How to Find Accounts Linked to Email Addresses (And Why You Should)
Every time you get a free trial, sign up, or tap a social login button to save time, you leave a breadcrumb of personal data. Years later, most of us have no idea who still holds those crumbs. But they might include your invoices, saved card numbers, or private messages.
From this article, you’ll know how to find accounts linked to email addresses for free on Google, Apple, Outlook, Yahoo, and your favorite social media platforms. Moreover, we’ll show that cleaning up that hidden digital footprint is simpler than you may think and why it is worth doing. Finally, you’ll discover how a trusted VPN like VeePN can boost your online security.

How to find accounts linked to your email: general steps
Before we dive into step-by-step guides for each provider, here’s a quick roadmap of what you basically need to do:
- Open the right Google account settings / Apple ID page, Microsoft Privacy dashboard / Yahoo Security tab.
- List every third-party app or social media account that still has account access.
- Revoke access for anything you do not use.
Apply the same procedure for any service that lets you sign in with Facebook, Instagram, X, or LinkedIn.
Now, let’s break that down by provider.
Gmail account
- Sign in and click your profile picture → Manage your Google Account.
- Choose Security → See details
- Select “Your third-party connections” to see accounts linked to email apps & services. There you’ll see all connections and find everything from streaming trials to old shopping carts.
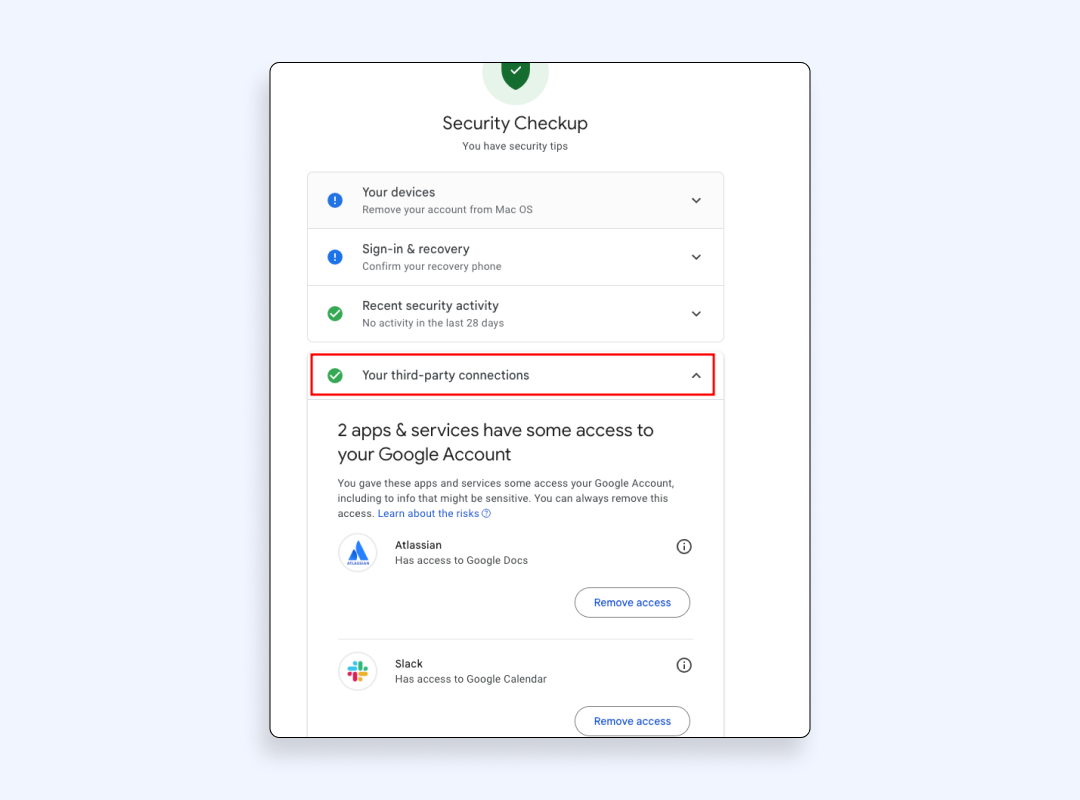
- Click the “ⓘ” icon next to any entry, read the shared data points (name, email, profile picture, etc.), and hit “Remove access” if you’re done with it.
While you’re here, consider enabling two-factor authentication and swapping any reused passwords for a strong password generated by a password manager. We explained why it’s important after the guide.
Apple ID (iCloud & Sign in with Apple)
- Open Settings on an iPhone
- Head to “Sign in with Apple”
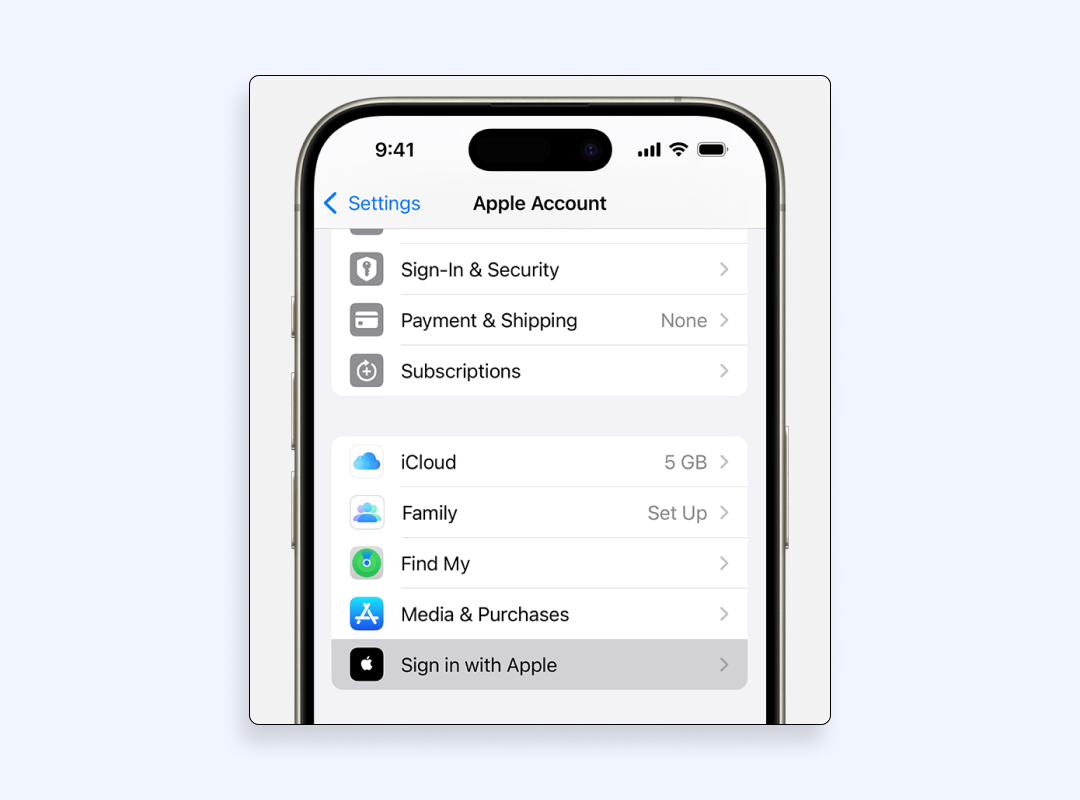
- Review each entry. Apple shows which third-party apps and websites rely on your Apple ID email relay.
- Select an app, then Stop Using Apple ID to cut the tie.
