Cybersecurity Frameworks: What They Are and How to Choose the Right One
Welcome to the Cybersecurity Framework Olympics, where the top frameworks compete to secure your digital world. From NIST’s flexible risk-based strategies to ISO/IEC 27001’s global standards and CIS Controls’ laser focus on cyber risks, each has its strengths. Based on your unique needs — compliance, adaptability, or critical infrastructure protection — you won’t be left without a winner.
This guide will help you choose the right “champion” for your organization and show how tools like VeePN can add extra muscle to your cybersecurity defenses. Let the games begin!

Why cybersecurity frameworks matter
As organizations navigate the digital landscape, they face numerous challenges that can leave them vulnerable to cyberattacks. Some of these common challenges include:
⚠️Growing cyber risks targeting sensitive data.
⚠️Fragmented security measures leading to vulnerabilities.
⚠️Regulatory requirements demanding compliance.
Recognizing these challenges is the first step toward fortifying your defenses. Cybersecurity frameworks provide a detailed guide on how to adopt cybersecurity measures, allowing companies to manage their risks in the most effective way. Let’s review the most common cybersecurity frameworks.
Essential cybersecurity frameworks
Here are the main security frameworks and standards you should consider:

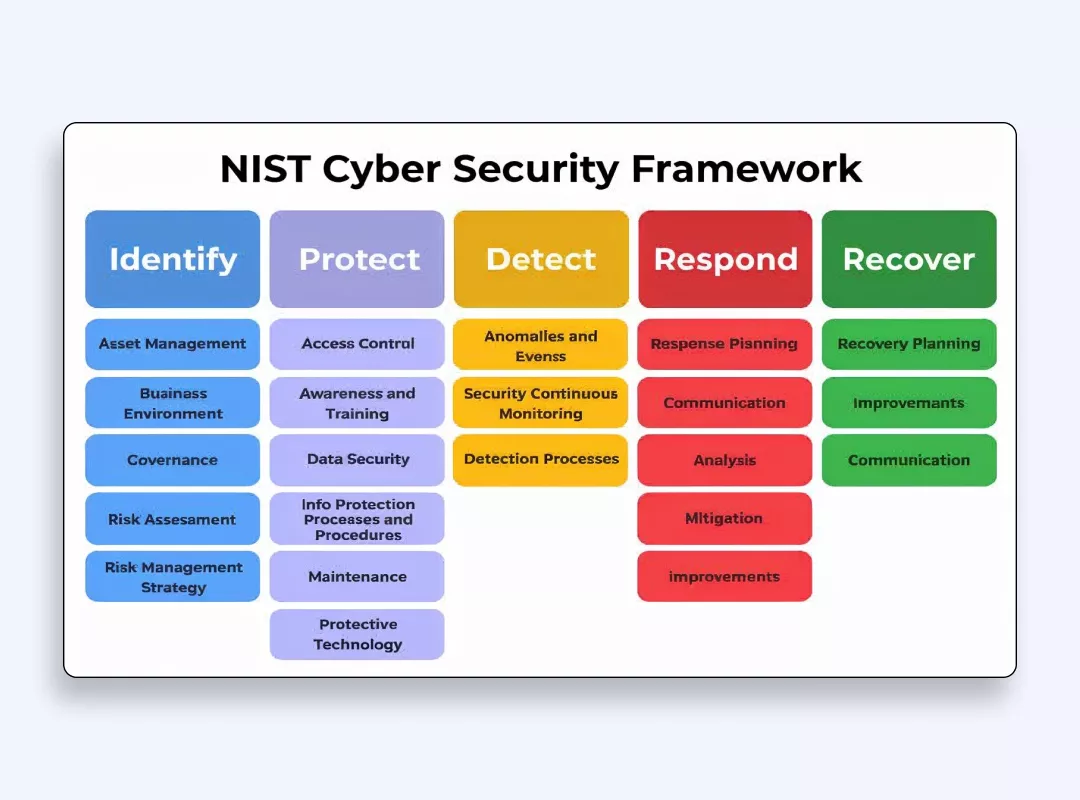
NIST Cybersecurity Framework (CSF)
The well-known adaptable framework helps improve critical infrastructure security through risk-based implementation techniques. This framework uses the Identify, Protect, Detect, Respond, and Recover steps to help organizations create their cybersecurity strategies.
