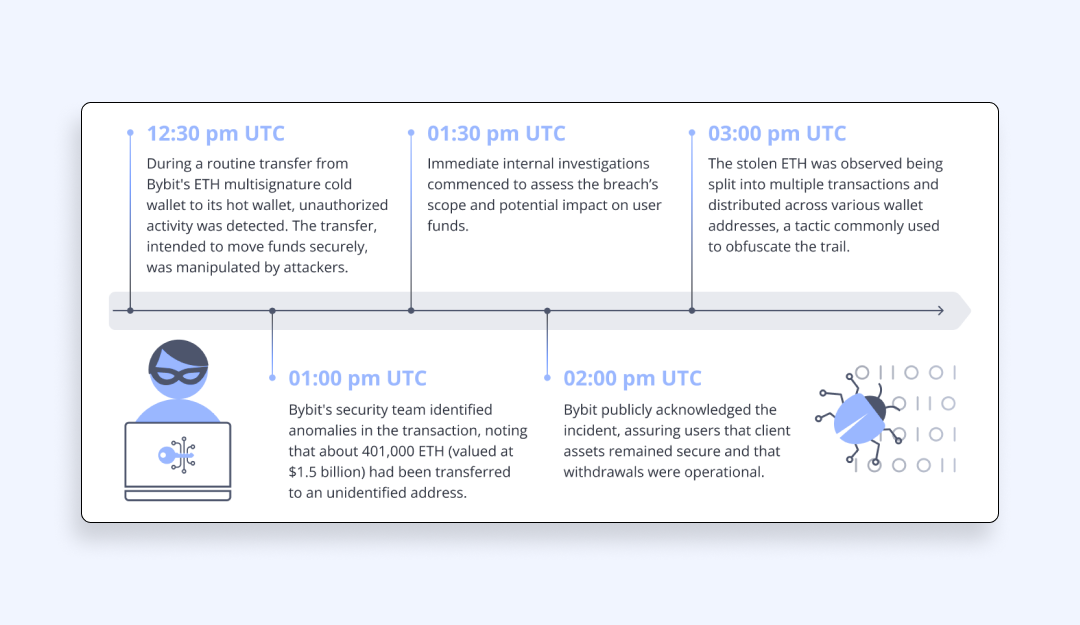
Bybit Hack: Traffic Interception and Address Swap Led to Massive Crypto Theft?
A routine transaction. A trusted platform. A moment of relief… until the money never arrives. The Bybit hack wasn’t a brute-force assault or a simple phishing scam. It was something far more insidious. Hackers didn’t steal funds outright; they stepped into the shadows between sender and receiver, manipulating transactions in real time. Like a puppet master pulling invisible strings, they intercepted payments, swapped wallet addresses, and redirected millions in crypto to their own accounts without triggering alarms.
By the time users realized what had happened, the funds had disappeared into the depths of blockchain anonymity. But how did hackers pull it off? And more importantly, could it happen again?

How the attack happened
The biggest crypto theft was executed in an intricate manner: from gaining access to wallets to distributing stolen assets across dozens of intermediaries and decentralized accounts. Let’s deconstruct the whole incident into separate phases to understand how the attackers got Bybit hacked:
1. Safe Wallet UI breach
The attackers chose the longest but the most effective way to gain access to the wallets. Instead of cracking the Bybit platform itself, the hackers aimed at its security system, a so-called Safe Wallet application. There are different theories how the attackers managed to sneak into the Safe without being noticed:

🧿Social engineering. A classic phishing or even a whaling attack could be the primary instrument the hackers used. By tricking a Bybit employee into leaking necessary information such as login credentials, the attackers got a completely legit access to the Safe. In such cases, fake emails impersonating the platform’s executives or messages containing a malicious link are the most common instruments. And since Bybit security officers are also humans, they could have been lured into such a trap.
🧿SSL stripping. Secure socket layer (SSL) stripping is a technique that prevents a victim’s browser from changing an insecure connection to a secure one, letting attackers intercept all the traffic. Hackers usually intrude via the Internet Service Provider (ISP) network to create a proxy server that replaces a safe one provided by ISP. As a result, an unsuspecting user routinely browses the web without realizing their connection is not safe, leaking their sensitive information.
