What Is SMB and How to Use It Safely?
Do you know what lies behind the seamless flow of data from one device to another? Enter Server Message Block (SMB), the unsung hero of data transfer. This powerful protocol sets the rules for your device to send and receive information with ease. But what exactly is SMB and how does it work? Read on to find out.
What is SMB?
Let’s start with some basics. How does your computer send your data from one place to another? Thanks to a network protocol — a set of rules that tells your device how to transfer your data, say, from your computer to another server. SMB is one such protocol.
SMB stands for Server Message Block, and it’s a protocol used for sharing files, printers, and other resources on a network. In simpler terms, it’s a way for computers to communicate and share information with each other. It’s like a shared office cabinet where employees can access shared files and resources, as if they were stored in their own desk drawers.
Over the years, SMB has been used primarily to connect Windows computers. However, most other systems, like Linux and macOS, include client components for connecting to SMB resources, too.
When was SMB developed?
SMB is still a popular way to share files at work, although the protocol was created back in the 80s. Over time, new versions (also called “dialects”) were made to keep up with changes in how networks were used. Let’s talk more about them.
SMB protocol versions
The SMB protocol has come a long way since its introduction, with several updates that have made it better. Today, it’s more secure, scalable, and efficient. Here’s a quick look at some of the most important versions.
- SMB 1.0 (1984) was the original SMB protocol, introduced in the 1980s. It’s the most basic version and has since been replaced by more advanced dialects.
- CIFS (1996) or Common Internet File System, is a Microsoft-developed SMB dialect introduced in the 1990s to provide better compatibility with Windows systems. It added support for larger file sizes.
- SMB 2.0 (2006) was released with Windows Vista and Windows Server 2008. This version improved on the scalability and performance.
- SMB 2.1 (2008) was introduced with Windows Server 2008 R2 and Windows 7. It added support for larger read and write operations, among other things.
- SMB 3.0 (2012) focused on security and reliability, adding support for encrypted data transfers.
- SMB 3.02 (2013) made further improvements to security, including better support for secure negotiation and mutual authentication. It was introduced in Windows 8.1 and Windows Server 2012 R2.
- SMB 3.1.1 (2015) is the most recent version of SMB, released with Windows 10 and Windows Server 2016. It provides additional enhancements, such as improved support for persistent handles, symbolic links, AES-128 encryption, protection from man-in-the-middle attacks, and other features.
Note: Examples of operating systems that support different SMB dialects include:
Windows 7 and Windows Server 2008 R2 support SMBv1, SMBv2.1, and SMBv3.
Windows 8 and Windows Server 2012 support SMBv2.1 and SMBv3.