The NIST CSF enables organizations to develop shared cybersecurity practices which apply across all business sectors. Organizations spanning multiple scales choose this framework because it improves their resilience against cyber attacks.
ISO/IEC 27001
This universally recognized standard includes all aspects of creating and keeping an information security management system (ISMS) operations in a loop of continuous improvement. Through ISO/IEC 27001, organizations acquire a comprehensive method to protect confidential information while ensuring its secure nature and preservation along with its accessible state.
An Information Security Management System enables businesses to detect potential risks and minimize them while connecting their security posture to organizational objectives and meeting regulatory standards. This standard allows businesses to build an improvement-oriented security culture which helps them adapt their cybersecurity approach to emerging threats.
CIS Critical Security Controls
The goal of CIS Controls is to directly confront cyber threats. This comprehensive cybersecurity framework helps organizations achieve effective cybersecurity by providing prioritized and immediately actionable strategies. The IT security framework comprises 20 controls which protect against recognized cyber threats:
- Inventory and control of enterprise assets. Keep an updated inventory of hardware devices connected to the network to ensure only authorized devices are granted access.
- Inventory and control of software assets. Track authorized software to prevent unauthorized or unmanaged programs from executing.
- Data protection. Identify, classify, and protect sensitive data at rest and in transit.
- Secure configuration of enterprise assets and software. Establish secure configurations for hardware and software to reduce vulnerabilities.
- Account management. Use principles like least privilege to manage accounts and reduce unauthorized access risks.
- Access control management. Limit access to systems and data to authorized users only.
- Continuous vulnerability management. Regularly scan your systems and applications for vulnerabilities and address them promptly.
- Audit log management. Collect, monitor, and analyze logs to detect and respond to anomalies or potential incidents.
- Email and web browser protections. Ensure email and web browsers are configured securely to block malicious content.
- Malware defenses. Use antivirus and other tools to detect, block, and remove malicious software.
- Data recovery. Regularly back up critical data and verify recovery processes to ensure availability after an incident.
- Network infrastructure management. Secure network devices, including routers and switches, to safeguard communications.
- Network monitoring and defense. Use tools to monitor, detect, and respond to unauthorized network activities.
- Security awareness and skills training. Educate employees on security best practices and conduct regular training to prevent human error.
- Service provider management. Ensure third-party providers comply with security requirements to protect organizational data.
- Application software security. Secure in-house and third-party applications through testing, patching, and secure development practices.
- Incident response management. Create and test an incident response plan to quickly address security breaches or disruptions.
- Penetration testing. Simulate real-world attacks to evaluate the effectiveness of security defenses.
- Secure network engineering. Design and maintain secure network architectures to minimize risks.
- Controls implementation for ICS (Industrial Control Systems). Tailor the implementation of controls to protect critical infrastructure and maintain secure systems across the company.
These actions emphasize implementing basic security hygiene and offer a roadmap for organizations to follow, making it accessible for teams with varying levels of expertise. By focusing on practical measures that can yield significant results, organizations can strengthen their defenses and respond swiftly to incidents. This framework is especially beneficial for those seeking clarity in a cluttered cybersecurity strategy.