🧿Man-in-the-middle attack. A man-in-the-middle (MITM) attack is a security breach where attackers secretly intercept and relay communications between two parties who believe they are directly communicating with each other. By positioning themselves in the communication pathway, the attackers can acquire sensitive information or alter the data being transmitted in real time. In the context of the Bybit hack, a MITM attack might have allowed attackers to intercept Bybit employees’ login credentials to access the Safe Wallet.
🧿DNS and BGP hijacking. DNS hijacking is an attack where an adversary diverts or manipulates DNS queries, causing users to be routed to fake or malicious websites instead of the legitimate ones. By tampering with the DNS infrastructure, the attackers might have intercepted traffic meant for a real Safe server which led them to access the app. As for BGP hijacking, it is an attack that exploits flaws in the Border Gateway Protocol to reroute Internet traffic through an attacker-controlled network. By manipulating routing announcements, attackers can intercept or alter data in transit, potentially leading to unauthorized access or theft of sensitive information such as login credentials necessary for accessing Safe Wallet.
As soon as the attackers have intruded the Safe, they changed some of the user interface (UI) commands with a JavaScript code to modify transactions in real time. In other words, the hackers “redirected” a command to transfer crypto from cold wallets. Instead of going to the receivers’ hot wallets, crypto went to wallets belonging to the hackers.
But since cryptocurrency is based on blockchain technology, and all the payments require initiation of a smart contract signing, the attackers had to overcome one more hurdle: smart contracts logic.
2. Changing smart contract logic
The main principle of smart contracts is to ensure that a transaction takes place without interference by third parties and under specific conditions. The attackers meddled with this logic by injecting a command to redirect the cryptocurrency to their wallets. In such a way, the system doesn’t recognize these transactions as unauthorized as they were embedded in the smart contracts. But the attackers had to make sure people making transactions were absolutely confident they were making a legit payment, which is why the hackers did one more trick.
3. Faking signing interface
The attackers changed the “background” of the signing process, or a confirmation that payment should be made. The Sygnia’s forensic investigation revealed that a malicious JavaScript code was injected in Safe Wallet via one of its Amazon Web Services (AWS) servers just before the attack. These changes to the Safe’s code let hackers be sure the victims would transfer the crypto believing the transaction is entirely safe and legitimate. Still, the attackers had to complete the last but also critical stage of their plan: withdraw the stolen money without drawing attention.
4. Stealing crypto
The attackers needed to leave no trace of the hack and launder stolen funds, which is why the stolen crypto was distributed among dozens of wallets and sent via third-party chains and decentralized wallets to avoid suspiciously large transfers done with one transaction. Take a look at the image below to see how virtual assets dispersed to cover the hackers’ tracks.
Overall, the entire attack was built upon the principle of faking and masking malicious actions, so they look like real ones and don’t trigger any Bybit security alarms. The attackers didn’t attempt to boil the ocean with a brute-force attack but found a subtle way that allowed them to act unnoticed.
Nevertheless, opinions about the attack and its consequences do differ among cybersecurity experts and crypto enthusiasts. Let’s put these opinions under a microscope.
What experts and the crypto community say
It is hard to deny that the biggest crypto heist in history made huge waves in the crypto industry and community. Opinions and speculations about the attack vary, from a strong scrutiny of the platform’s security measures to conspiracy theories.
To start with, we need to focus on what experts say. The same forensic investigation by Sygnia confirms that the Bybit’s own infrastructure was not compromised at all. Instead, the experts admit that the attackers found access backdoor through relatable services such as Safe Wallet and its AWS server.