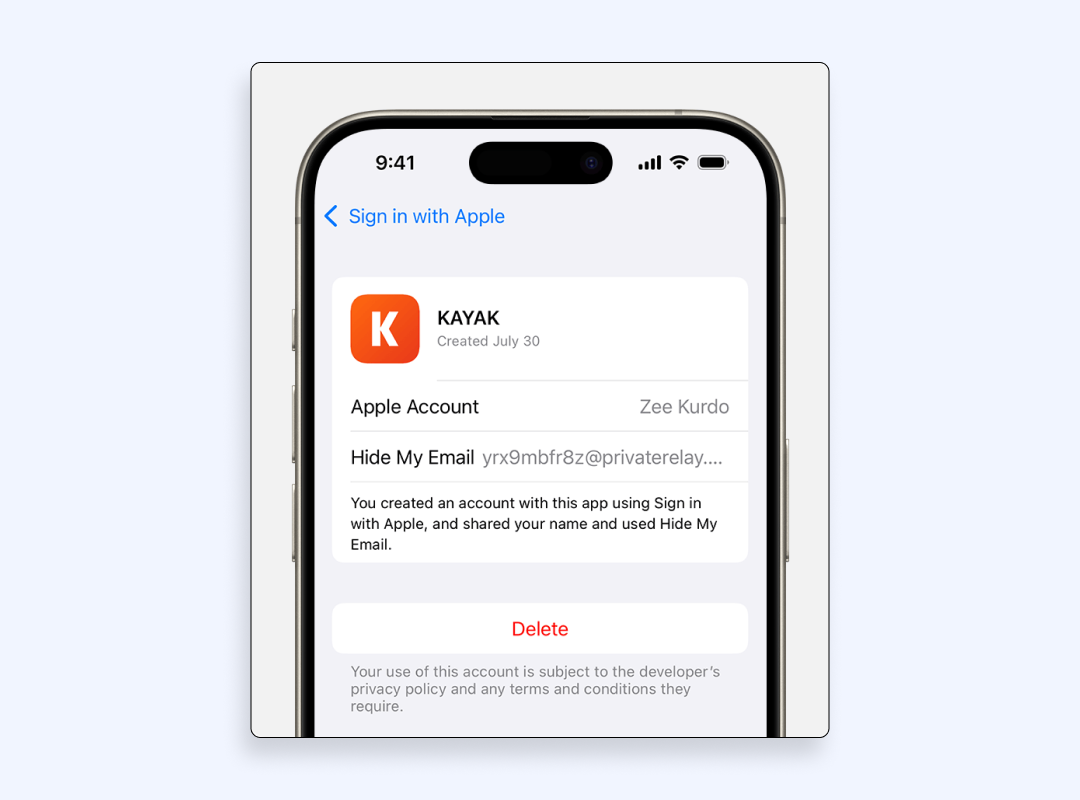
- Under Advanced, flip on “Hide My Email” to generate throw-away aliases for new sign-ups and shrink future clutter. (Apple encrypts every alias end-to-end).
Outlook / Microsoft
1. Log in to Outlook.com and click your avatar → My Microsoft account.
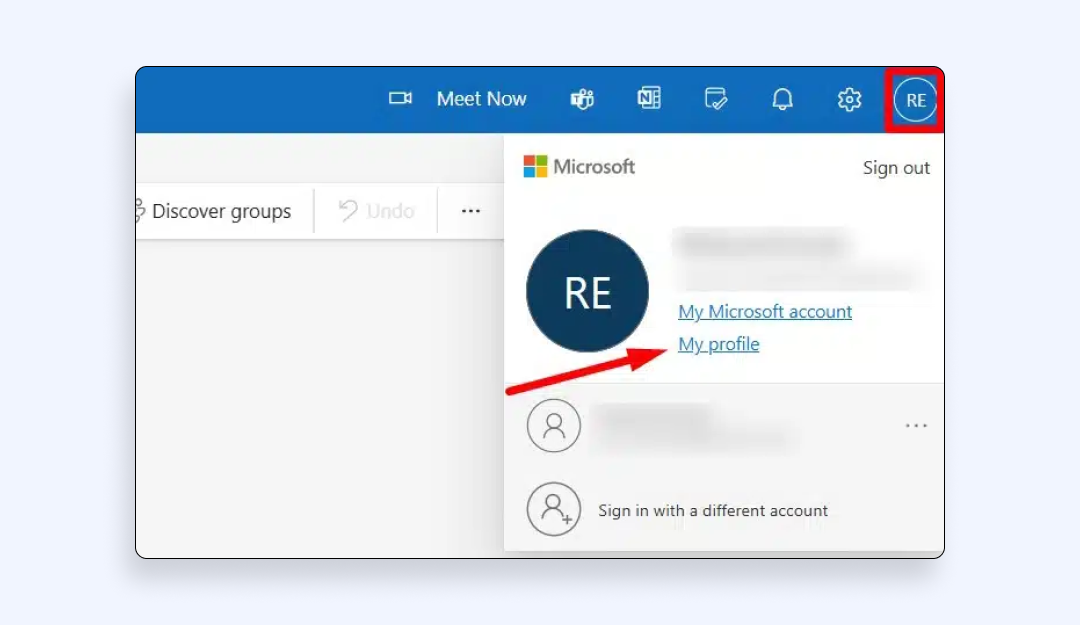
2. Choose Privacy → Enter your password again.
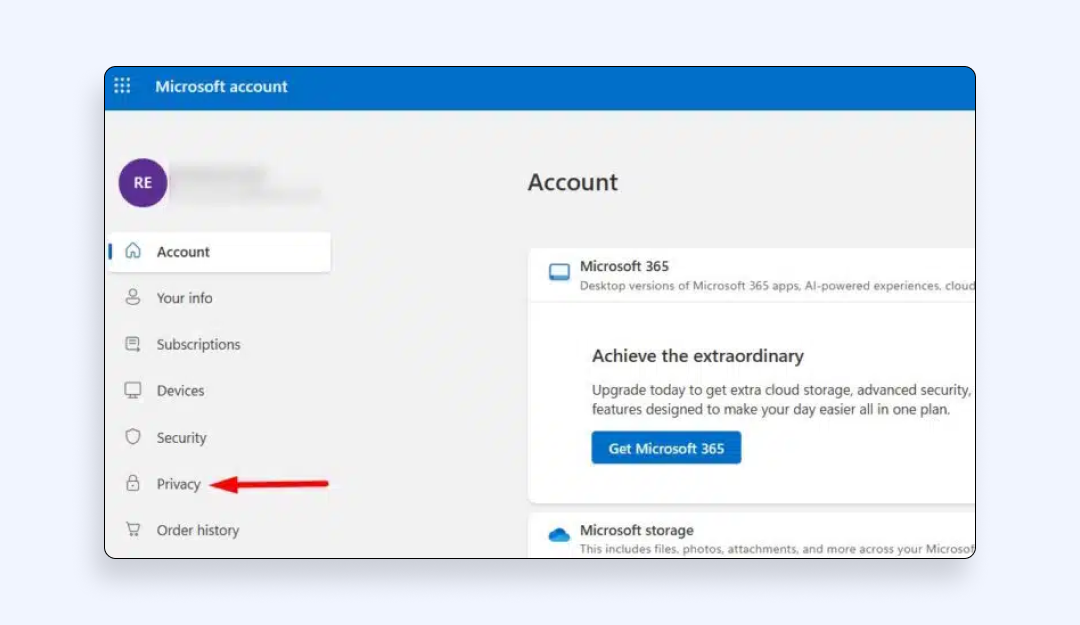
3. Click “App access”
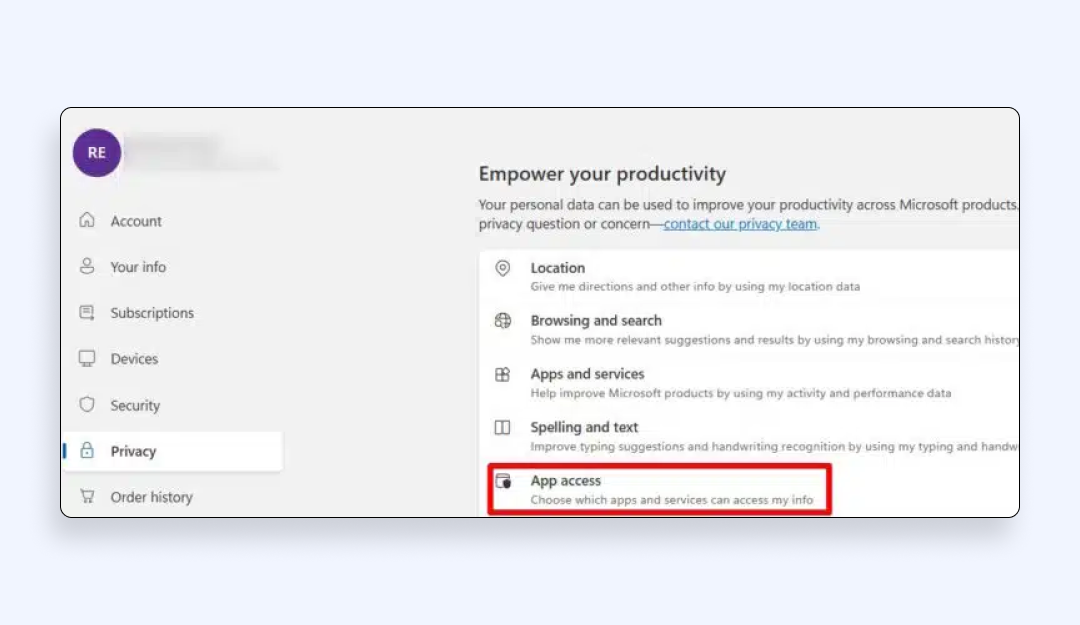
You now have a sortable list of accounts associated with email that rely on your Microsoft identity. Click an entry to remove permissions or delete the single account entirely.
Yahoo mail
- Hover over your name → Account info → Sign in again for security.
- Open Recent activity and scroll to View all connected apps.
- Remove anything you no longer use, especially old news sites or coupon apps that love selling user data.
Social logins (Facebook, X, Instagram, LinkedIn)
Even if you prefer email sign-ins, chances are that at least one social media platform hosts dormant logins:
- Facebook: Menu → Settings & privacy → Apps and websites.
- Instagram: ☰ More → Settings → Website permissions → Apps and websites.
- X / Twitter: More → Settings and privacy → Security and account access → Connected apps.
- LinkedIn: Profile icon → Settings & privacy → Data privacy → Permitted services.
Tap each old integration and hit “Remove”, especially if it looks like a fake social media profile or a long-dead quiz app.
Having talked about how you can find and delete your logins via emails, let’s outline the risks of leaving them untouched.
Threats of leaving abandoned logins via your emails
Leaving abandoned accounts alive might feel harmless, but there are things to worry about:

Exposure to data breaches
Every extra record in a vendor’s database is one more lottery ticket in the breach jackpot. Criminals piece together stolen data points, like your name, email, birth date, and even your profile pictures, to open credit lines or launch personalized phishing.
For instance, a major data leak has exposed over 184 million login credentials from known platforms such as Google, Facebook, Instagram, Snapchat and Microsoft. Because the database is public, millions of users found themselves exposing their bank account details , healthcare info and government data to con artists.
Weak or reused passwords
Old accounts often rely on passwords you set years ago, before password generators were strong enough. If that password shows up in a breach list and has been used on multiple websites, bots will get to your bank account, streaming services, and cloud storage within minutes.
Unwanted tracking and spam
Dormant logins still feed analytics trackers, ad networks, and data brokers. That may result in ads, inbox spam, and a bigger surface for email spoofing dangers.
Lost subscriptions and phantom charges
Some “free trials” may silently be converted to paid tiers, which is one of the popular scam techniques. Deleting outdated invoices helps you discover and cancel these hidden charges before your next billing date.
With that said, let’s have a look at how you can protect your online accounts.
Smart ways to manage and secure your online accounts
A tidy inbox is not enough for your safety. Lock in long-term safety with these practices:
Use a password manager
One click creates truly unique passwords and autofills them on any website or app. You won’t have any repeats in passwords for different platforms.
Enable 2FA everywhere
Whether via app code, hardware key, or SMS, enable two-factor authentication to verify it’s you before every sign-in.
Schedule quarterly audits
Set a reminder to search your inbox for emails like “Welcome,” “Receipt,” or “Verify your account.” These messages help you find accounts related to email, so you can review which services you’ve signed up for and decide whether to keep or delete those accounts entirely.
Mask throw-away emails
Tools like Apple’s Hide My Email or dedicated alias services let you send anonymous email and keep junk out of your main inbox.
Browse through a VPN
A VPN encrypts your traffic to prevent snoops from mapping your cleanup spree and stops ISPs from selling your metadata.
But don’t use free VPNs, because many of them promise online privacy but often embed trackers, inject ads, or log your traffic to sell it later. That defeats the whole purpose of hiding or email masking. Using free VPNs may even expose you to man-in-the-middle attacks, as many of such providers offer weak encryption. Paying a few dollars a month for proven security is cheaper than recovering from identity fraud. That’s why consider using a reliable provider like VeePN instead.
How VeePN strengthens your email privacy
Here is what VeePN brings to the table:
- AES-256 encryption. This gold standard of encryption that locks down every password reset link and inbox session.
- Automatic Kill Switch. If your VPN connection drops or glitches, your real IP address won’t leak while editing sensitive settings.
- Anti-tracking NetGuard. This VeePN feature blocks ads, malware domains, and pixel trackers that map online accounts’ activity.
- 2,500+ servers in 89 countries. You can jump past regional blocks to access other services that only work abroad.
- Multi-platform apps. Secure up to 10 devices at once on Windows, macOS, iOS, Android, Linux, and browser extensions.
- Double VPN routing. You can chain two servers for extra cover when managing high-value accounts like crypto wallets.
- No Logs policy. VeePN never stores your browsing or login metadata.
Try VeePN without risk with a 30-day money-back guarantee and see how effortless true privacy feels.
FAQ
Start in your inbox: search “Welcome,” “Verify,” or “Receipt” to spot sign-ups. Cross-check that list against Google, Apple, Microsoft, and Yahoo dashboards to find accounts connected to emails you forgot about. Dive into social media settings as well to find accounts associated with emails created through one-tap logins. Close anything you no longer need.
Read the steps on how to do it in the article.
Scan purchase receipts, newsletters, and password-reset messages in your email first. Then, open your browser’s password vault to find profiles by email in one list. If you use Gmail, Google’s “Third-party apps” panel shows every service with accounts associated with Gmail. There, you can remove this access with a click. Read detailed guides in the article.
Use HaveIBeenPwned or other breach tools to check accounts linked to emails that have been leaked. Then, follow up in each provider’s security dashboard to confirm what apps you still use and need and which logins with your emails can be removed. Find full instructions and privacy tips in this article.
VeePN is freedom
Download VeePN Client for All Platforms
Enjoy a smooth VPN experience anywhere, anytime. No matter the device you have — phone or laptop, tablet or router — VeePN’s next-gen data protection and ultra-fast speeds will cover all of them.
Download for PC Download for Mac IOS and Android App
IOS and Android App
Want secure browsing while reading this?
See the difference for yourself - Try VeePN PRO for 3-days for $1, no risk, no pressure.
Start My $1 TrialThen VeePN PRO 1-year plan