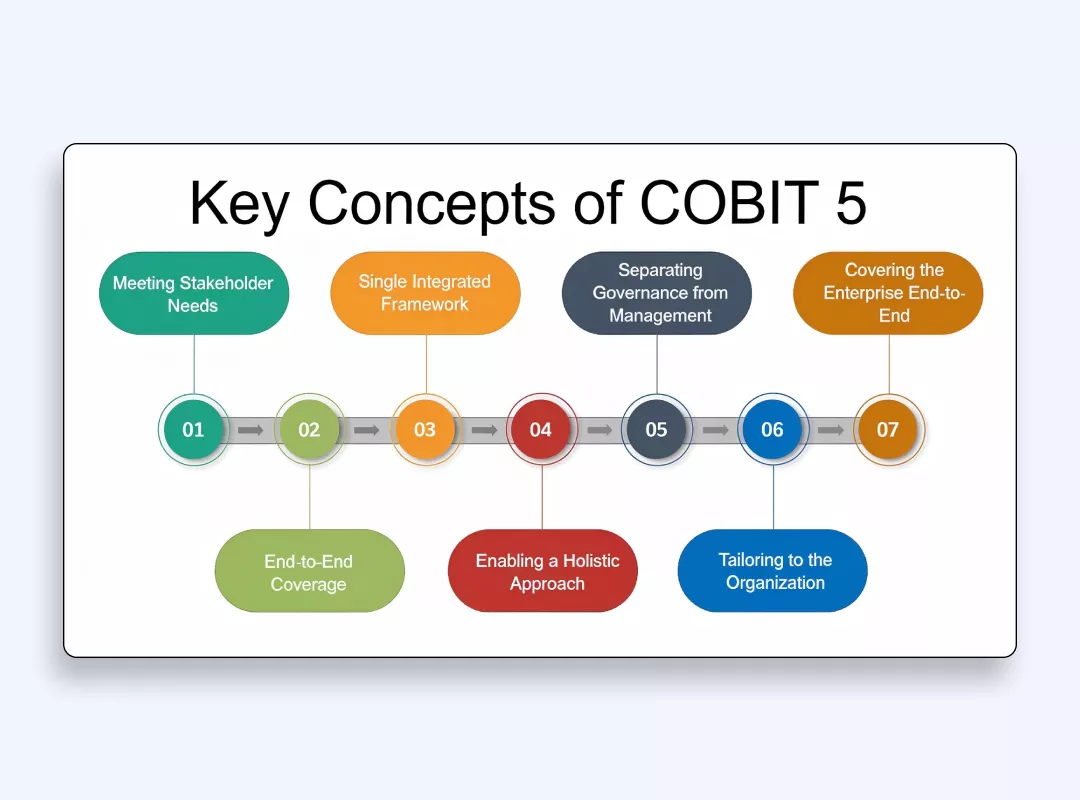
COBIT
COBIT manages IT governance through established best practices which link business targets to compliance requirements and IT resource use. COBIT establishes a detailed methodology which maintains connections between technical operational issues and strategic corporate goals. The framework establishes best practices for enterprise IT governance and management through a strategic approach to risk control and resource allocation and value generation.
COBIT helps organizations to successfully manage risks together with compliance requirements. The structured governance system enables transparency and accountability which supports organizations that target integrated cybersecurity management alongside IT governance frameworks.
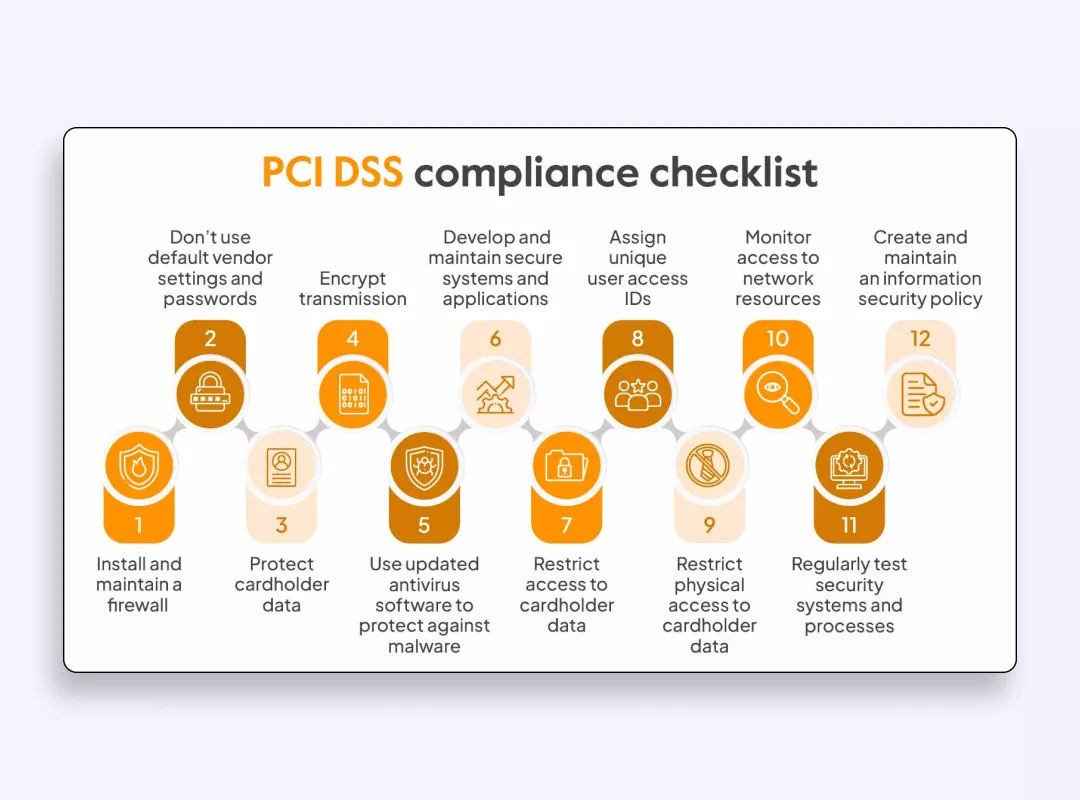
PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) protects cardholder data which makes it vital for entities processing credit cards. PCI DSS provides standard security requirements to businesses which help them protect cardholder data and minimize fraud risks. Businesses need to use encryption technology alongside access restrictions and regular monitoring protocols to meet PCI DSS compliance requirements.
The implementation of PCI DSS standards guarantees secure payment environments and increased customer trust. Every business that processes payment data needs to integrate PCI DSS frameworks because they create a strong shield against cyber threats.
Benefits of adopting a cybersecurity framework
Organizations can reap significant benefits by adopting a cybersecurity framework. Here are the key advantages:
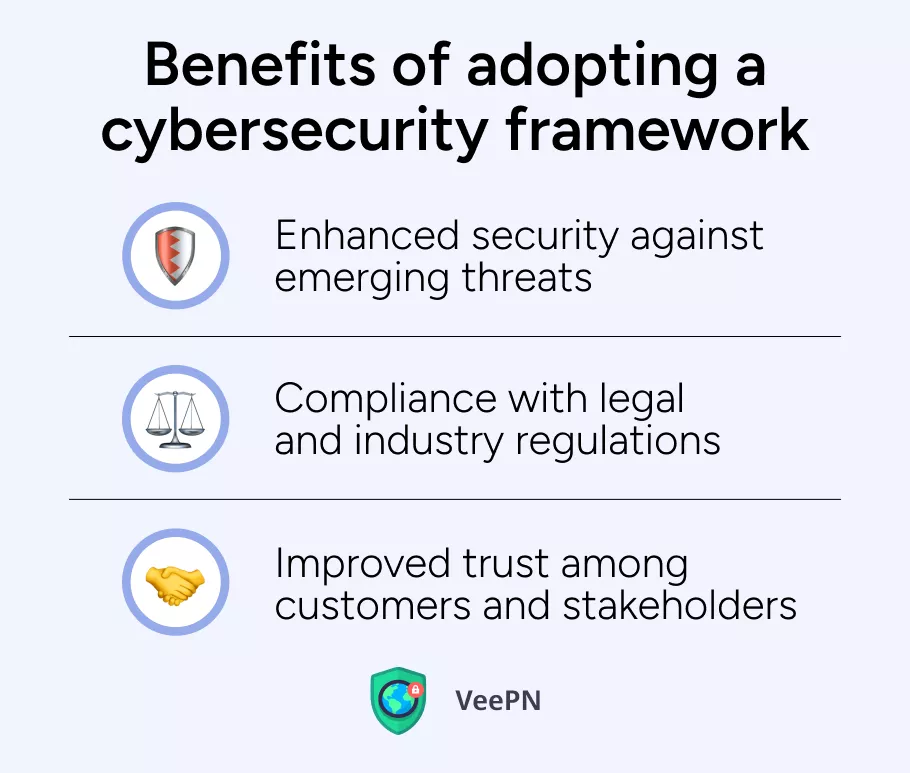
👍Enhanced security against emerging threats: Frameworks provide guidelines for implementing effective security controls and risk management.
👍Compliance with legal and industry regulations: Adhering to a recognized framework can help your business meet regulatory obligations and avoid penalties.
👍Improved trust among customers and stakeholders: A robust cybersecurity posture enhances an organization’s reputation, fostering trust among clients and partners.
It is hard to pick one in the above-mentioned cybersecurity frameworks list, but you probably still have to. Bear with us to learn how to choose the best cybersecurity framework for your company.