Windows 10 and Windows Server 2016 support SMBv3.
CIFS vs. SMB
Common Internet File System (CIFS) is often compared to SMB. So, let’s clear things up. CIFS is a form or dialect of the SMB protocol — it’s a particular implementation of SMB, created by Microsoft. However, the CIFS variant of SMB is rarely used these days. Under the covers, most modern storage systems no longer use CIFS, but SMB 2 or SMB 3.
How does SMB protocol work?
Now that we’re clear on the different variants of SMB, let’s take a look at how SMB makes all the sharing and file transfers happen. Here’s how it works.
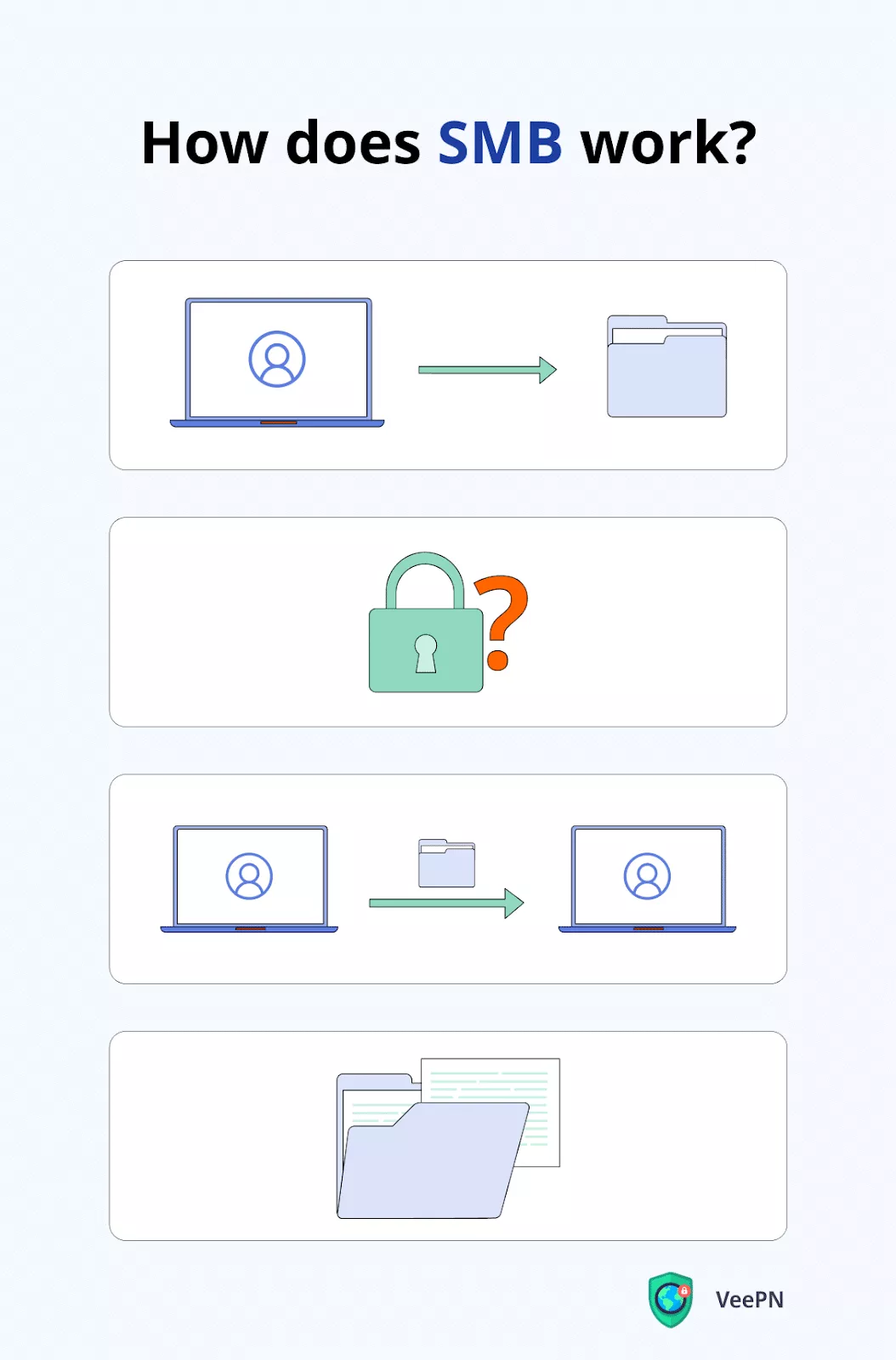
- A computer wants to access a shared resource on another computer, such as a file or a printer.
- The computer sends a request using the SMB protocol to the other computer, asking for access to the resource.
- The other computer receives the request and checks to see if the requesting computer has the necessary permissions to access the resource.
- If the requesting computer is authorized, the other computer sends the requested resource back to the requesting computer.
- The requesting computer receives the resource and can now use it as if it were stored locally.
In this way, SMB lets computers share files and resources in a seamless and transparent manner. This allows users to access the resources they need without having to worry about the technical details of the protocol.
What is SMB authentication?
Like any other connection, SMB protocol needs to have some security measures in place. Here’s when SMB authentication comes in. When you want to access a resource on a network using SMB, the network wants you to prove your identity and give it your username and password. If your credentials match with what the network has on record, you’re in! If not, sorry, access denied. The purpose of SMB authentication is to keep the network secure by only allowing authorized users to access its resources.
SMB protocol: When is it helpful?
Okay, we’ve handled SMB basics, so let’s explore when this handy protocol truly shines. SMB stands out among other protocols for several reasons:
- Compatibility — works with a wide range of operating systems, including Windows, macOS, and Linux. It’s a versatile option for sharing files and resources between different types of computers.
- Ease of use — designed to be user-friendly and straightforward, allowing users to access shared resources without needing to know the technical details of the protocol.
- Integration — integrates well with other technologies and protocols, such as Active Directory and Kerberos, making it a good choice for businesses with complex network environments.
- Performance — has been optimized for high-performance file sharing and has features like caching, compression, and encryption, which help to make file transfers faster and more secure.
- Security — has built-in security features, such as encryption and authentication, that help protect sensitive information when it’s being transferred over the network.
But hold on, it’s not all sunshine and rainbows with SMB. Let’s take a closer look at its downsides, too.
