What Is VPN Encryption and How Does It Work? (The Ultimate Guide)
When you’re using a VPN, it allows you to surf the web without anyone tracking your online activities. But what do VPNs do to ensure your privacy? The method they apply to protect your traffic is known as VPN encryption. When your data runs through the VPN tunnel, it’s turned into a ciphertext so that no snoopers can read it.
For instance, let’s say you’re sending a message to your friend saying, “Hi! How is it going?” When it’s encrypted, nosy third parties will only see gibberish like “fh! tsm dg lv hpetj?” Makes no sense, right? That’s the point! Thanks to encryption, only you and the person you’re writing to will be able to read the message.
Of course, VPN encryption is a bit more complicated than that. There are many technical details to consider when exploring this concept. But do not worry. In this article, we will talk about what VPN encryption is, how it works, and how to test its efficiency using no hard words – plain language only.
What is encryption?
Let’s start with some fundamentals and delve into what encryption is all about at a basic level.
Encryption — a way of encoding information in secret so it can only be understood by those with the right access. Because most of our digital lives now revolve around computing security, encryption has become very much a subfield of cryptography – which is why you see most online services, platforms & apps relying on encryption to shield sensitive data that gets either stored or sent via the web. Think of popular messaging service WhatsApp : they use end-to-end encryption to make sure your conversations stay private between users.
The encryption methods have changed and evolved over time. In the 1970s, IBM introduced DES (Data Encryption Standard), a cipher algorithm that encrypted data quite effectively at that time. However, it became vulnerable and was replaced with AES (Advanced Encryption Standard) at the beginning of the 21st century. Today, it’s used by most powerful security systems and services, such as VPNs (virtual private networks).
Now, without further ado, let’s talk about VPN encryption.
What is VPN encryption?
When a VPN runs your traffic through a secure tunnel to keep it invisible to third parties, it hides your data so that nobody can compromise it during transit. VPN encryption is the process of encoding information at both ends of this tunnel. It turns plain text into ciphertext, the complexity of which varies depending on the type of encryption used by a certain VPN service.
VPNs use different ciphers, some of which, like AES-256, are much more effective than others. We will soon discuss it in more detail. But first, let’s clarify a bit more why you need VPN encryption.
The importance of VPN encryption
Encryption is an essential component of a VPN. The main functions of a virtual private network majorly depend on the effectiveness of the encryption standard behind it. If it’s reliable, a VPN becomes an ultimate solution covering the following aspects of your online activities:
- Enhanced online security. In case a VPN service carefully encrypts your traffic, hackers will not be able to steal your information or infect your computer with viruses. Specifically, VPN encryption will keep man-in-the-middle attack, DDoS attacks, malware-infested links, and phishing sites at bay.
- Untraceable browsing. Apart from hackers, many other third parties may compromise your online privacy. VPN encryption won’t allow ad agencies, snoopers, and Internet service providers (ISPs) to track your activities and use your personal information for their own profit or apply Internet throttling.
- Access to the free Internet. When you have a coded VPN connection, you can overcome any actions on the web. Specifically, it will prevent rigid censorship of the Internet by the governments of many countries, such as China, North Korea, Iran, Russia, among others. In addition, upon visiting other countries, you will enjoy media streaming and consider your favorite content that is not available to you because of geographical restrictions.
All these benefits make VPN encryption a must if you strive to feel safe and free when going online. But how exactly does a virtual private network secure your traffic? It’s time to look under the hood of VPN encryption.
How does VPN encryption work?
Reliable VPN services provide end-to-end encryption. It means that your data is protected at every stage of the communication process. Even when the message or request is decrypted along the way, it’s still guarded from potential cyber threats. How? To begin with, let’s have a look at encryption keys, the core component of the VPN encryption process.
What are VPN encryption keys?
An encryption key is a string of information needed for encoding and decoding data. Simply put, thanks to the encryption key, only the person or device that has it can access encrypted data by decrypting it.