How to choose the top cybersecurity framework
Choosing the correct cybersecurity framework becomes essential to achieve organizational success. Your framework selection should include analysis of these specific aspects:
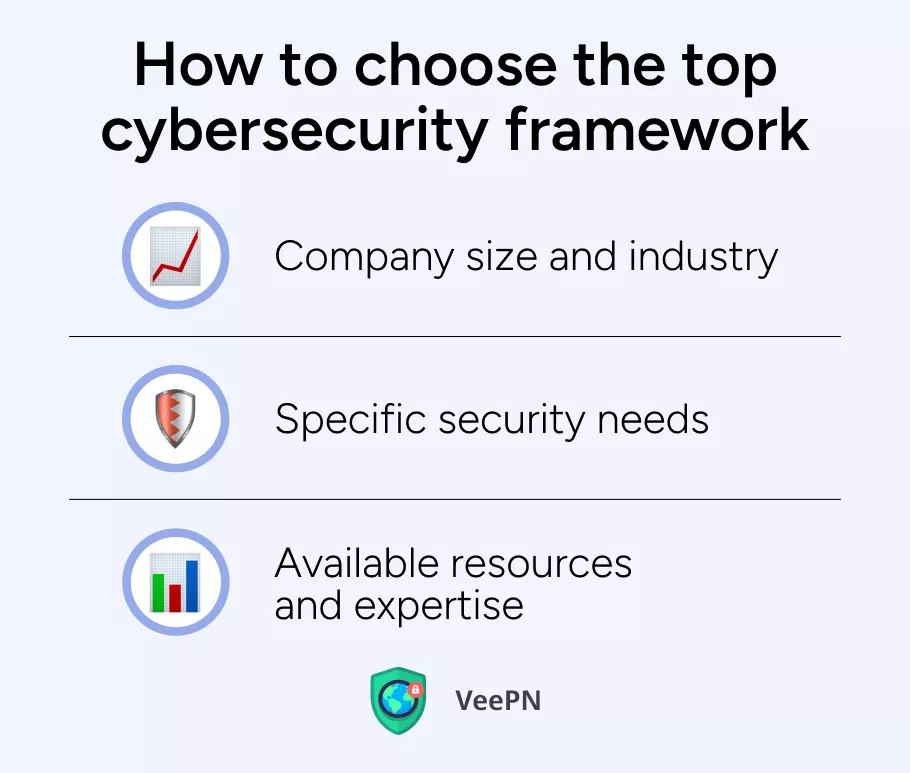
👍Business size and industry type. Depending on these factors, you should select a framework which matches your operations environment.
👍Special security needs. To discover an effective framework you must determine the special security needs of your organization.
👍Your team’s skill level and available resources. You should evaluate them to measure implementation feasibility as well as maintenance capabilities of the selected framework.
The use of a reliable VPN service offers an additional security measure beyond cybersecurity frameworks which protect organizations against cyber threats. Organizations achieve stronger security frameworks when they use dependable VPN services because these services both encrypt connections and hide IP addresses.
The extra privacy protection layer provides essential security for sensitive information exchange particularly when remote workers need to communicate. VPN technology provides protection against different online security threats including man-in-the-middle attacks together with eavesdropping attempts. Businesses that integrate a reliable VPN into their cybersecurity strategy will achieve stronger protection and maintain full confidentiality over their crucial data.
However, you should not use free VPN applications because they are unsafe due to their poor encryption standards and their practice of selling user data to third parties for advertising goals. VeePN can be your premium choice to provide secure data protection alongside a strict No Logs policy.
The role of VeePN in supporting cybersecurity frameworks
In the quest for robust cybersecurity, tools like VeePN can significantly enhance your defense mechanisms. Here’s how VeePN contributes to your cybersecurity framework:
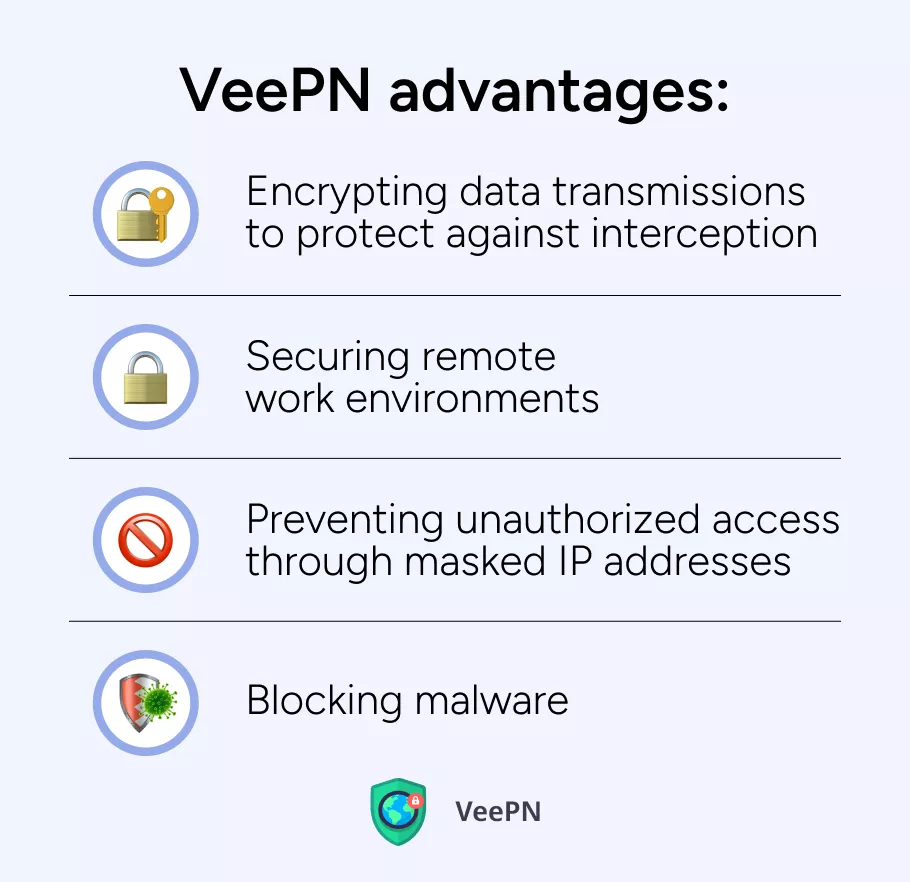
🛡️Encrypting data transmissions to protect against interception: VPNs help secure sensitive information in transit, making it more difficult for attackers to eavesdrop on communications.
🛡️Securing remote work environments: VeePN ensures that remote employees can safely access company resources without exposing their companies to risk, for example, when using public Wi-Fi networks.
🛡️Preventing unauthorized access through masked IP addresses: By hiding your actual IP addresses, VeePN helps prevent unauthorized users from targeting your network.
🛡️Blocking malware: Advanced VPN services often include features that block access to malicious websites and help safeguard against potential th reats.
Also, VeePN offers an antivirus software for Windows and Breach Alert tool that will automatically notify you when your sensitive data is compromised. Get VeePN today and enjoy a 30-day money-back guarantee!
FAQ
Organizations use a cybersecurity framework as a structured system of guidelines and best practices to manage their cybersecurity risks. Different organizations can select from various cybersecurity frameworks which include NIST Cybersecurity Framework, ISO/IEC 27001 and CIS Controls but each framework serves organizations with unique industry requirements and needs.
Beyond the common frameworks NIST and ISO/IEC 27001 and CIS Controls there are other frameworks. Here are a few examples:
- MITRE ATT&CK: MITRE ATT&CK maintains a knowledge database that teaches about adversary tactics, techniques and procedures (TTPs).
- Zero Trust Framework: The framework adopts the core philosophy of “never trust and always verify” by focusing on micro-segmentation techniques together with strict access rules.
- OWASP Framework: The framework supplies developers with directions to build secure web applications.
- GDPR Guidelines: Despite not having framework status it defines European Union data protection standards that affect security strategies throughout the region.
HIPAA Security Rule Framework: The healthcare industry depends on this framework to protect both its data security and patient privacy.
The adoption of cybersecurity frameworks becomes more feasible through VPN technology which ensures a secure network connectivity. The core features of VPNs match the requirements of frameworks such as encryption, access controls, and secure communication channels. A VPN use meets requirements for network traffic protection and prevention of unauthorized access while maintaining operational security. This article explores how VPNs play a significant part in developing powerful cybersecurity frameworks.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






