePN has proved to be a reliable server that has already helped thousands of people use PCs and stay assured about their own confidentiality. It hides the IP address of the device, guarantees anonymity, and provides top-grade AES-256 encryption. Using VeePN, you can be calm and do all necessary actions without any worries.
Conclusion: Preventing Unauthorized Users
TeamViewer is widely used by people and has already become one of all PC owners’ basic tools. Still, in the era of massive hackers’ attacks, it is very important to care about your own safety and do everything in your power to protect personal information. However, using remote access tools like TeamViewer can introduce potential security risks, such as weak passwords, outdated software versions, and improper configuration, which need to be addressed to ensure safe usage. Using VPN service like VeenPN is an excellent way to keep your data far away from all third-parties and reduce TeamViewer security risks . It allows using the PC safely despite your location. Once you get a 100% secure VPN, you can forget about all security issues and use your own device without any worries.
FAQ
TeamViewer can be safe for business use when configured correctly and used with strong security practices, such as two-factor authentication, strong passwords, and updated software. However, it has been targeted by cybercriminals in the past, so ensuring secure access policies and monitoring sessions is essential. For sensitive operations, consider alternatives with enhanced security features tailored for enterprise needs.
Hackers can potentially access your device through TeamViewer if your account or connection is not secured properly. This can happen if you use weak passwords, reuse credentials, or fail to enable features like two-factor authentication. To prevent unauthorized access, ensure strong security measures and monitor active sessions regularly.
Keeping TeamViewer running in the background can be safe if it’s properly secured with a strong password, two-factor authentication, and restricted access settings. However, it increases your exposure to potential threats, so it’s best to close the application when not in use, especially if you don’t need constant remote access. Regularly updating TeamViewer also helps mitigate security risks.
TeamViewer is designed with security in mind, offering encryption and features like two-factor authentication, but no tool is entirely immune to hackers. The risk often arises from weak user practices, such as poor password management or unprotected accounts. By enabling strong security measures and keeping the software updated, you can significantly reduce the risk of unauthorized access.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan