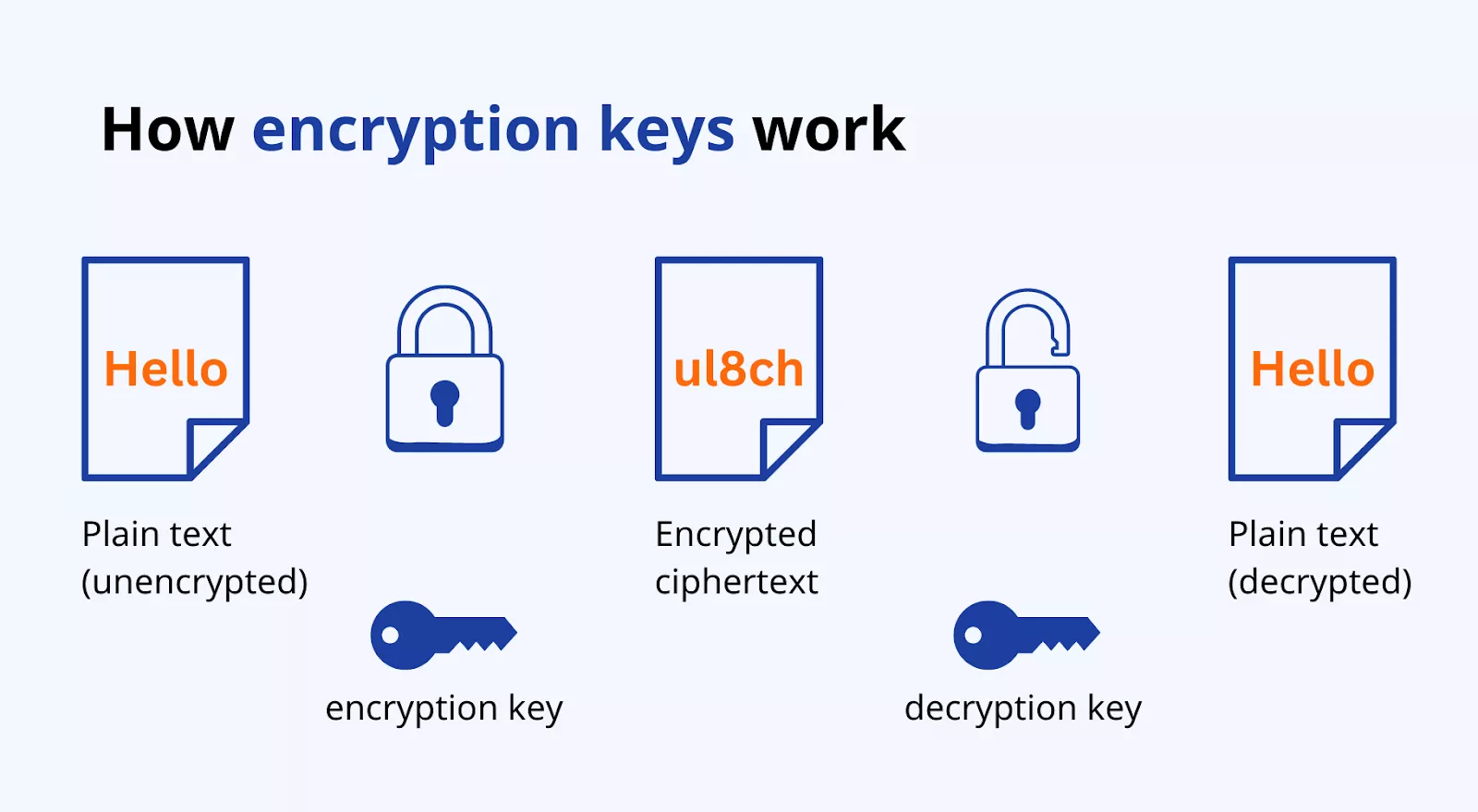
There are two main types of encryption keys, both widely used by VPNs: symmetric and asymmetric.
- Symmetric encryption keys. This kind of encryption gives the parties involved in the communication process the same encryption key. Think of a situation where you are sending a message to your friend. In the symmetric encryption technique, you get to encrypt your plain text into ciphertext with the aid of an encryption key and your friend is able to decrypt it with the same key. Yet, this method will not work in case the information being transferred out of your gadget has one more destiny – VPN server. And in this case, the asymmetric encryption comes into play.
- Asymmetric encryption key. With this approach, instead of a similar key, you and your friend will have to use two different encryption keys – a public key to encrypt the message and a private key to decrypt it. This way, the public key helps turn the message into code and then sends it to the owner of the private key, the only one who can decode it.
Most VPN services adopt both symmetric and asymmetric approaches when encrypting users’ data. While communication is based on the principles of asymmetric encryption, the keys are exchanged with the help of symmetric encryption. To better understand how it all works, let’s take a closer look at this process.
The stages of VPN encryption process
Let’s say you want to enter a website while using a VPN. Here is how it defends your data along its journey.
- When you’re entering a website, your request is sent to your VPN app or browser extension.
- Once your request arrives, the VPN app creates an encrypted tunnel that leads to a remote VPN server. That is where your data is encrypted so that no third-party trackers can access it.
- Next, your request moves to the website you want to access. When accepted, it returns to the VPN server.
- At this point, your data is encrypted once again and sent to your VPN client app.
- The VPN app decrypts the data and delivers it to you.
It may look like a complex, multi-level process. But in fact, all these steps take just a few seconds. The encryption occurs directly in the tunnel created for your data. In general, it consists of four essential stages. Let’s consider each in more detail.
Stage 1. Public and private key exchange. When your VPN app is connected to a VPN server, the encryption of your data starts with a handshake (the verification of secure connection between your device and a server). During this process, a private key and a public key are created with the help of the asymmetric exchange method. Your public key is sent to the requested server to encrypt your data so you can decrypt it with the private key.
Stage 2. Symmetric key exchange. After the asymmetric key exchange is over, the new key is created via the symmetric exchange. This adds an extra security layer, so even if your data was compromised during the previous stage, it’s still carefully protected.
Stage 3. Algorithm of encryption. The symmetric key adopts the encryption algorithm that is responsible for a safe journey of your data.
Stage 4. Final checkup. At this stage, integrity algorithms are used to verify if there are no mismatches in the information communicated via the encrypted tunnel and make sure no one has compromised it.
These four steps are the essentials of VPN encryption. However, the efficiency of this process is defined by the encryption standard used by a certain VPN service. This standard is a block cipher that splits your data into a particular number of blocks. Let’s discuss the most common types of ciphers and learn which one is the most secure.
Main VPN encryption types
These are the most common VPN encryption ciphers though not every one of them is equally powerful. Specifically, 64, 128 and 256 bits ciphers exist. In this case, it is notable that the greater the bits that a cipher offers, the more safe it is. It is important to note when using a VPN service, therefore, that you find out what type of encryption it uses.
1. Blowfish
The oldest VPN encryption standard is 64-bit with 64-bit blocks, which is blowfish. The most recent release of Blowfish allows 128bit encryption. Yet, it remains quite vulnerable and can be broken much easier as compared to its more contemporary counterparts.
2. Camellia
Camellia is a quite powerful block cipher available with the OpenVPN security protocol. Today, Camellia supports 64, 128, and even 256 bits encryption. However, it hasn’t been tested as carefully as the next encryption standard on our list.
3. AES
AES (Advanced Encryption Standard) is the most famous block cipher and a golden standard for modern VPN solutions. It is considered the most secure and powerful method to encrypt data and transmit it without the risk of being hacked.
Here are two main types of AES encryption.
- AES 128-bit encryption. AES-128 doesn’t require many resources and is faster than other encryption methods. However, 128 bits may not be enough if you prioritize your Internet privacy.
- AES 256-bit encryption. Today, this encryption standard is the most secure. It splits 256 pieces of common text into 256 blocks, making it simply impossible for hackers to steal your data with the help of a brute-force attack. Why? Because it would take them years to decrypt a single message or request. That is why all trustworthy VPN providers, including VeePN, use AES-256 encryption.