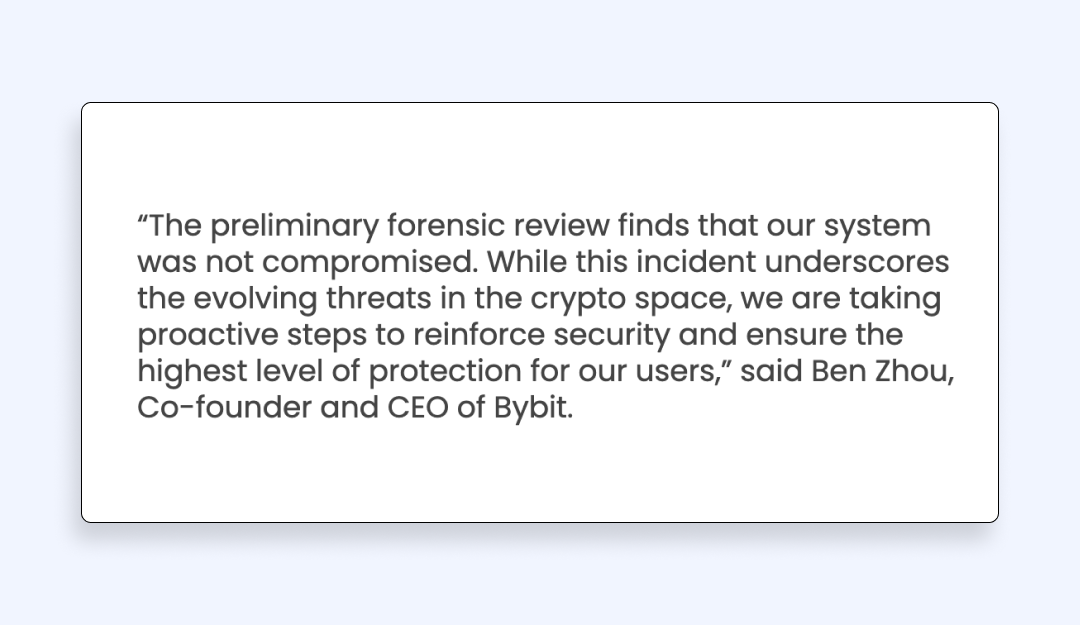
Such a conclusion does look way too obvious, but the experts just wanted to highlight the fact that Bybit’s own infrastructure is still safe and reliable. At the same time, the attack origin stems from the platform’s external infrastructure and human error that may happen one way or another.
Despite the fact that such an opinion definitely holds true, the crypto community has a different take on the Bybit hack. Cryptoenthusiasts blame the company for being too relentless with their risk management by considering extra caution unnecessary and expensive. Here are the main arguments the crypto community expresses regarding the attack:
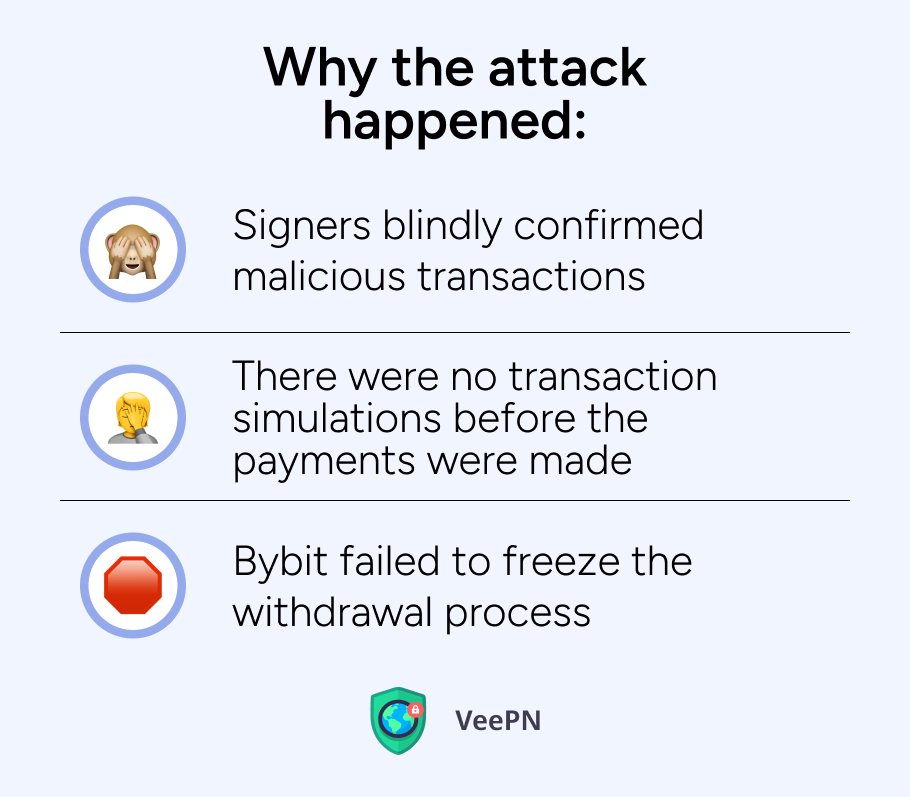
🤬Signers blindly confirmed malicious transactions. The platform obviously lacks an additional layer of crypto security that can protect multisig signers from being manipulated. Needless to say, there is no ultimate solution, but Bybit seems not to invest in such a kind of protection at all. Bybit generally relies on Safe Wallet only, which makes the entire security system vulnerable as there are no other defense walls hackers have to pass.