Is SMB safe? Some pitfalls of using a SMB protocol
Yes, despite its many advantages, SMB isn’t without its flaws and potential security risks. Some potential drawbacks of using SMB include:
Vulnerability
SMB has had several security vulnerabilities in the past, like:
- The EternalBlue 2017 computer exploit that led to the WannaCry ransomware attack. The attackers used the EternalBlue exploit to spread ransomware to unpatched systems worldwide. The attack spread rapidly due to the worm-like capabilities of the EternalBlue exploit, allowing it to spread from one infected system to others on the same network.
- SMBGhost, also known as CVE-2020-0796. Discovered in March 2020, it allowed attackers to take control of a vulnerable computer and execute harmful code on it, potentially giving them access to sensitive information and causing widespread damage.
- SMBLeed, also known as CVE-2021-24074. A vulnerability in the SMBv3 protocol discovered in November 2021. MBleed allowed attackers to read sensitive information from a vulnerable computer, such as passwords or encryption keys, which could be used for malicious purposes.
Although all past vulnerabilities have been addressed by Microsoft with security updates, there’s always a risk of new vulnerabilities being discovered.
Other pitfalls
Complexity
While the protocol is designed to be user-friendly, it can still be complex to set up and configure, especially for businesses with complex network environments.
Performance
SMB is optimized for high-performance file sharing. But it may not perform as well as other protocols in certain situations, for example, when transferring large files over slow or unreliable networks.
Lack of support
Some operating systems, such as Unix or BSD-based systems don’t support SMB, which can limit its usefulness in certain environments.
Licensing costs
Some SMB implementations, like the Microsoft version, may require a licensing fee, which can be a significant cost for businesses.
How to use SMB safely?
Though all we’ve covered above is true and does exist, don’t worry. Using SMB can be safe and secure. Just follow these simple guidelines to make sure you’re using it right.
1. Install updates promptly
It’s crucial to keep your software up-to-date. This means installing security updates as soon as they become available. By doing this, you’re patching up any holes that attackers could use to get into your system. And just a heads up, some updates may require a quick restart of your computer, so it’s best to do them when you’re not using your computer, like outside work hours.
2. Encrypt everything
Enable encryption for all SMB file transfers to protect the data from being intercepted or tampered with during transit.
3. Lock it down
Use firewalls to block unauthorized access to your SMB resources and to monitor and control incoming and outgoing traffic.
4. Limit access
Only grant access to SMB resources to those who need it and use strong authentication methods, such as password policies and multi-factor authentication, to secure access to them.
5. Keep an eye out
Regularly audit and monitor the use of SMB resources to detect any unusual or unauthorized access and to promptly address any security incidents.
6. Use a virtual private network (VPN)
While the most recent SMB version has AES-128 encryption to boost its security, most modern VPN providers offer even stronger AES-256 encryption and other built-in security features. Didn’t hear much about this solution? Here’s a quick VPN 101:
- A VPN is a cybersecurity software that acts like a secret tunnel for your Internet connection.
- It encrypts all your traffic, making it much harder for attackers to steal your information.
- Using a VPN can also hide your IP address and change your virtual location for added privacy.
Making sure to choose a reputable VPN provider is all it takes. And VeePN is one such service. Its robust encryption and Kill Switch will keep your data safe, while VeePN NetGuard will block infected pop-up ads, trackers, and potential phishing sites. The latter are often used to carry out massive network attacks like the ones mentioned before, by the way.
Secure up to 10 devices with only one subscription and use VeePN on computers, phones, and even routers to get complete protection. One account — endless (and risk-free) security!
FAQ: What is SMB?
SMB is a protocol used for sharing files, printers, and other resources between computers. It’s commonly used by businesses to allow employees to access shared resources, such as files and printers from their desktops or mobile devices. By enabling resource sharing, SMB can greatly improve collaboration and productivity for organizations of all sizes.
SMB stands for Server Message Block, a network communication protocol used for sharing files, printers, and other resources between computers.
Imagine you’re working at a small business, and you need to access important company files, like spreadsheets, presentations, and documents. Instead of emailing files back and forth or using a flash drive, you can easily access all these shared resources right from your computer. That’s what SMB is all about — it helps you share resources with your coworkers, making collaboration and work much easier. Find out more in our article.
- FTP is primarily used for transferring files between servers and client machines.
- SMB is used for sharing resources within a local network, such as files, printers, and serial ports.
- SMB offers additional features such as file locking, making it better suited for collaboration.
- FTP is simply a means of transferring files from one location to another, while SMB is more robust and feature-rich.
- FTP operates at the application layer of the OSI model and isn’t as secure as SMB, which operates at the session layer. In simple words, FTP is like a post office where data is sent in an unsecured manner, while SMB acts as a security guard to make sure the data being sent is protected and secure.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan








