Zero Trust vs VPN: Can You Use Them Together?
With cyberattacks looming large, network security means a lot today. Luckily, there are quite a few ways to boost it. Specifically, the current security debate often revolves around choosing between VPNs and a zero trust approach. But what if you didn’t have to settle on one and combined both technologies? Would that work? Also, what’s all the fuss about zero trust and VPNs, overall? Let’s move along and find out.
What is zero trust?
First, let’s look into what each solution is about.
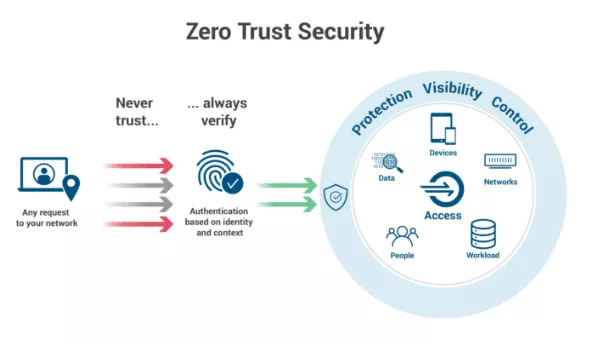
Guilty unless proven otherwise — this could be a slogan of the zero trust model. Zero trust is an approach to network security stating that no one inside or outside the network should be trusted unless their user identity is verified. Try to picture zero trust as this highly vigilant and a bit cynical pal always assuming that every attempt to access the network is a threat. So, as the name suggests, zero trust trusts no one. And this means each user or device has to get verified every time they try to connect, enforcing continuous verification despite any previous connections. That’s the deal.
Particularly, zero trust security model is all about:
- Thorough verification. Authenticating and authorizing access requests through numerous data points based on identity and context.
- Least privileged access. Applying strict access control so users can reach only the resources needed to accomplish a problem at hand.
- Assuming a breach. Segmenting accesses, verifying encryptions, and using threat detection tools to monitor the perimeter at all times.
Why did zero trust appear?
Largely because of business migration to the cloud and a growing number of cyberattacks. Besides, the modern mobile workforce has made network perimeters more fluid than ever. And this called for stronger defense models. So appeared the need to shift away from the “castle-and-moat” framework (where no one outside the network can access data inside the network, but everyone inside it can) to a zero trust model.
How are Zero Trust and SDP related?
As zero trust security is just a model — an architecture for today’s network, so to say — you’ll need a specific product or technology to bring this concept into reality. And here’s where a software-defined perimeter (SDP) comes in handy since SDPs help carry out many of the zero-trust principles on your network. SDP technology uses zero-trust capabilities to make network protection more solid. This way, not only are users unable to see resources concealed behind the perimeter, but they must also go through rigorous authentication processes to gain access to them.
How zero trust works
Having covered what zero trust is, let’s now talk about how it works. As we’ve mentioned before, zero trust is a security model in which we cast aside an idea of trusting anyone or anything based on where they are on a network. Instead, every single connection attempt is verified. So, until trust is established, unauthorized users or devices are denied access to resources, including critical systems.
What does zero trust verification process look like
Any user or device attempting to get hold of resources within a zero trust network must go through strict verification and authentication processes, regardless of whether they work remotely or in an office. Verification involves a human and machine element before establishing trust.
- Human verification involves checking that a user is who they claim to be through authentication and that they have permission to the requested resource.
Next, we need to verify they’re coming from a trusted device. And that’s when machine verification steps in:
- Verification of the machine or device a user’s connecting from cuts back the risk of a compromised machine having access to sensitive data.
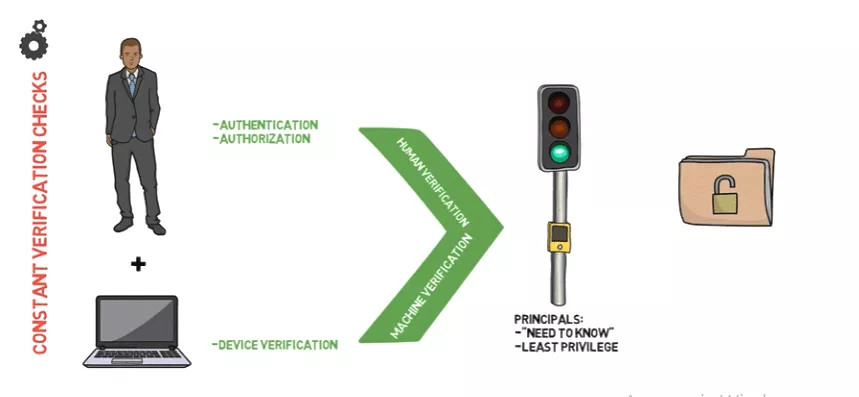
Once the verification process is over and the trust is established, a user can access a resource they’ve requested. And that’s basically it. Because a zero trust security is based on the concept of need-to-know, users get hold of only the resources they need at that time. And this is until a new request goes through the same process.