🤬There were no transaction simulations before the payments were made. The platform should have run a payment simulation to ensure the smart contract is safe and legitimate. Instead, the payments were made instantly, with malicious algorithms activated. On top of that, the platform seems to omit a smart contract’s security feature that notifies about altering transaction contacts. Had this feature been in place, the users would have recognized suspicious activity with their wallets.
🤬Bybit failed to freeze the withdrawal process. The platform just let a huge amount of money siphon from the chain, while they had nearly 24 hours to freeze all suspicious and large-sum transactions. Speaking of large-sum payments, we need to mention that the attackers cared enough to split stolen crypto into smaller chunks, so this claim isn’t really relevant. Anyway, Bybit missed the chance to save at least some part of the stolen crypto.
All in all, the crypto owners suggest that Bybit simply did not adopt stronger security guards to make such attacks impossible. Given that the investigation has revealed enough of the compromise details, the community’s complaints aren’t that hollow. Along with well-grounded criticism of the platform’s security practices, there are conspiracy theories that circulate within the crypto community.
What conspiracy theories and rumors say
The most prominent conspiracy theory speculates that Bybit simulated the attack to dump the market to favor the other cryptocurrencies the platform wants to benefit from. But even though the Ethereum value has dropped by 10%, such insinuation is definitely not worth the risk, both finance and reputation-wise.
In reality, a growth of withdrawals or exchanging Ethereum into other currencies was a natural panic typical of all big crypto market incidents. People are people, and we can’t really blame them for fearing for their savings after such a huge attack on one of the largest crypto exchanges.
Under these circumstances, the matter of your savings security arises no matter whether you share the above-mentioned opinions or not. You want your crypto to be safe, but how can you safeguard yourself? Keep on reading, as we’re going to equip you with a couple of actionable tips.
How to keep your crypto secure
With the following tips, you can reduce your risk of leaking your personal information and exposing your crypto wallets:
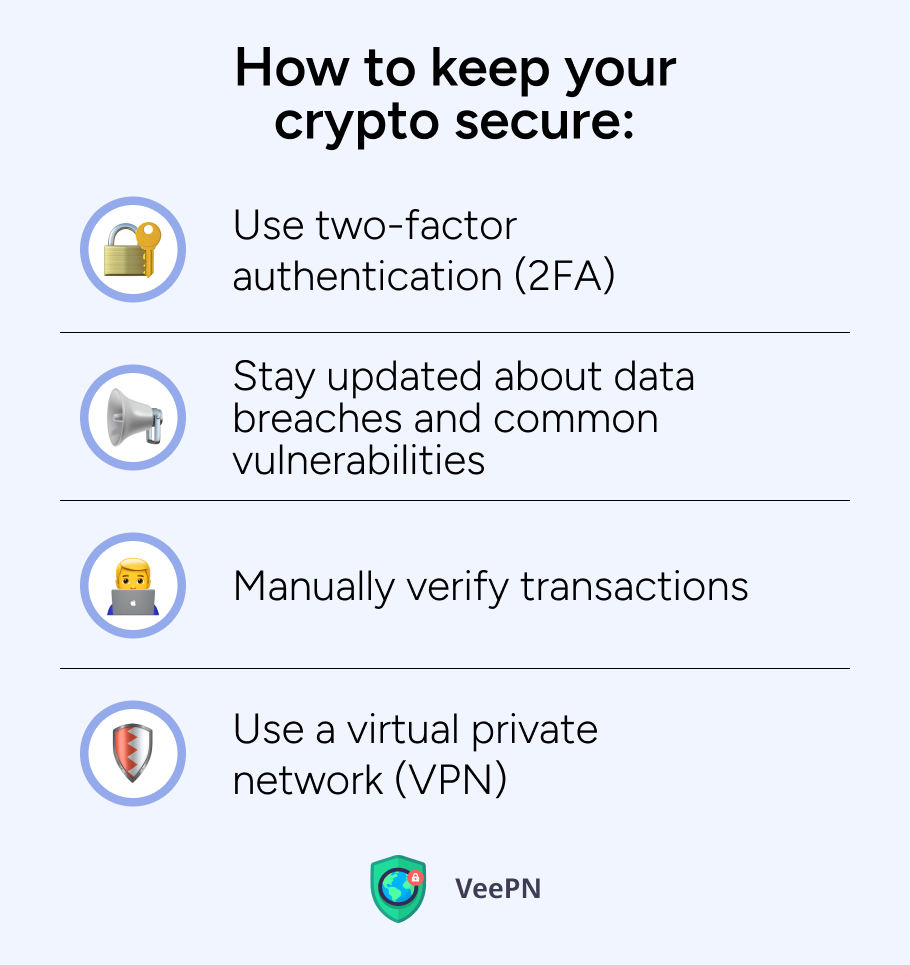
🔐Use two-factor authentication (2FA). Add as many authentication methods as possible to make access to your wallets extremely difficult for attackers. If applicable, use authentication with biometric data such as your fingerprints, face/retina recognition as this data is almost impossible to steal or fake.