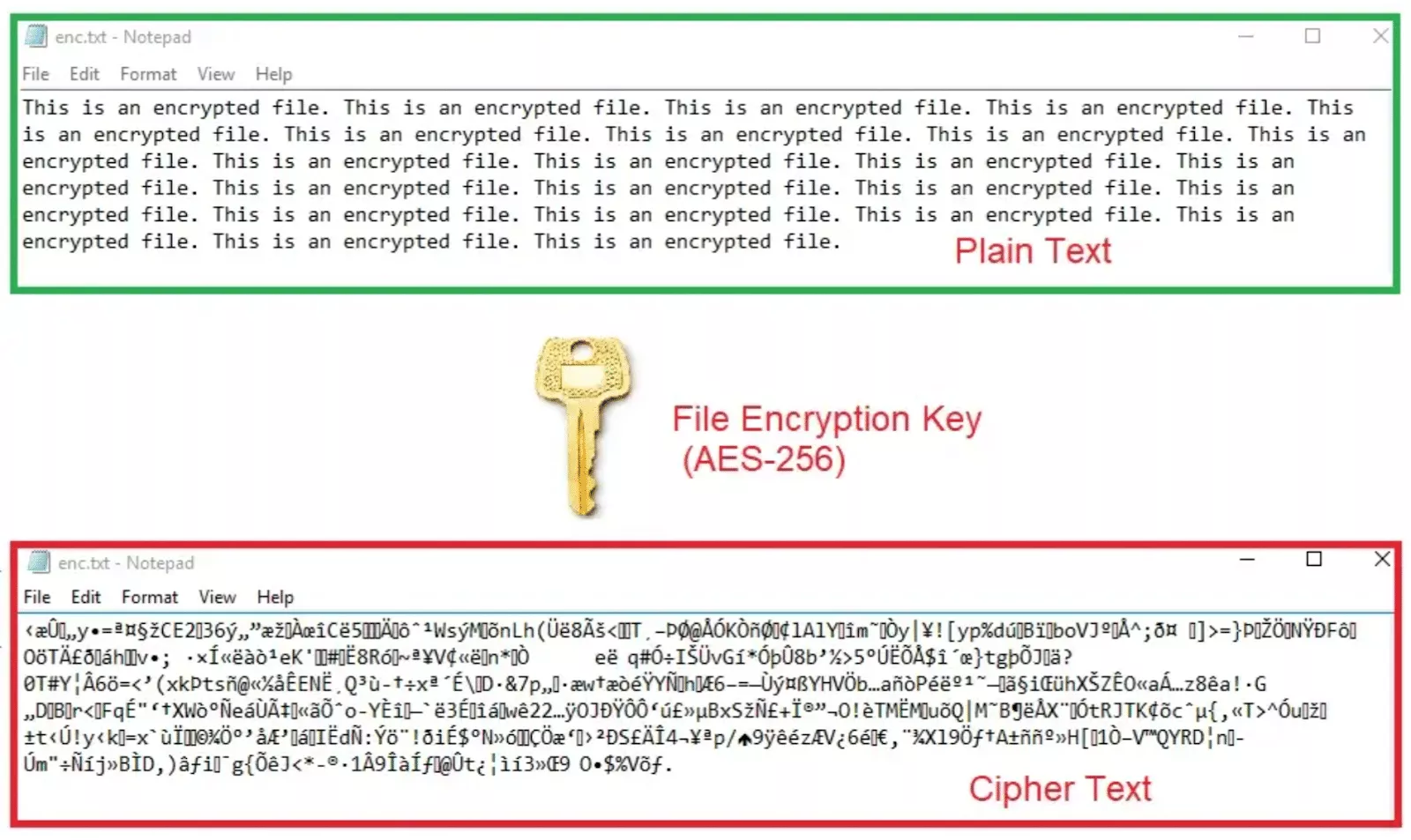
So this is it, now you know what VPN encryption is and how it works. But can you impact the way a VPN service encrypts your data? While you don’t directly participate in the encryption process, you can define its efficiency, as well as other aspects of VPN connection, by choosing a suitable VPN protocol.
VPN encryption protocols explained
A VPN protocol is a set of rules that define how your data is transmitted between your device and a VPN server. VPN protocols cover many aspects of the VPN connection, including its security, stability, and speed. And most importantly, the encryption type applied to your traffic also depends on the chosen protocol.
VPN protocols vary due to these and other factors. Some of them, such as PPTP, are outdated since they support only 128-bit encryption. Others have certain security vulnerabilities or may significantly slow down your connection speed.
Here are the three most effective and secure VPN protocols you can benefit from with VeePN. All of them are stable, fast, and work with 256-bit encryption. Each of them may suit you depending on your personal needs.
- OpenVPN is considered the most secure VPN protocol. It’s perfect for users who need to protect confidential information, perform money transactions, or stay safe when using public Wi-Fi.
- WireGuard is the fastest VPN protocol, so it’s perfect for online gaming and streaming media.
- IKEv2/IPSec is the most stable VPN protocol. You can use it to switch to mobile data trouble-free.
If you want to learn more about VPN protocols, read our recent blog post.
As it has been said, VPN encryption is a complex technical procedure occurring in the background. Nevertheless, you are able to follow the functionality to ensure that it will not lead to your personal information falling into the wrong hands.
How to check if your VPN connection is actually encrypted
The following tools will help you check how effectively a VPN encrypts your data.
Glasswire
Glasswire is a free tool enabling users to get quick reports regarding the performance of their VPN encryption. Here is how to use it.
- Download and install Glasswire on your device
- Open and start the program
- Open your VPN app and turn it on
- Start any browsing activities (play a video on YouTube, search for something on Google, and so on)
- In Glasswire, select Usage and head to the Apps menu
- Find the VPN protocol you’re using
- Verify the type of traffic and get the results of your test
Wireshark
Wireshark is a more advanced tool that allows you to check if your VPN provides reliable encryption. It’s worth turning to it when you’re using a free VPN or a service you do not fully trust. Here is how to run a test with Wireshark.
- Download and install Wireshark on your device
- Start the program
- Select your network type (it should be wireless if you’re connected to a Wi-Fi network)
- Click on data packets to test the encryption. If the result looks like an unreadable set of characters or gibberish text, the VPN encryption works properly.
Looking for a VPN with the strongest encryption? — Try VeePN!
VPN encryption may seem like a complex process at first. But in fact, it doesn’t require any manual effort or deep tech knowledge from you. All you need to do is pick a virtual private network you can trust, install it on your device, turn the VPN on, and there that is it! You can surf the web, remaining confident that your online privacy will not be violated.
Need a VPN tool that adheres to the most powerful encryption standards? Check out VeePN. It’s a trustworthy VPN provider that protects users’ personal information and prevents potential data leaks thanks to top-rated AES-256 encryption. Besides, VeePN offers many other essential cybersecurity features, including NetGuard, Kill Switch, and Double VPN. Get VeePN now and take advantage of a 30-day money-back guarantee.
FAQ
A VPN functions by scrambling your information and converting it to encryption a coded-up form of mess that is almost unbreakable. When you have a connection with VPN, then your internet traffic is picked up and sent through a tunnel with an unbreakable public key that is locked down – that is, the business you do online remains a secret. And to ensure that your information will be put back on your device intact, you can unlock it with your personal key when it gets to the other side. To provide you with an added protection, the best VPN systems run an over-solid AES 256-bit encryption – a very formidable code that fragments your data into bitesized portions. To know more about this, have a look at our article on this.
AES 256 — that’s the gold standard of VPN encryption used by every reliable VPN service out there. This encryption chops your data into 256 bite-sized pieces, making it a seriously long number – we’re talking a never-ending string of zeros. And that’s great news for your online security, because it would take a hacker an eternity to unravel such a complex code.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