Zero Trust Network Access (ZTNA) — what is it?
Now let’s turn to specifics. While looking up zero trust, you may have come across zero trust network access as well. Basically, ZTNA is a subset of zero trust. It’s a technology that allows companies to implement a zero-trust strategy and extend it beyond the network. Unlike a VPN (more on it in a bit) that centers on the network, ZTNA takes it to the next level and provides application security that is independent of the network.
ZTNA is all about verifying the user and supporting concepts similar to privileged access management. It typically does so with multi-factor authentication to prevent credentials theft. Next, the technology validates the device, checking if it’s up to date and properly protected. And then it uses that info to grant the access (or not) while enforcing granular access controls for specific applications.
Although this technology is newer compared to VPNs, it has been actively gaining traction. Check out the example of MAN energy solutions, Germany-based manufacturing company, which used the ZTNA solution developed by a cloud security company Zscaler to make their apps dark to the internet.
Note: While some experts may use ZTNA and SDP interchangeably, it’s more common to consider them distinct solutions.
What is VPN?
A VPN, or virtual private network, refers to a network connection established through encrypted tunnels that protect users on public networks. With a VPN, remote workers can gain secure access to network resources as if they were in an office directly connected to the corporate network. VPNs authenticate users from outside the network before tunneling them inside, which can unintentionally grant broad network access. Only users logged into the VPN can see and access assets and gain visibility into the network activity.
Types of VPN
VPNs were primarily developed for business purposes. The goal was to create a secure way for employees to connect to their corporate network. The first VPN dates back to 1996. Then Microsoft employees created a peer-to-peer tunneling protocol (PPTN). But as more and more people started transferring their own data online, VPNs for personal use became popular because they allow broad access with added privacy.
And now we usually divide modern VPNs into two main types:
- Business VPNs are used for corporate purposes, being common in large-scale business environments that require secure remote access. They allow multiple users in various fixed locations to have access to corporate resources. As such, these VPNs are especially beneficial for remote workers.
- Commercial VPNs are mainly for personal use. They connect you to a secure remote server to access a private network. The added encryption ensures that security isn’t compromised. These VPNs hide your IP address and encrypt all your traffic. That said, you can regain your privacy online, access content that’s otherwise restricted to your regular connection, and protect your data from hackers and snoopers.
If you’re worried about your privacy and security online, consider an attractive VeePN offer. VeePN offers an impenetrable 256-bit encryption, a network of 2,500+ VPN servers in 89 locations, unlimited bandwidth and speed, extra protection features such as kill switch and a no log policy, and much more. Do not give hackers and snoopers a chance. Find out more here.
How VPN works
A business VPN works by encrypting tunnels between corporate networks and authorized end-user devices. It lets you into the internal network and enables access to network resources from anywhere you’re connected without exposing your identity to outsiders. After authenticating a device, the VPN client connects it to the VPN server, creating a secure and encrypted connection through an encrypted tunnel. The tunnel secures all traffic via encryption protocols like OpenVPN, IKEv2, and WireGuard.
Although both aim to strengthen corporate security, VPNs and zero trust networks take very different approaches to remote access security. While zero trust networks restrict access to all users at all times, VPNs give access at the network level, often resulting in broad network access once a user is authenticated. So if an attack occurs, the potential damage is significant.
How VPN, SDP, and zero trust can work together
When it comes to network security, zero trust solutions do appear to be more effective. Some vendors even claim ZTNA and SDPs will soon replace VPNs altogether. But…should they? The thing is that companies can benefit from using all three solutions at once, using the advantages and goals of each.