🔐Stay updated about data breaches and common vulnerabilities. Crypto hacks happen from time to time, so it’s crucial not to miss the news about massive attacks to withdraw your funds on time or take preventive measures such as password update or adding extra layers of security.
🔐Manually verify transactions. Verify each transaction manually and double check the receiver information. Don’t take a leap of faith with even the most reliable and automated security tools used for safe crypto transactions.
🔐Use a virtual private network (VPN). By using a VPN app, you route all your Internet traffic through an encrypted tunnel invisible to others that leads to a remote server. In such a way, nobody can intercept your sensitive information and identify your real location as your IP address is masked. Using VPN is especially useful when you travel abroad or use public WiFi networks to make a fast trade. Although, we have to mention that using free VPNs isn’t safe as well. They commonly lack necessary encryption protocols and sell your personal information to third parties such as advertisers and marketing agencies.
To ensure your financial data is safe, consider trying VeePN, a premium VPN for crypto trading that offers a wide range of advanced security features. Bear with us to learn more about the advantages of VeePN that let you buy crypto securely anytime anywhere.
Why VeePN is a solid protection for your crypto savings
VeePN is a reliable solution for securing your crypto transactions because it offers such features and benefits as:

🛡️Military-grade encryption. VeePN uses AES 256-bit encryption that is considered the most secure encryption protocol so far. Even if hackers succeed in the interception of your traffic, they won’t be able to decrypt it.
🛡️Antivirus software. As a part of its security bundle, VeePN offers an antivirus app for Windows and Android, so you can be sure no spyware will crawl into your device unnoticed. With VeePN antivirus software, you can reduce your risks of leaking your wallet credentials via malicious apps.
🛡️Breach Alert. This feature instantly notifies you about leaks of your personal information such as login credentials, email addresses, and such, which gives you extra time to take preventive action and secure your crypto.
🛡️Device compatibility. VeePN is compatible with the majority of operating systems and platforms, so you can secure up to 10 devices with one subscription.
🛡️No Logs policy. We rigorously follow a strict policy of not collecting and selling your personal information to provide you with maximal confidence in our service and your online privacy.
Get VeePN today and enjoy a 30-day money-back guarantee!
FAQ
The platform announced that all crypto stolen will be refunded to users, so you just need to stay updated about the official statements from Bybit and follow their instructions regarding getting your refund.
Bybit suffered the biggest crypto theft in history, but the platform is likely to keep working as it used to. Beyond a doubt, Bybit is currently reconsidering its cybersecurity measures, but we highly recommend you safeguard yourself with VeePN — all-in-one cybersecurity app to ensure you can trade crypto at any platform without risks for your money and Internet privacy.
Yes, Bybit has the right to freeze accounts under certain conditions, such as suspected fraudulent or illicit activity, violations of its Terms of Service, or non-compliance with regulatory requirements. If an account is frozen, users typically need to contact Bybit’s support or compliance team to resolve any issues and potentially regain access. This measure is in place to ensure legal compliance and protect users from illegal activities.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan