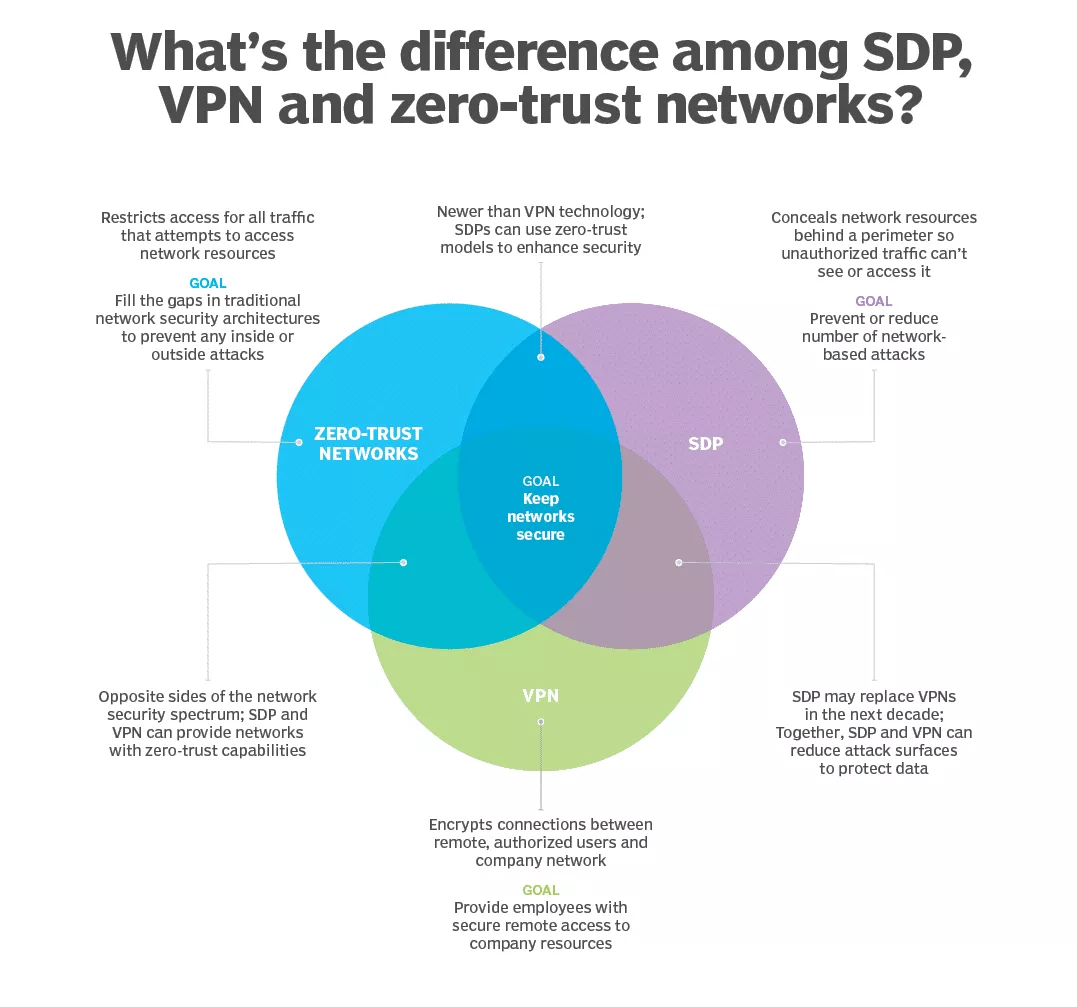
SDP and VPN
Let’s take a closer look at how these solutions can work together.
Instead of choosing between SDP and VPN, it can be a good idea to use these solutions at once. This way, SDP technology could close security gaps in VPN services. For example, a possibility of credential theft and increasing the size of the network’s attack surface.
Zero trust and SDP
With a growing threat of cyberattacks, companies can use both SDP and zero trust networks to provide stronger protection for modern networks. SDP technology can leverage zero trust capabilities to boost protection of network resources. That said, not only can’t users see or access network resources that lie behind a perimeter, they also have to undergo strict authentication processes before they can access those resources. And these precautions would minimize the possibility of cyberattacks.
VPN and Zero trust networks
Since VPNs provide secure remote access for users and zero trust is a holistic authentication approach, VPN can be used as an access method as part of zero trust. A company can combine VPNs and zero trust if it pairs a SDP and VPN together — that is, if it works with technology that implements a zero trust model. With zero trust models, SDPs create secure zones within the network and delineate a clear network perimeter. This way, zero-trust SDP will work with VPN to facilitate remote work and create a more robust security infrastructure.
Conclusions
To wrap up, because modern networks have many edges, it’s difficult to create a single protective boundary. So one may have a hard time choosing the sole solution to network security. A good thing, though, is that you don’t have to — it’s possible for companies to reap the benefits from several technologies like VPN and zero-trust SDP at once. There isn’t such a thing as too much security, anyway.
FAQ
What is Zero Trust Network Access vs VPN?
Zero trust networks ask for constant user and device verification and give user access only to resources needed to solve a problem at hand. VPNs, on the other hand, enable connectivity for authorized remote users and managed devices, giving them unrestricted access to network resources.
Is VPN or Zero Trust best for remote working security?
For better remote working security, companies can combine both solutions if they pair an SDP and VPN together.
Is ZTNA a VPN?
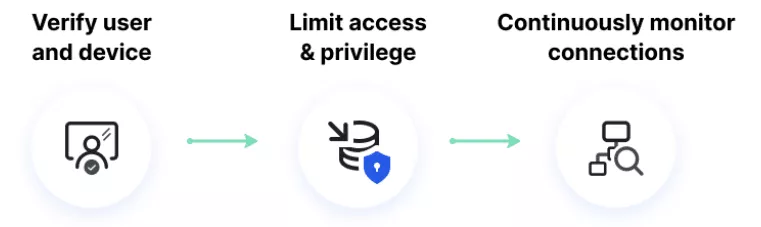
No, a Zero Trust Network Access (ZNTA) is a distinct network security solution, which is all about user and device authentication, limiting access and privilege, and continuous connections monitoring.
Is Zero Trust still relevant?
Yes, zero trust is a promising approach to modern network security which states that no one inside or outside the network should be trusted unless their identity is verified.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan






